The best VPN service 2025

Welcome to the TechRadar best VPN buying guide. Our aim is to give you the information to buy the best VPN for your needs as quickly as possible.
With that in mind, NordVPN is the best VPN for most people, and we'll explain why just below. Surfshark (don't miss its 7-day free trial) and Proton VPN are also excellent. You're unlikely to go wrong with any of them. We know this because we regularly perform in-depth and rigorous VPN testing, which you can also read about further down.
We've been writing about and reviewing VPNs at TechRadar for over 11 years, and we know more about them than any other website. When it comes to guiding our readers to the right choice, we think that's worth something.
5 best VPNs: a quick overview
1. NordVPN – The best VPN overall ($3.39 $2.99 per month)
NordVPN came out on top in our latest round of VPN tests. It is our top pick as the best VPN for most people. We’re confident that virtually anyone can sign up for NordVPN and get what they need. It’s easy to use, it's very secure, fast enough for downloads and gaming, and offers flawless streaming service unblocking.
NordVPN is also good value for money with the price down to a healthy $2.99 per month plus tax if you sign up for two years (though it needs to be paid upfront). You can try it before committing by using the 30-day money-back guarantee.
Read our full NordVPN debrief below ▼
2. Surfshark – get the 7-day free trial
Surfshark beats NordVPN on price and speed – although both services are very fast and we doubt you'll notice the difference. Surfshark is not quite as good at unblocking streaming services and it doesn't have servers in as many different countries as NordVPN. Surfshark has excellent apps but, again, a slightly lower score than NordVPN in our malware, phishing, and ad-blocking tests.
ExpressVPN (below) edges Surfshark on security, too. Its two-year Starter plan (paid upfront) is $1.99 per month plus tax but we rate the Surfshark One plan ($2.29) as the best value price plan. Both come with a 7-day free trial. That's something that none of the other top VPN services offer.
Read our full Surfshark debrief below ▼
3. Proton VPN – The best VPN for privacy ($3.59 $2.99 per month)
If you want extreme privacy above all else, choose Proton. Based in Switzerland, this extremely capable VPN offers good speeds and has servers in 126 countries around the world – including across Africa and Asia where other providers tend to struggle – which makes it excellent for streaming and torrenting too.
It's privacy that's the big differentiator for Proton VPN, though, with extra features and tools for ensuring your internet traffic remains under wraps no matter where you are in the world and with almost absolute certainty. Proton VPN's recent app improvements make it a good choice for beginners, with explainer pop-ups for most functions. It's also a terrific time to get Proton with the price still discounted by around $0.50 per month.
Read our full Proton VPN debrief below ▼
4. ExpressVPN – The best VPN for Windows ($3.49 per month)
ExpressVPN is the easiest VPN to use on our list, making it a great option for anyone less tech-savvy. It’s also one of the most secure VPN we’ve tested, with good features to keep you safe online. Like NordVPN and Surfshark, it's very fast, particularly on Windows thanks to the Lightway Turbo protocol which delivers excellent performance at connections over any distance.
ExpressVPN is still the most expensive of our recommended VPN services, even after switching to a three-tier structure. Subscriptions now start at a more competitive $3.49 per month on the two-year plan which puts it on a par with NordVPN and others for value. As with most VPNs, there’s a 30-day money-back guarantee.
Read our full ExpressVPN debrief below ▼
5. PrivadoVPN Free – The best free VPN
We don’t advise using a free VPN for most purposes but, if you do need one – as a one-off, say – PrivadoVPN’s free plan is the best of the free services we’ve tested. Its speed rivals the services above and it'll keep your data private and secure but you don't get the same breadth of features or unlimited usage.
There are only 13 server locations and a 10 GB data cap, so it isn’t suitable for heavy streaming or downloading lots of files. If you need those functions, it’s worth paying for NordVPN or Surfshark. Of the free options, though, it’s the best. (You'll find the 'Try free plan' button in light grey below PrivadoVPN's paid plan.) If you do like PrivadoVPN, then it's only $30 for 2 years if you want the full version. That makes it less than half the price of anything of the other top 5.
Read our full PrivadoVPN debrief below ▼
The best VPN services 2025


1. NordVPN
For streaming, security and everyday use, this is the best VPN you can buy.
NordVPN is more than enough for most people: it's fast, reasonably price, and relatively easy to use – but with plenty of tools for even the biggest technophiles.
There are some niche cases where you may be better off with another service (ProtonVPN is a better choice for countries with extreme censorship, for example) but, if you just want a VPN for streaming your favorite shows, gaming, and keeping safe on public WiFi, NordVPN is the best VPN for the job.
At $2.99 per month it's slightly more expensive than the likes of Surfshark, but the experience pays for itself. Take a look below for more information about NordVPN.
Read more about NordVPN ▼
Ease of Use ★★★★★
Why you can trust TechRadar
Getting started with NordVPN is easy thanks to the onboarding wizard that springs to life when you fire up the Mac or Windows version for the very first time. It'll walk you through Nord's features and make sure you understand what's going on.
NordVPN has users well covered for apps, and we love the browser extension too which still includes features like split-tunnelling and the kill switch. It also has location spoofing which means you can access international versions of any website you come across – handy for checking for the cheapest prices.
We were delighted to see the May 2025 addition of a NordVPN Linux app complete with a GUI and even more pleased to see the company make the interface app open source in October 2025 too.
Any Fire Stick VPN users should also take note that NordVPN has been the first VPN provider to ready an app for the September 2025 launched Fire Stick Select and its new Vega OS.
Read more details on NordVPN's compatibility and usability in the full review.
Streaming ★★★★★
We rate NordVPN as the best streaming VPN that money can buy. It boasts over 7600 ultra-fast servers covering over 127 countries, all of which are optimised for streaming.
It unblocks all major streaming services – including international Netflix libraries, Amazon Prime Video, and Disney Plus – as well as a host of other regional streamers such as BBC iPlayer, 9Now, SBS On Demand, ITVX, Sling, FuboTV, Max, and many, many more. In fact, it's not often we find a streaming service that NordVPN can't get around the back of.
Speeds are easily enough to handle 4K HDR video. The only streaming-related caveat is that NordVPN isn't the best torrenting VPN. That accolade goes to ExpressVPN. That's because there are only a handful of NordVPN servers optimised for P2P use.
NordVPN also has a special, if slightly niche, treat on the streaming front with its Meshnet private network feature which had been scheduled for shutdown, in August 2025, until user uproar saw it saved on just one month later. We asked NordVPN what happened here along with everything you've always wanted to know about NordVPN.
Meshnet can be used for remote desktop access and file sharing and that includes using it to turn your home computer into a media server. So, you could use Plex to set up your media server and then access it remotely on all kinds of devices over Meshnet. That's not something you get with other VPNs.
Read more details on NordVPN unblocking in the full review.
Privacy & Security ★★★★★
NordVPN comes with cutting-edge security and privacy features, including its recently launched NordWhisper protocol for VPN obfuscation and censorship avoidance. It also runs both OpenVPN and its own proprietary WireGuard-based Nordlynx protocol with super-secure, recently audited, zero-trust AES-256 encryption, meaning you can be confident that nobody has access to your data but you.
If someone ever did manage to pilfer it, it would take them millions of years to crack the encryption, particularly as NordVPN's quantum-safe encryption is theoretically future-proofed. In fact, NordVPN extended its post-quantum encryption (PQE) in May 2025 across all of its apps, making the service theoretically invulnerable to so-called "store now, decrypt later (SNDL)" attacks, which await the availability of quantum computers and their increased code-cracking powers.
All of NordVPN's mettle was put to the test in a large-scale security audit in December 2025, which the company passed with flying colors.
NordVPN has a strict no-logs policy – which was successfully audited for the fifth time in February 2025 – meaning that not even the company itself has a record of your browsing data.
It's also legally headquartered in Panama – a country with strong data protection laws – meaning that it would be very difficult for any third parties to have any successful claims to NordVPN's customer base, even if it did log anything significant.
