How to lock your PC with a USB drive
Secure your PC quickly when you have to walk away from it
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
You're sitting at your home PC. You have a browser window open with about a dozen tabs, you're writing and updating a couple of text documents and reading through a PDF or two.
To ward off the midday slump, you decide to go for a little walk, but what do you do with your open workspace?
To protect your machine from prying eyes, you can either close all the apps and shut down the machine, activate a password-protected screensaver, or take it with you.
The first of these options is time-consuming and tedious, while the second leaves you vulnerable to shoulder surfers and the third might not be feasible, especially if you're working on a desktop computer.
Engage the Predator
This is where something like Predator comes in. It's designed for situations where you need to leave your computer switched on and unattended.
The tool turns any USB key into a physical key, which you can use to lock and unlock your system. Not only does it save you the hassle of rummaging in menus or fiddling with shortcut keys to lock your session, Predator also includes security features to ensure privacy and let you keep an eye on unattended PCs remotely.
Creating a USB key with Predator is a walk in the park. Follow the walkthough below to get started. The software doesn't wipe existing data off the key, and you can continue using the key, writing and reading data from it while you're using it with Predator.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
When you've created the key, insert it and launch Predator if it isn't already running. A green icon will begin flashing in your taskbar. Depending on your settings, the icon will periodically change to red to indicate that Predator is updating your key. Whenever it's green, you can pull the key out to lock your desktop. When you return, simply re-insert the key to reactivate your desktop session.
For added security, you can also configure the software to prompt for a password. If anyone without access to the key tries to use the desktop while you're away, Predator will challenge them to enter a password or enter the key within 20 seconds. If they fail to do so, Predator will display an 'Access denied' message and flood the room with a noxious gas that will incapacitate anyone within five seconds…
OK, it only sounds an alarm. It also records the intrusion attempt in its log, and depending on your edition of the app, alerts you via email or SMS.
The good thing about Predator is that when the key is removed, it blanks your screen, freezes the keyboard and the mouse, and disables the Windows autorun facility. This will prevent someone from installing malware on your locked computer by exploiting the autorun feature, which lets you install software from removable media without the need to touch the keyboard.
Tinkering the setup
To minimise the learning curve, Predator comes with default settings that will work for most users, and there are some settings you should tinker with after you get comfortable with the program and understand basic usage.
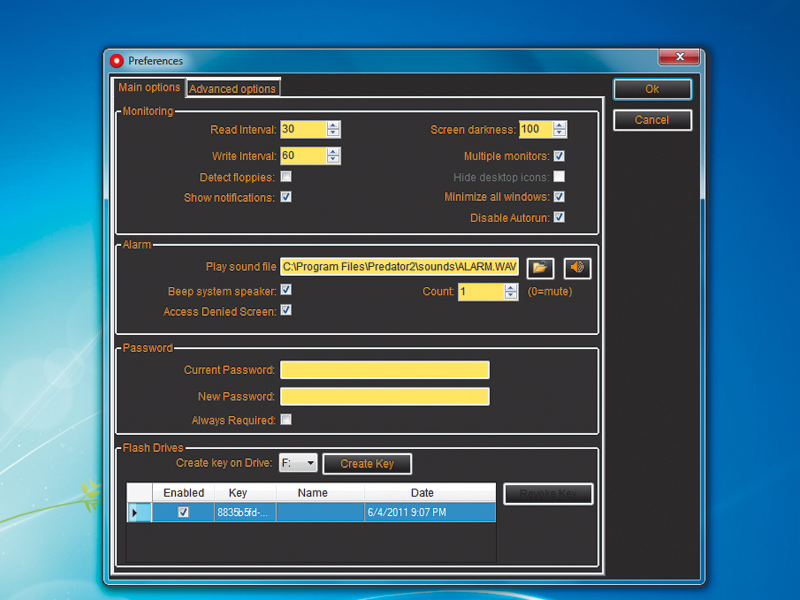
You can access Predator's settings easily by right-clicking its flashing icon in the taskbar and then selecting the 'Preferences' option from the menu. The Preferences window is divided into two tabs that house the main options and more advanced parameters.
In the 'Main options' tab you'll see monitoring options like the read and write intervals. The read interval is the number of seconds after which Predator looks for the key. For example, if this is set to 30, Predator will look for the key every half minute. If you remove it, the Pred will lock your session until you reinsert the key.