Finally, there's also a kill switch for further assurances and DNS leak protection to prevent your ISP from getting even a whiff of what you're up to.
NordVPN's Threat Protection Pro feature set (available on the NordVPN Plus plan and above) includes anti-malware and anti-phising security for file downloads as well as while browsing. It extended its protection to customer email inboxes too, in December 2025, for those using the Windows or Mac apps.
The company also added a crypto wallet checker, in September, 2025, to scan for fraudulent addresses, after $1.5 billion was stolen in scams, in Q1 2025 alone. It also added session hijacking protection which aims to keep your stolen cookies off the dark web.
And if you think that the security provided by your antivirus is enough, then you might want to take a look at NordVPN's October 2025 Times Square demonstration of just how exposed we are online without a VPN.
Read more details on NordVPN's privacy and security in the full review.
Speed & Performance ★★★★½
The NordLynx proprietary protocol performed brilliantly in our speed tests. It clocked consistent speeds upwards of 1200 Mbps in servers to the UK, dropping to more like 900 Mbps when heading across the Atlantic to the US. The latter of these is where many other VPNs struggle to perform. That's worth considering given that plenty of people will be looking to access streaming services and other content across The Pond.
OpenVPN speeds are a little slower, at more like 900 Mbps both locally and long distance, but we'd rate NordVPN as one of the very fastest out there on this protocol, along with ExpressVPN.
NordVPN has a great deal of pride in its server network and has recently looked to change the conversation from server count to server quality. From our results of putting its network performance to the test, NordVPN has a good point.
In fact, NordVPN has just undergone a third-party audit of its performance speed and connection time, as well as its functionality and security. West Coast Labs determined that every was satisfactory.
Read more details on NordVPN speed and performance in the full review.
NordVPN price plan comparison
There are four NordVPN price plans to choose from if you're based in the US – three if you live anywhere else in the world.
NordVPN Basic is just the VPN software. It's available everywhere. If you want to add some anti-virus functionality (Nord Threat Protection Pro), then go for NordVPN Plus. For a password manager (NordPass), cloud storage (NordLocker), and up to $5000 of cyber insurance on top, go for NordVPN Ultimate.
NordVPN Ultimate also recently extended its ID theft recovery insurance to UK Ultimate users up to a value of £5000 – useful in light of the recent UK big retail cyber attacks.
NordVPN has a slightly different pricing structure in the US with its NordProtect program which includes up to $1M in identity theft insurance and $100K in cyber extortion insurance. There's confidence for you!
That's a lot more fraud protection US customers but, then, apparently, Brits are better than Americans at spotting phishing scams, so perhaps that's a good idea.
So, instead of the Plus and Ultimate tiers, the USA gets Basic, Plus, Complete, and Prime.
For our money, the Basic plan is the best value, but if you really need the extras on offer in Plus, Complete, Ultimate, or Prime, then go for it. Each plan type comes with a different possible contract length: 1-month, 1-year, or 2-year.
Do remember that you need to pay the full amount upfront, though, and that, along with Surfshark, NordVPN adds local tax at checkout. That means that its quoted monthly prices might well be a little higher depending on where you live. In some parts of the United States, that could mean another 8% or so added on. For those in the UK, it's a full 20% extra.
The other major warning – and this is true for most VPNs – do not let your subscription auto-renew, or you'll end up with a pretty sharp price hike. Currently, NordVPN auto-renews for $139, for just one year, for those on the Basic plan.
That's around 50% more than you might have paid for the original 2-year plan you subscribed to. In fact, a US law firm is taking NordVPN to Court over what it has deemed to be "deceptive" auto-renewal pricing. Our advice is to make sure you switch off auto-renew in your subscription settings as soon as you sign up and install.
Whichever subscription you choose, though, you get 30 days to change your mind and ask for a full refund.
Below is a comparison table of the NordVPN plans and what each one offers. Just be careful not to fall for a fake NordVPN ad scam when you come to buy.
| Header Cell - Column 0 | |||||
|---|---|---|---|---|---|
1-month plan price | $12.99/month | $13.99/month | $14.99/month | £12.29/month | $17.99/month |
1-year plan price | $4.59/month | $5.49/month | $6.49/month | £5.99/month | $8.49/month |
2-year plan price | $2.99/month | $3.89/month | $4.89/month | £4.79/month | $6.89/month |
VPN | ✅ | ✅ | ✅ | ✅ | ✅ |
Threat protection Pro | ❌ | ✅ | ✅ | ✅ | ✅ |
Password manager | ❌ | ✅ | ✅ | ✅ | ✅ |
1TB cloud storage | ❌ | ❌ | ✅ | ✅ | ✅ |
Cyber Insurance | ❌ | ❌ | ❌ | ✅ | ✅ (NordProtect) |
Surfshark – the best low cost VPN
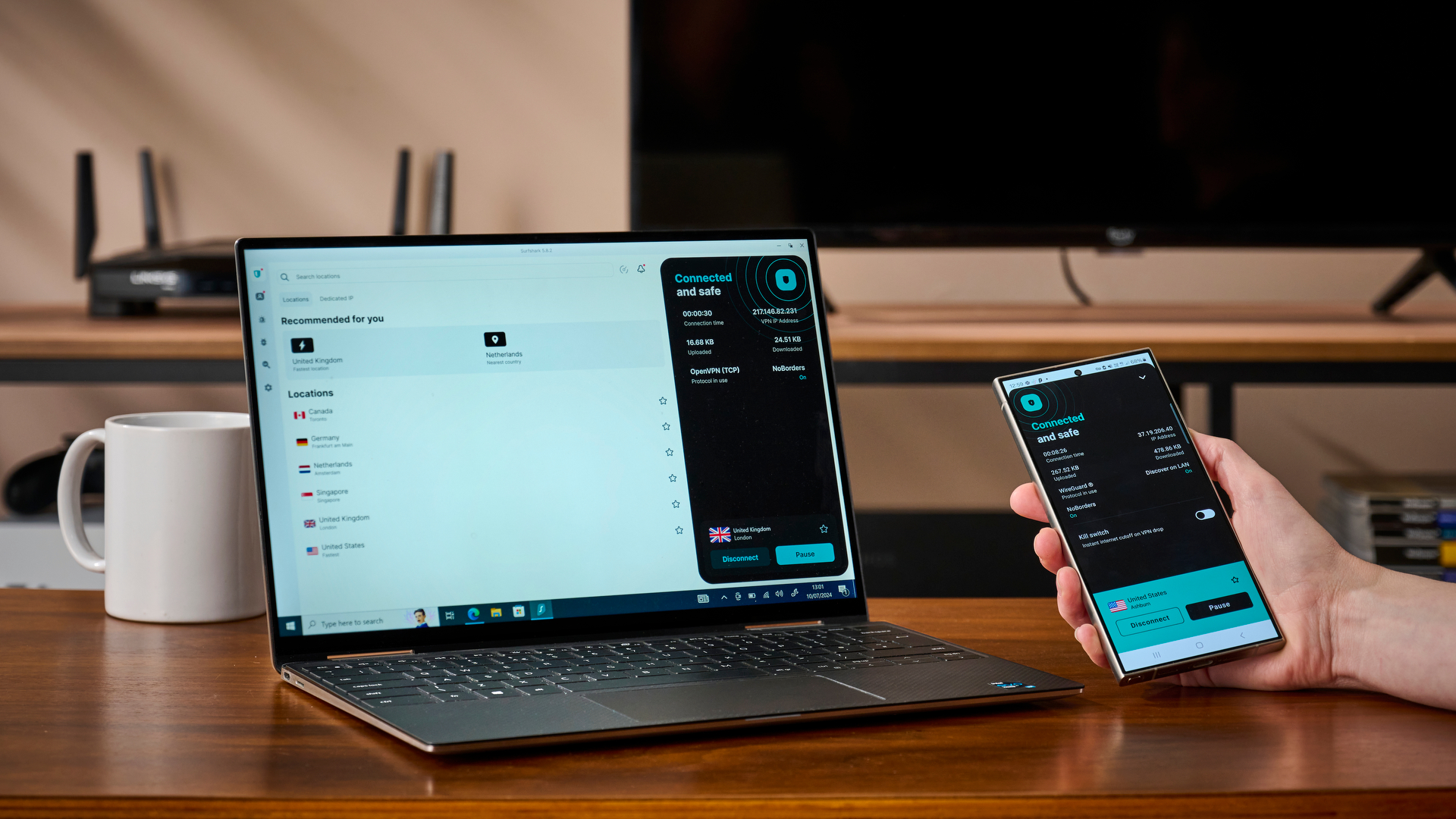
2. Surfshark
The cheapest and fastest VPN – an excellent choice on a budget.
For a straight-up VPN with all the basics of privacy, security, and streaming included, Surfshark really is excellent value. It costs less than NordVPN, it's half the price of ExpressVPN and there are no limits to the number of devices you can install it on with just a single, simple account.
Surfshark has some brilliant web browsing anonymity features that every casual user will love. You should be rightly tempted to choose it over NordVPN even though it loses out to the top dog on streaming, server spread, and security but only by a shade.
READ MORE ABOUT SURFSHARK ▼
Ease of Use ★★★★
Surfshark has an app for pretty much every platform and is one of the few to have a proper GUI for Linux. It's got you covered for routers, browsers, Fire Stick, and Apple TV, as well as all the regulars. It's also recently added macOS to the list of platforms which support its Surfshark Bypasser feature. That means that you can now choose to route some traffic through your normal connection, while still using the VPN for other functions, on a Mac computer.
Apple users should beware, though, that Surfshark announced that it will only support the four most recent versions of iOS and macOS. So, you will need your device to be able to keep up with Apple firmware updates if you're planning on choosing Surfshark in the medium to long term.
Should you wish to purchase a dedicated IP address, for easier access to sensitive online services with fewer annoying CAPTCHAs, then that's now available as a feature across all apps with browser extensions included since October 2025.
Surfshark is very straightforward to use – we love the QR code log-in for your secondary devices – but, with the location guide and quick access feature buttons all competing for screen real estate, there's a fair bit going on at a glance. That makes the interface a little tougher on the eye than NordVPN or ExpressVPN but not so much that it should put off any beginners.
If you do need help, the built-in AI chatbot will spit out some solid how-to type articles and there aren't many layers between you and a real, live customer support operative if that doesn't do the trick.
Read more details on Surfshark's compatibility and usability in the full review.
Streaming ★★★★
Streaming is probably Surfshark's weakest area at the moment, but it's important to remember how well a VPN can unblock streaming services is something of a moveable feast. What's true today is not necessarily the case tomorrow. It's just that, right now in the arms race, the streaming services are slightly better at spotting and blocking Surfshark IP addresses than we would like them to be.
Surfshark generally did an excellent job of unblocking free local streaming services from all round the world in our most recent lab tests. It was also excellent for unlocking regional Netflix libraries. It only really came a cropper Amazon Prime Video and US YouTube. NordVPN is the best streaming VPN if those are the services you need.
Surfshark's extensive and well designed server network certainly helps for streaming. With 141 server locations across 99 countries, you're not going to be short of options of places to pretend to be.
All of Surfshark's servers are optimized for streaming and torrenting but we did have a couple of issues of jitter which meant that video streams dropped out once or twice in our tests. Obviously, just reconnect the VPN and press play again should that occur.
You might also want to turn off both the CleanWeb ad blocker and the IP rotation feature for better results.
A problem, you say? Well, maybe but balance that against Surfshark's unlimited connections policy. That's right, you can use Surfshark on as many devices as you like simultaneously, all from just one account!
Read more details on Surfshark's unblocking and content in the full review.
Privacy & Security ★★★★½
Surfshark's AES-256 encryption tech puts it at the top table for security. Its CleanWeb browser add-on blocks ads from appearing on websites and denies cookie requests without you having to bother which we really, really like.
It also has a rather wonderful Alternative ID tool that effectively creates a fake persona – complete with name, email address, and phone number – to autofill into online forms when you'd rather not give your real details. Emails, calls, and messages get forwarded to your real versions until you pull the plug.
Surfshark's Camouflage Mode obfuscation technology helps you bypass VPN blocks by hiding the fact you're using a VPN. Its No Borders feature, meanwhile, detects if your current network is facing any restrictions and automatically recommends servers that perform best under those restrictions. There's no post-quantum protection future-proofing, like NordVPN or ExpressVPN, to prevent possible "store now, decrypt later" attacks but you can't expect everything for a bargain price.
The company's most recent security addition is the October 2025 arrival of Web Content Blocking which allows parents using One or One+ to deny access to adult websites, gambling sites or content with profanity, phishing, and malware to others on their network. This is something that Windscribe already offers and is a handy borrowed ideas from parental control services.
In the same month, Surfshark also launched its email scam checker tool for the Chrome browser extension. It uses AI to scan for any suspicious looking messages in your Gmail inbox and sends a warning if you find one, and all without recording any user email data.
Lastly, it's worth noting that Surfshark's headquarters, for legal purposes, is the Netherlands which is a member of the 14 eyes intelligence sharing community along with the United States, UK, Canada and Australia among others. If privacy is your top reason for using a VPN, for this reason alone, Surfshark is probably not the best choice.
Read more details on Surshark's privacy and security in the full review.
Speed & Performance ★★★★
You want speed? You got speed. Surfshark is the No.1 fastest VPN under ideal conditions. We clocked it in with average download speeds of 1615 Mbps over a local VPN connection.
Do bear in mind, though, that it can drop considerably when connection to a distant VPN server. We averaged just 355 Mbps with a hop over the Atlantic, while the likes of Proton VPN (1242 Mbps) and NordVPN (626 Mbps) fared much better.
Surfshark can also be prone to more jitter than others, which might make you suffer during gaming and streaming. If you're looking at pure up/download speeds, though, then Surfshark is hard to beat.
We can expect Surfshark to get even faster in the coming months, however, with the recent launch of its FastTrack route optimization technology which is designed to improve long distance connection speeds. More significant perhaps, though, is Surfshark's October 2025 launch of the world's first 100 Gbps VPN server. Now that's commitment to performance.
Right now, FastTrack is only available for Mac users accessing the Sydney, Seattle, or Vancouver servers, and the only 100 Gbps server is in the Netherlands but expect these technologies to rollout across the global network over the next year.
Better still, Surfshark announced a 40% expansion of its network to include 4200 servers as of October 2025. Always a good sign to see reinvestment.
Read more details on Surfshark's speed and performance in the full review.
Surfshark price plan comparison
The Surfshark Starter plan is where to go to keep costs at rock bottom. That's your VPN use, including ad and cookie pop-up blockers, plus the Alternate ID personal detail mask and masked email generator. The price has just gone down to its bargain basement $1.99 per month on the two-year plan, which makes it a really good moment to buy. It doesn't ever get cheaper.
However, it's very hard to turn down the upgrade to the Surfshark One plan, given that it's only about $9 more over 2 years and only about a $3 difference on the 12-month plan. That adds a built-in antivirus, webcam protection, and real-time credit card, ID, and email breach alerts.
Surfshark's premium plan, One+, is a tougher sell. It's around double the price of Starter at $4.19. The most noticeable benefit of One+ is that you get the Incogni data removal tool into the mix. It's a decent service, but it's probably only worth opting for Surfshark One+ if you were considering Icogni anyway.
As with NordVPN, do beware that Surfshark's prices may not be quite as good as they look, depending on where you're based. The company adds local tax at checkout, unlike the other VPN providers below, whose prices already include tax.
Also, like most VPNs, auto-renewal prices are steep. There's a handy article here on how to make sure your Surfshark subscription doesn't auto-renew without having to set yourself a calendar reminder.
If you'd like to get a taste of one of Surfshark's features for nothing, then you can try out its recently announced free private DNS service. It's a way of routing your internet traffic without allowing your ISP to block certain domains, log traffic or create targeted adverts based on your browsing.