The write interval is handy if you're particularly security conscious. This is the time after which Predator changes the security code for the USB key. If someone makes a copy of your key while you're away, the copy will be useless once Predator generates the new code for the original key.
Backups and new access
If you want to give another user access to your computer, or you find that you need to generate a backup key, you can do this by plugging in the new pen drive and selecting it under the 'Flash drives' section. Then click the 'Create key' button to create an additional key. The original and new keys will now be listed.
If you create a backup key, it's prudent to temporarily disable it by unchecking the 'Enabled' checkbox. You can then re-enable it if you lose your primary key. If you lose a key, make sure you revoke it permanently by selecting that key's entry and then clicking the 'Revoke key' button. Now Predator won't allow anyone with this key to unlock your PC.
You can unlock a session without a key by entering the password. When you unlock the session without the key, Predator automatically pauses monitoring. This gives you time to open the Preferences window, revoke the lost key and create a new one.
Also remember that while the Preferences window is open, monitoring is paused. It can also be paused manually from the context menu of the icon in the taskbar. If the 'Show notifications' checkbox is ticked, Predator will periodically remind you that you ought to resume monitoring.
The 'Multiple monitors' checkbox is selected by default. You should leave this option as it is even if you don't have an additional monitor. With this option toggled, if an attacker connects an additional monitor while you're away, Predator will lock the extra display as well.
The other options in the screen are self-explanatory. There are options to change the alarm sound, set its volume, and control the display of the 'Access denied' screen. You can also change the password, and even force Predator to ask you for it.
You can only reset the password from within Predator if you know the existing password, so what do you do if you forget your password? If that happens, you need to use the Predator Administration tool installed alongside Predator. Besides resetting the password, the tool can also be used to reset Predator's settings to their default values, and revoke all USB keys.
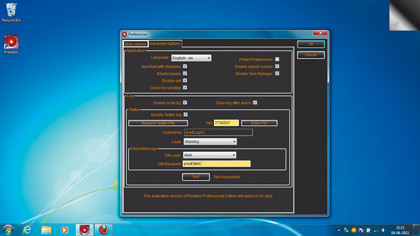
If you aren't too concerned about someone accessing your PC while you're taking a stroll, all you need Predator to do is keep a local log of failed intrusion attempts. Just head to the 'Advanced options' tab in the Preferences window and make sure the 'Enable local log' checkbox is toggled, along with the 'Open log after alarm' box. If someone has tried logging into your PC while you were away, the log will display the log as soon as you reactivate the session.
Hook Predator up to Twitter
If you want to be alerted when someone tries to activate your session, the professional version of Predator can use Twitter to alert you via email or an SMS.
To make this work, you need to register two Twitter accounts. Predator will send log events to one, which will then send a direct message to the other, which will notify you via email or SMS.
The two accounts we registered were predLogAC to log all events, and predDMAC to notify us of intrusions. Ensure the DM account (predDMAC) is following the log account (predACLog). This will let one account send DMs to the other.
Once the accounts are set up, head to the 'Advanced options' tab and toggle the 'Enable Twitter log' box. Click the 'Request Twitter PIN' box, which will open your browser and take you to Twitter's authorisation website. Now log into your Twitter log account (predLogAC). This will display the Twitter PIN, which you should type into the text box in Predator before clicking 'Enter PIN'.
When you've logged into your account, select a filtering level from the pull-down menu. You can choose 'Information', which copies all events from the log; 'Warning', which copies only major events; 'Alert', which copies messages Predator thinks are critical; or 'None', which effectively disables log replication. The default level is 'Warning', but you can change it to 'Information' for more detail.
Now enter the name of the DM recipient (predDMAC, in this case) and select its filtering level. It's wise to keep the log level for the DM account equal to or lower than that of the log account, which notifies you of only a subset of log events. By default, you are notified of only critical alerts.
Log into the Twitter account for your DM user (predDMAC). Head to its Settings page and click the 'Notifications' tab. Make sure Twitter sends you an email when you receive a DM.
For text messages, head to the 'Mobile' tab and enter the mobile phone number Twitter should use. Save the settings and restart Predator, then in the Preferences menu click 'Test'. If it can communicate with Twitter, Predator will display a 'Test successful' message.

With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.