Better still, Surfshark has introduced a 7-day free trial for the first time. It's the only one of the best VPNs to offer that which makes taking it for a spin something of a no-brainer. Our bet: you'll probably stick with it.
Be careful, when you click through to buy, that you select the 'Start a free trial' button and not the 'Get Surfshark' one, or you won't get the best prices on the Surfshark One+ plans.
All Surfshark plans come with a 30-day money back guarantee. Just in case you need to, here's how to cancel Surfshark and get a refund.
Here's a comparison table of the Surfshark plans and what each one offers and a direct comparison of NordVPN vs Surfshark:
| Header Cell - Column 0 | |||
|---|---|---|---|
1-month plan price | $15.45/month | $17.95/month | $20.85/month |
1-year plan price | $3.19/month | $3.39/month | $6.29/month |
2-year plan price | $1.99/month | $2.29/month | $4.19/month |
VPN | ✅ | ✅ | ✅ |
Ad blocker | ✅ | ✅ | ✅ |
Cookie pop-up blocker | ✅ | ✅ | ✅ |
Alternative ID | ✅ | ✅ | ✅ |
Web content blocker | ❌ | ✅ | ✅ |
ID breach alerts | ❌ | ✅ | ✅ |
Antivirus | ❌ | ✅ | ✅ |
Incogni data removal | ❌ | ❌ | ✅ |
Proton VPN – the best VPN for privacy

3. Proton VPN
Proton VPN is the best choice if privacy features and widespread server access are top of your wishlist.
Proton VPN is one of many privacy-centric products built by Proton. It's a CERN-scientist-founded, Swiss company committed to the "societal problem of surveillance capitalism" rather than a Silicon Valley venture capitalism get-rich-quick machine.
So long as Proton sticks to that mission, that makes it quite an ethical VPN choice and one that works pretty much as well as all the others on this best VPN list. It was certainly a good sign to see a strong reaction from Proton's CEO on the possible change in Swiss data protection laws – and Proton's willingness to relocate should the country's surveillance bill force Proton to collect user data – and finally that the Swiss authorities are reconsidering those changes as of December 2025.
Launching free privacy tools, such as the Data Breach Observatory, in October 2025, is yet another good indication that the mission is here to stay.
The big reason to choose Proton VPN is if privacy is of paramount importance to you – or if you need a good range of server locations across Africa, the Middle East, and Asia – but don't let that fool you.
With over 15,000 servers across 126 countries, Proton VPN is every bit the right tool for those looking for some serious streaming and torrenting fun too.
READ MORE ABOUT PROTON VPN ▼
Ease of Use ★★★★
Proton VPN is easy to use, thanks to a recent UI refresh of its Windows, iOS and Android apps. It may not have a Chrome browser extension that's as reliable as others but it does boast a Linux application with a decent graphic interface and those new-look mobile and desktop apps. We really like the added home screen widgets for mobile and upgrades to the Profile feature which allowed us to switch protocol and server by use cases like streaming, anti-censorship and gaming, really quickly.
Proton also recently partnered with privacy-focused browser Vivaldi. So, if you really do want a VPN browser extension for Proton, you might consider Vivaldi instead of Chrome. Best of all, though, is that Proton is finally bringing the split tunneling feature to macOS and Linux users this summer along with a host of other upgrades that we saw when the other major platform apps were upgraded in April. That's a terrific result.
If you're interested in a VPN app for Android TV, then Proton's definitely one to consider. There's a plenty of focus from the company on Google's TV interface which might be of note to anyone following Amazon's Fire Stick crackdown. Proton updated its Android TV app in November, 2025, to include support from the NetShield advert and tracker-blocking tool.
Sadly, Proton VPN loses a few marks in the Ease of Use category for customer service. Like the others in this list, the live chat isn't 24/7. It's only available during Swiss work hours – not great if you're based on Pacific Time in the States or live in Australia or New Zealand. That said, we're assured that this is an area where Proton VPN is soon to improve.
Read more details on Proton VPN's compatibility and usabilityin the full review.
Streaming ★★★★
Proton VPN is a good choice for both streaming and torrenting. It's one of the few VPNs where port forwarding is still available and there are dedicated, P2P-optimized servers, which, again, is great for torrenting.
Proton VPN also has more country locations than any other VPN. If you're looking to connect to a regional service in Africa (22 countries) or the Middle East (14 countries) then it should be high on your list. It also has more Asia locations covered than any other provider on this page.
The trade-off is that there aren't so many server locations in the US or across Europe, but most countries are covered in those places, even if there's not much at the city/region level. More to the point, Proton VPN had no trouble with any local or international streaming services we tried. We managed to access the desired Netflix, Prime Video, and Disney Plus libraries with every server we tried.
Read more details on Proton VPN's unblocking and content in the full review.
Privacy & Security ★★★★½
Proton VPN has been built from the ground up as a privacy-first product and plenty of features show that off. But expect its privacy credentials to get an even bigger boost over the last few months of 2025 with company CEO Andy Yen announcing that an all-new, in-house VPN architecture is on the way as part of Proton's 2025 autumn/winter roadmap.
In the meantime, there are still plenty of excellent features already available.
Proton's Secure Core sends your VPN traffic through an extra secure server in a privacy-friendly location (Switzerland, Iceland, or Sweden) and then onto the endpoint VPN server. Similar to NordVPN's Double VPN system, that means your traffic is secured twice, reducing the risk of your IP getting exposed if the endpoint server is hacked.
As well as OpenVPN and WireGuard, Proton uses its own Stealth protocol which hides the fact you're even using a VPN which could be very important if you're in a region where VPN use is banned.
Equally, you can opt to use the Alternate Routing feature instead which sends your IP-relocated internet traffic through a third-party server, like Amazon's, for example. That helps to get around sites that don't play nice with VPNs.
You can also connect directly to the Tor network through some Proton VPN servers which might be handy if you're in a line of work that requires extra anonymity.
Proton VPN Plus also brings the use of the NetShield Ad-blocker feature. It did a decent job with ads and trackers, although the malware-blocking end wasn't particularly comprehensive. Get a decent AV for that instead.
Lastly, and by no means least, Proton has a tight no-logging policy – successfully audited for the fourth time in September, 2025 – and an excellent system of handling customer data, which received a 'SOC2 Type II" audit to prove its worth in July of the same year.
Read more details on Proton VPN privacy and security in the full review.
Speed & Performance ★★★★
In previous rounds of testing, Proton VPN has always played second fiddle when compared to the speeds on offer with other VPNs on this list, but not any more. Proton VPN was arguably the fastest VPN we tested in October 2025, using the WireGuard protocol.
The VPN Accelerator feature does a good job of automatically finding the routes with better speeds when connecting to long-distance servers, meaning that both short and far-flung server download speeds were consistent at 1521 Mbps and 1242 Mbps, respectively.
Sadly, Proton VPN is behind the game for those looking to use OpenVPN, though. Its 240 Mbps local connection performance was a long way back from ExpressVPN (1038 Mbps) and NordVPN (974 Mbps).
Do bear in mind, though, that for streaming purposes, Proton VPN still has plenty under the hood. Indeed, its latency and jitter scores were nice and low, which arguably, is more important for some use cases.
Read more details on Proton VPN speed and performance in the full review.
Proton VPN price plan comparison
The free version of Proton VPN is one of the best free VPNs available, and worth your consideration, depending on your needs.
The paid version of Proton VPN is the one to go for if you want to use the streaming functionality, though. Upgrade to Proton Unlimited if you want all of that plus access to the full suite of Proton web products including Proton Mail, Proton Drive, Proton Pass and more. (You can compare two top-end VPN bundles here with NordVPN Prime vs Proton Unlimited.)
Soon you'll be able to do that direct from Apple's App Store and still get the best online price after a US ruling found against "the Apple Tax".
Proton VPN's two-year plan is the best value. You only need to subscribe to the full Proton Unlimited package for a year if you want the best monthly price for all the Proton products, though.
Best of all, it's a really great time to sign up for Proton VPN. It's currently down at a year-long low of $2.99 instead of its regular $3.59 price point. That's excellent value on a terrific VPN.
Proton VPN comes with a 30-day money-back guarantee. We have a guide on how to cancel your Proton VPN subscription and get your money back.
Here's a comparison table of the Proton VPN plans so you can see for yourself:
| Header Cell - Column 0 | |||
|---|---|---|---|
1-month price | Free | $9.99/month | $12.99/month |
12-month price | Free | $3.99/month | $9.99/month |
24-month price | Free | $2.99/month | $7.99/month |
VPN | ✅ | ✅ | ✅ |
Streaming | ❌ | ✅ | ✅ |
Server choice | ❌ | ✅ | ✅ |
Malware protection | ❌ | ✅ | ✅ |
Tracker blocking | ❌ | ✅ | ✅ |
Ad-blocker | ❌ | ✅ | ✅ |
Tor over VPN | ❌ | ✅ | ✅ |
Proton Mail, Calendar, Drive, and Pass | Free features only | Free features only | ✅ |
ExpressVPN – the best VPN for Windows users

4. ExpressVPN
Choose your location and switch it on; it's pricey but fast, particular for PCs.
Price used to be the main reason ExpressVPN sat behind NordVPN and Surfshark in our best VPN. In September 2, 2025, ExpressVPN introduced a three-tier structure to offer customers a cheaper entry point. Nonetheless, it's still expensive compared to the others, including Proton VPN, which is now up in third spot. You get more features for less with Proton.
ExpressVPN did have a few gaps in streaming during our most recent testing, compared to NordVPN, and, while it's the best VPN for beginners, none of the other three VPNs above are so complicated that they should put you off.
It's also worth noting that ExpressVPN reduced its workforce back in March, 2025, in big enough numbers that it felt it needed to release a statement. So far, it's doesn't seem to have affected the product, although getting dragged into a class action over auto-renew fees will not be helping the situation back at HQ.
Most interestingly of all, though, ExpressVPN launched a free, ad-supported VPN into the market in September 2025, called EventVPN. We look forward to taking it for a spin and seeing how this affects both the paid and free VPN markets.
READ MORE ABOUT EXPRESSVPN ▼
Ease of Use ★★★★★
The ExpressVPN user interface is just great. There's nothing glitzy about the look of its apps but there's a simplicity that belies a lot of very clever design. It's red when it's off, it's green when it's on and the first two sections that draw your eyes are the massive Connect button and the server location option which opens up a list of countries either recommended or by continent. The casual user needs to go no further and get everything they need right there.
There are apps for every platform. ExpressVPN even has its own Aircove router if you want the VPN working at the heart of your home network, and, in fact a recent software update for Aircove and Aircove Go has improved their core infrastructure to make the user experience more stable and easier.
Likewise, ExpressVPN updated its iOS and Android apps in May 2025. They now include built-in speed testing tools, access to more VPN protocols and a Smart Location connection for an automated link to the best server at any given moment. There are also new ExpressVPN widgets and Siri shortcuts on the iOS app to enjoy.
ExpressVPN continued its charm offensive on Apple users in September, 2025, with updates for its iPad and macOS apps too. Tablet users will now get a screen-filling app UI that's more responsive and easier to use. Mac owners get a streamlined install process.
And the company went one step further for Mac users, in December 2025, with a ground-up reconstruction of its Mac VPN app, with its first native version of the software. It's set to offer a more authentic Apple look and feel, and better performance too.
As of March 2025, Linux users got to join the party too with a GUI finally added to the ExpressVPN Linux app. More recently, in December 2025, the Linux app was the first to receive the new Qt (pronounced 'cute') app framework revamp which should help features roll out across all platforms more quickly. (The Qt Mac and Windows versions are currently in beta.)
Whichever apps you use, do take note that you'll need to update them ahead of January, 2026. ExpressVPN has announced that apps using older certificates will expire and need replacing for you to stay connected.
The other place your money goes is the 24/7 live chat in the help section of the app. Waiting times to get connected to human support can be as little as 30 seconds. We were never left hanging for more than 5 minutes in our tests. There is just no better VPN for usability.
Read more details on ExpressVPN's compatibility and usability in the full review.
Streaming ★★★★½
With over 187 locations in 108 countries, ExpressVPN will have you covered for most of your streaming needs – certainly when accessing streaming services across the States, UK, and Europe. It has the most Oceania server locations of our top five and it did a great job of unblocking Netflix, 10Play and 9Now in Australia. Use the 24/7 live chat for advice on the best server choice if you do find any issues and that should sort it.
In fact, ExpressVPN has just expanded its server network so that it now has a server location in every single one of the 50 US states. That's great news in terms of both speed for folks in the US and for ensuring you get the correct online state laws when you connect to your nearest server.
ExpressVPN is a bit short across the Middle East with just two countries to choose from. Not great for BeIn sports content in that part of the world, or watching Ronaldo in the Saudi Pro League or any other local content from Saudi, UAE, and the like.
In terms of stream stability, ExpressVPN does pretty well, although it does feel like NordVPN has the edge here with fewer instances of dropping out when viewing trans-Atlantic content – another reason why you might want to make a different choice if streaming is your no.1 VPN use case.
Read more details on ExpressVPN unblocking and content in the full review.
Privacy & Security ★★★★½
As with Surfshark and NordVPN, you do get a lot of security features with ExpressVPN. The only difference since the September price changes is that, now, they're not available to every customer.
Advanced and Pro subscribers get the ExpressVPN Keys password manager, parental controls to stop access to adult sites, free eSIM use, and a tracker and malware threat manager. Dedicated IP address access is the big perk for the Pro tier.
All users, from Basic upwards, benefit from one of the best built-in ad blockers on this list, as well as the VPN product itself. The only disappointment in our tests was the fake website warning system which let far too many slip the net to really trust.
Fortunately, ExpressVPN gets the basics of security bang on. It uses top-end, rotating key, AES-256 encryption as well as a 1000-dimension secure ML-KEM key designed to future-proof your data for the quantum computing age too. We're also big fans of the randomly allocating Shuffle IP system which ensures there's no correlation between your identity and your online activity.
Combine that with the provider's TrustedServer technology, its commitment to post-quantum encryption, and the fact that data requests are made very difficult thanks to its British Virgin Islands choice of jurisdiction, and it's high marks here.
In fact, ExpressVPN passed its 23rd successful security audit in July 2025 (courtesy of KPMG) confirming that it never stores user data as indicated in its privacy policy.
The company is so confident in its security that it offers a $100,000 bug bounty should you ever get inside an ExpressVPN server. No one has ever claimed it.
Read more details on ExpressVPN privacy and security in the full review.
Speed & Performance ★★★★
Lightway is the name of ExpressVPN's bespoke VPN protocol. It's optimized for mobile use – certainly no bad thing in the modern age – but it was long way short of NordLynx or WireGuard, as used by Surfshark and Proton VPN, in our latest lab speed tests.
We clocked Lightway in with average download speeds of 489 Mbps, even over a local connection. Compare that to NordVPN (1256 Mbps), Surfshark (1615 Mbps) and Proton VPN (1521 Mbps) and it doesn't look good.
Fortunately, Lightway's performance gets a serious boost through the ExpressVPN Windows apps, however, thanks to the rollout of Lightway Turbo and DCO and with the recently launched Lightway 2.0. and it's more streamlined coding in Rust. Lightway in Rust is already on Aircove devices and is expected to land elsewhere in 2025.
We clocked Lightway Turbo in at an average local download speed of 1479 Mbps, second only to Surfshark (1615 Mbps), and it also performed well when we connected to long distance VPN servers. Its 1374 Mbps transatlantic speed was the best of any VPN.
What's more ExpressVPN is one of the fastest VPNs overall when using OpenVPN, matched only by NordVPN's OpenVPN performance, and that's available across all platforms – not just Windows.
ExpressVPN's speeds are looking to extend into the post-quantum era, too. The provider adopted WireGuard, on August 13, 2025, in addition to its proprietary Lightway protocol; the move gives users a quantum-secure, high-speed protocol, thanks to adopting ML-KEM encryption. Plus, it's already available across Windows, iOS, and Android.
As it turns out, Opera VPN has been so impressed by ExpressVPN's protocol technology that it's decided to switch to Lightway itself – quite the vote of confidence when it comes from a third party, and a bit of a slight to NordVPN and NordLynx too.
If all of ExpressVPN's protocol choices seem overwhelming, then fear not. The company updated its apps, in December 2025, to include a Fastest Location option. That way, you can just hit the button and be assured that you're getting the best performance possible for your circumstances.
Read more details on ExpressVPN speed and performance in the full review.
ExpressVPN price plan
A subscription to ExpressVPN Basic brings access to the VPN product and Lite Protection (a DNS-level ad-blocker and malicious website blocker) on up to 10 devices simultaneously. Post-Black Friday sales, ExpressVPN Basic is back up to $3.49 per month, making it pricer than NordVPN right now.
Pay a little extra ($4.49 per month) for the Advanced plan over two years and you'll get the sweet spot. It's a pretty compelling package with advanced browsing protection, the password manager, and three days per month of free eSIM use. If you're in the US you get ID monitoring with fraud alerts, and identity restoration too.
If you really want the dedicated IP service, then Pro is worth it but it's a big step up. If that's not something you need, you're best off with Advanced.
ExpressVPN's auto-renewal prices (subject to change) are a lot better than Surfshark and NordVPN. All the same, here's an article on how to cancel your ExpressVPN subscription before your subscription ends, which we recommend doing. That will stop the auto-renewal and still allow you to use ExpressVPN right up until the last day of your agreement.
Here's a table showing ExpressVPN's main features and a direct comparison of ExpressVPN vs NordVPN:
| Header Cell - Column 0 | |||
|---|---|---|---|
1-month plan price | $12.99/month | $13.99/month | $19.99/month |
1-year plan price | $4.99/month | $5.99/month | $8.99/month |
2-year plan price | $3.49/month | $4.49/month | $7.49/month |
VPN | ✅ | ✅ | ✅ |
Ad blocker | ✅ | ✅ | ✅ |
Password manager | ❌ | ✅ | ✅ |
Dedicated IP | ❌ | ❌ | ✅ |
Data Removal | ❌ | ❌ | US-only |
ID Monitoring | ❌ | US-only | US-only |
$1M ID theft insurance | US-only | US-only | US-only |
eSIM use / month | 0 days | 3 days | 5 days |
Simultaneous connections | 10 | 12 | 14 |
Aircove discount | None | 50% | 75% |
PrivadoVPN Free – Best Free VPN
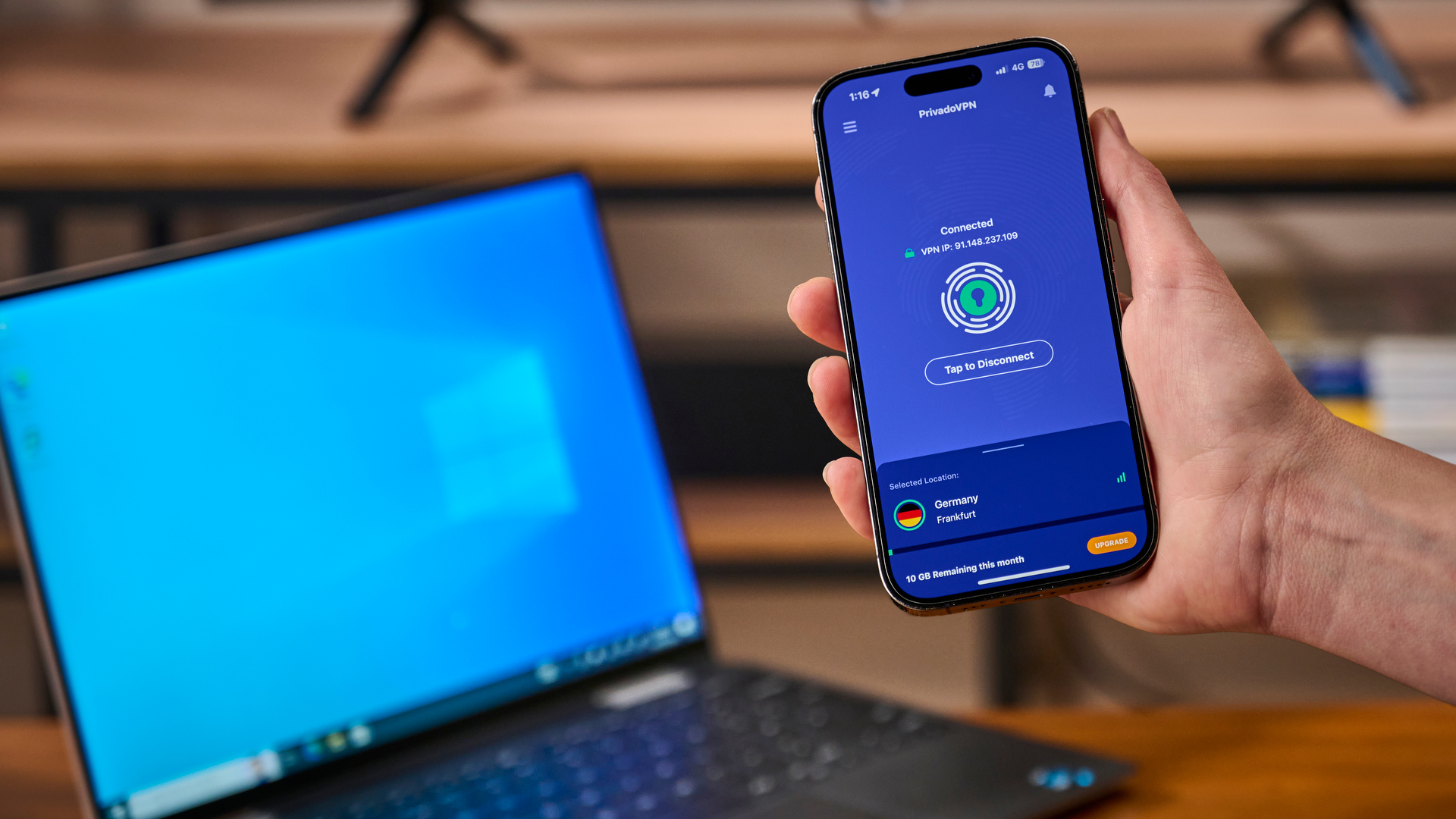
5. PrivadoVPN Free
For occasional use, including some worldwide TV show streaming, it's hard to beat the best free VPN.
It's not all about money. The best things in life are free. Well, the fifth-best thing, at least. A paid VPN is a better choice for anyone serious about using a VPN regularly but, if you’re looking to dip your toes in the VPN waters and see whether you like the feel, PrivadoVPN Free is a good choice.
Why? Because you get to play with most of the important features that a paid VPN offers and that’s not the case for many of the other best free VPN services. You can do things like unblocking access to trans-Atlantic Netflix libraries (in a limited way) and you also get the peace of mind that PrivadoVPN won’t sell your data to make up for the fact you’re using its service for free.
READ MORE ABOUT PRIVADOVPN FREE ▼
Ease of Use ★★★
PrivadoVPN Free doesn't come with as much customization and functionality as a paid VPN, the upside of which is that it’s certainly easy to use. There are apps for Windows, MacOS, Android, Android TV, iOS, Apple TV, and FireTV. Annoyingly, the Chrome extension has slipped behind the paywall in 2025. If you're struggling to install these apps, then the online knowledge base is good but live chat access is limited.
By default, the layout is a lot simpler than many, and the user interface is uncluttered. There’s the location manager, where you choose which server you wish to connect to; the recently revamped and stabilized kill switch; the connect button; and a handy reminder of how much data you have left; and that’s pretty much it. Hit ‘Click to Connect’ and away you go!
Read more details on PrivadoVPN Free apps and usability in the full review.
Streaming ★★★½
Streaming is where PrivadoVPN Free stands head and shoulders above other free VPNs. There’s not really much streaming on offer elsewhere, without paying, because of very low data allowances and limited, or often no, server choice.
PrivdoVPN Free allows you to access its 13 servers across 10 countries: Argentina, Brazil, Canada, France, Germany, India, Mexico, Netherlands, UK, and the USA. You also get 10 GB of data to use each month. That’s about 10, hour-long, TV shows at standard definition. If you need more than that, then maybe it’s time to pay for your VPN.
The split tunneling feature is handy for minimizing your data use but, if you do bust the limit of your allowance, then PrivadoVPN Free will let you connect still but only on the 1 Mbps server. With no servers in Australia, New Zealand or Italy, there are a lot of great free streaming services that you miss out on here but it did still manage to unblock Netflix, Disney Plus, BBC iPlayer, Channel 4, and ITV in our recent tests.
Read more details on PrivadoVPN's Free streaming in the full review.
Privacy & Security ★★★½
PrivadoVPN Free brings access to its VPN but not much else in the way of privacy and security features, aside from the kill switch. It uses AES-256 encryption and offers OpenVPN, WireGuard protocols as well as the usually slower IKEv2, if you need.
We love that PrivadoVPN doesn’t sell its free users’ data to fund the gratis access. We love its strict no-logs policy. We love that it’s based in Switzerland too, where data protection laws are super tight. But the fact that PrivadoVPN has never had a third-party audit to check all this? Not so much. But then audits cost money and the users aren’t paying, so, you know.
Read more details on PrivadoVPN's Free privacy and security in the full review.
Speed & Performance ★★★½
You might expect a free VPN to be significantly slower than the paid options on this page but that’s not the case with PrivadoVPN Free. It recorded a frighteningly fast 1045 Mbps average download speed on our VPN speed testing rig using WireGuard.
That's faster than ExpressVPN over WireGuard (694 Mbps) and not a long way short of NordVPN (1256 Mbps). PrivadoVPN Free even recorded a peak speed of 900 Mbps over a long distance before we ran out of our 10 GB of free monthly data.
So, as we say, you get a lot more than the other best free VPNs with PrivadoVPN Free. What you don’t get is the unlimited ability to use it.
As we say, you get a lot more than the other best free VPNs with PrivadoVPN Free. What you don’t get is the unlimited ability to use it.
Read more details on PrivadoVPN's speed and performance in the full review.
PrivadoVPN price plan comparison
PrivadoVPN would much rather you sign up for its paid VPN service. The free version is not easy to find on its website. It's usually a greyed-out button buried pretty deep on the sign-up page.
In many ways, it has a point, though. PrivadoVPN Free is a good service but if you need a VPN on the regular, you're better off reaching into your pocket.
Here's a feature comparison table of the PrivadoVPN Free and paid plans and you can see if you agree:
| Header Cell - Column 0 | ||
|---|---|---|
1-month plan price | Free | $10.99/month |
12-month plan price | Free | $1.33/month |
24-month plan price | Free | $1.11/month |
VPN | ✅ | ✅ |
Server countries | 10 | 48 |
Data Limit | 10GB/30 days | Unlimited |
Simultaneous connections | 1 | 10 |
Ad blocker | ❌ | ✅ |
Parental controls | ❌ | ✅ |
Other VPNs we've tested
We rate the five VPNs above as the best available right now but there are plenty of other VPNs that we've reviewed. If you see a killer VPN deal out there for one of them, it might be worth your consideration, certainly if it's high up this list. We've put the highest-scoring VPNs at the top. The ones near the bottom are VPNs you should avoid.
Mullvad ★★★★½
A major player in the industry, and a great advocate for privacy. Mullvad is one of the only VPNs that still lets you pay with cash for true anonymity. Now with an ultra-fast obfuscation protocol too.
▶ Read more: Mullvad review
IPVanish ★★★★
A fast VPN with a decent track record for unblocking streaming services. It sits in the middle of the pack because we find its apps to be a little clunky.
▶ Read more: IPVanish review
Windscribe ★★★★
This privacy-friendly service doesn't believe in bells and whistles. But it's a great VPN with a modern server network, and an excellent free plan for you to get a taste of the service.
▶ Read more: Windscribe review
CyberGhost ★★★★
Part of the Kape conglomerate, CyberGhost is a popular VPN that's good for beginners. Decent speeds and a high unblocking score make it a great pick for newcomers, but it's still not as good as our top picks.
▶ Read more: CyberGhost review
CLICK TO SEE MORE VPNS WE'VE REVIEWED ▼
PureVPN ★★★★
A near-perfect streaming score and exceptional WireGuard speeds make this budget VPN a worthy consideration. However, there are still a few kinks that need working out in the apps.
▶ Read more: PureVPN review
Hide.me ★★★★
Decent speeds and streaming unblocking put Hide.me center of the pack for functionality, but its complicated apps and lack of audits undermine an otherwise great service.
▶ Read more: Hide.me review
Private Internet Access ★★★½
One of the best VPNs for Linux, and a popular VPN for torrenting, PIA is an industry veteran that has proven its no-logs policy in court (twice). Some connection issues and underwhelming speeds saw it fall out of our top ranks, but it's still a good app that's particularly well-suited for power users.
▶ Read more: Private Internet Access review
Hotspot Shield ★★★½
A popular free VPN that claims to be the fastest on the market. Our tests show otherwise, and it struggled in our stream unblocking tests, too.
▶ Read more: Hotspot Shield review
TunnelBear ★★★½
A popular brand that's had some excellent marketing campaigns, but the VPN itself is lackluster and can't hold a candle to the market leaders.
▶ Read more: TunnelBear review
FastestVPN ★★★½
With a $30 lifetime use deal on the table, FastestVPN makes a serious statement. But its server network comes up short and, despite its name, it's a bit slow.
▶ Read more: FastestVPN review
VyprVPN ★★★½
Previously hailed for its proprietary Chameleon protocol, Vypr has lost a lot of that venom that kept it nipping at the heels of the top three.
▶ Read more: VyprVPN review
AngelVPN ★★★½
A relative newcomer, AngelVPN is speedy and has the bonus of servers in Russia and China but a lack of extra features and some logging issues mean it can't go head-to-head with today's top dogs.
▶ Read more: AngelVPN review
Amnezia VPN ★★★½
Created by Russian activists looking to avoid state censorship, Amnezia VPN is an open-source VPN, with both free and paid tiers, that allows you to set up your own personal VPN server. It isn't the best for unblocking, streaming, or pure performance but that niche use case might be just what you need.
▶ Read more: Amnezia VPN review
AdBlockVPN ★★★
An open-source VPN with an ad blocker included is a great idea but AdBlockVPN is just too short on features to offer value for money – no kill switch, no WireGuard, and just 38 server locations. At this price, there's far better out there.
▶ Read more: AdBlockVPN review
NymVPN ★★★
Of course, a VPN based on blockchain technology has to exist. Zero-knowledge trust and decentralized privacy certainly make sense but, still in beta, NymVPN isn't quite there yet.
▶ Read more: NymVPN review
OysterVPN ★★★
Another new kid on the block, OysterVPN has plenty of great security tools and strong unblocking credentials. Missing WireGuard support and sluggish speeds are a major drawback for now, though.
▶ Read more: OysterVPN review
PrivateVPN ★★½
Once upon a time, this was a go-to VPN service. However, it's fallen behind the pack and now struggles to offer the same features and functionality.
▶ Read more: PrivateVPN review
SweatVPN ★
It may be aimed at Warzone players but SweatVPN is not the best VPN for gaming. If bot lobby after bot lobby is all you want, then it's just about a maybe but don't expect long before you get yourself banned.
▶ Read more: SweatVPN review
Hola VPN ★★
Hola VPN collects some concerning log data, including your "IP address, operating system, browser type, web pages you visit, time spent on those pages, access times and dates." In our opinion, this logging undermines the entire purpose of using a VPN for privacy, even if it's doing it to prevent people from abusing your IP address, which it uses as one of its so-called "nodes."
▶ Read more: Hola VPN review
What is a VPN?
A virtual private network (VPN) is a tool that creates a secure and encrypted connection between your device and another location on the internet. VPNs ensure privacy and security online by masking your IP address – and therefore your location – and encrypting data that's transmitted to and from your device, making it impossible for third parties to intercept or track your activities.
Without a VPN, your ISP can monitor and track which websites you access and the data you're transferring. Governments and legal bodies can then request to access that information or hackers may expose it. Install a VPN and no one can see your data or what you're doing online.
What does a VPN do?
A VPN provides security, privacy (the most popular reason for using a VPN, in fact), and a degree of anonymity (not total anonymity, despite what many people think) to you and your devices when using the internet. VPNs can also unblock your favorite streaming services from abroad, help you get cheaper prices when shopping online, assist with torrenting and online gaming connections, and they're a terrific tool for protecting yourself on public Wi-Fi.
Most good VPNs have ad-blockers and will deal with those annoying cookie-consent pop-ups too. You can read more about the benefits of using a VPN.
How to buy a VPN
There are two important things to note when buying a VPN: you have to pay the full amount up-front BUT most come with 30-day money-back guarantees, so you can change your mind for a full refund.
So, for example, if NordVPN's Basic plan is advertised at $3.39 per month for 24 months, that means you'll need to pay the whole $81.36 when you sign up. (You may also have tax to pay on that, region depending.) You'll then receive 24 months of service before you get the choice to pay again for another term.
As for the money-back guarantee, we've tried it, and it works. Most of our top picks also have 24-hour live customer support which makes it all the easier.
Finally, once you've bought and installed your chosen VPN, we'd advise deactivating any auto-renew settings. Some auto-renew prices can be eye-watering compared to the initial fee. Take a look at more things to consider when buying a VPN.
What to look for in a VPN
NordVPN, Surfshark, ExpressVPN and Proton VPN are probably going to fit most people's needs but if you've some specific use cases or have some key criteria, then you should probably consider the following. You can read more about each in our article on choosing a VPN.
Price
Anything under $2.50/£2.50 per month is a cheap VPN; up to $4.50/£4.50 per month is about average; and anything over $5/£5 per month is on the expensive side. There are also free VPNs but they usually come with limited usage and features. They're not great for streaming, torrenting or gaming. The longer the term of your agreement, the cheaper the price. Anything less than a year tends not to be great value.
Apps
Most VPNs have apps for Windows, Mac, iOS, and Android but do check. Linux users and anyone looking to install a VPN on an Amazon Fire Stick, a router, or a smart TV should definitely read the small print on this one.
Security & Privacy
Is it meeting industry standards for encryption? Is there a kill switch? Does it have a no-logs policy, and has it been audited? Look out for nifty security features that ensure no patterns to link you and your given IPs, and for anything that will help prevent encrypted data from getting cracked either now or in the future. And check the company's track record to make sure they have kept customers safe in the past.
Server locations
Does the VPN you're interested in have physical servers in the countries you need or just virtual VPN servers? That might be one where you live or one in a country with a geo-blocked streaming service that you're trying to access.
Performance
Can you trust VPN speed tests? Well, you can certainly trust performance. Consistency and quality are critical. You'll suffer poor performance if the VPN you've chosen has issues with latency or jitter. The end result will be packet loss during data transfer which you'll experience as buffering or a stream dropping when using video-based applications eg: video calls, online gaming, and watching Netflix.
Extras
Many providers include more than just the VPN. There are ad-blockers, password managers, antivirus software, and even cyber insurance bundled in sometimes. Are these things you'd like too, or are you better off keeping costs down? Picking the right price plan is usually the key here.
Customer support
Most of our top VPN providers have excellent, 24/7 live customer support. They're there to help you with any issues from solving your streaming problems to arranging the refund from your money-back guarantee. If the service you're looking at doesn't offer something similar, then you might want to think again.
Are VPN's legal?
Yes. VPNs are legal to use in most places around the world. The exceptions are North Korea, Belarus, Oman, Iraq, and Turkmenistan, where VPNs are illegal, and China, Russia, Turkey, UAE, India, Iran, Egypt, and Uganda where you can only use a state-approved VPN, the actual privacy of which would be questionable at best.
But, as far as everyone in the US, UK, Europe, and most other places go, yes, VPNs are perfectly legal to use. Go get one!
Do you need a VPN?
Good question. No. Not everyone needs a VPN. But they can be useful depending on who you are, what you do, and how you like to use the internet and online services.
If you want to access streaming services from all around the world – BBC iPlayer, ITV, SBS On Demand, 9Now, RAIPlay, Max, ESPN+, Sling, Hulu, etc – then a VPN is the best way to do that. Equally, a VPN is perfect for making sure you can access the right libraries for Netflix, Prime Video, and Disney Plus.
Primarily, though, VPNs are about online security. For the everyday user, that might mean staying safe while using public Wi-Fi, or minimizing the cookies and trackers that harvest your details as you browse the web and other connected services. That should lead to less email spam and less chances of cybercrime attack too because you're far less likely to have your details stolen in any online database hacks.
Some VPNs can offer a more ad-free online experience too while others have built-in tools to help steer you away from fraudulent websites and malware.
The only group for whom we'd say VPNs are a must are journalists, political activists, and people around the world who need to protect themselves from oppressive governments, access foreign media, and learn and report on global truths. If you want to make sure you're able to evade censorship and propaganda while maintaining anonymity and privacy online, a VPN is non-negotiable.
For any of those reasons above, or if you just want peace of mind that you're more in control of your personal data in a rapidly progressing digital age, then a VPN is probably a good idea. Give one a go and try it for yourself. Most have a 30-day money-back guarantee if you decide a VPN is not for you.
Are free VPNs as good as paid VPNs?
A free VPN might be enough if you don't intend to use it much or don't need to use it for streaming, gaming or torrenting. There are some bad free ones out there but if you choose one of the best free VPNs then you won't come unstuck.
A free VPN is usually limited in the amount of data it offers each month or by the number of server locations it offers. That's why streaming on a free VPN isn't usually going to work. You can certainly expect far fewer features on a free VPN too.
Take a look at our free vs paid VPNs page for a better idea, and do check out these free VPN trials of paid services. All those listed will offer a refund within 30 days if you're not happy with the service.
How we test VPN services
We've been testing VPNs for longer than almost any other online publication and feel very confident about our methodology.
Each VPN is tested twice per year on TechRadar. That way, we can be sure that this guide is as up-to-date as possible whenever you happen to be reading it. Every recommended VPN on this page has been fully reviewed.
We test all the VPNs on the following categories:
Feature analysis: Technical details, network size, server locations, and supported protocols.
Privacy and security: Privacy policies, encryption methods, independent security audits, data leak protections.
Performance testing: Connection speeds, connection times, video streaming performance, web browsing performance, gaming performance, torrenting performance.
Unblocking abilities: VPNs are tested against over 20 of the most common streaming services including Netflix, Amazon Prime Video, Disney+, Hulu, BBC iPlayer, and many more.
Support and reliability: Customer support facilities, such as live chat and email support and help sections on provider websites.
You can read more about our full VPN testing methodology here.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

Dan is Editor-in-Chief, VPN and How to Watch, at Future. He heads up all the VPN content and how to watch articles. So, if you want to know about what is the best VPN or how to watch just about anything on TV, anywhere in the world, he's a good bet to ask. Dan has worked in tech journalism for over 15 years, writing for Tech Digest, Pocket-lint, MSN Tech, Wareable and What Hi-Fi? as well as freelancing for T3, Metro and the Independent. Dan has a keen interest in playing and watching football. He has also written about it for the Observer and FourFourTwo and ghost authored John Toshack's autobiography, Toshack's Way.























