Avoid downloading a bad VPN - these are the warning signs to look out for
Don't waste your money or put your security in jeopardy

With privacy in short supply on the internet, having one of the best VPNs has gone from a luxury to more of a necessity.
Besides, there are plenty of reasons why you need a VPN, such as securing public Wi-Fi, unlocking restricted websites, streaming your favorite shows, sport and films when abroad and, of course, security.
But in the pursuit of the best ones, how do you avoid a bad VPN?
Low level encryption
VPN services are all based around the creation of an encrypted tunnel between the user’s computer and the VPN server. By routing the data traffic through this tunnel, it gains a high level of encryption, making it highly unlikely to be readable - or at least that is the plan.
The issue is that while all VPNs create this encrypted tunnel, the type of encryption and VPN protocols used can vary.
The better VPN services offer power protocols like OpenVPN and Wireguard, which are open source, and supports up to 256-bit encryption of data.
Whenever a product’s is “open source” the code used to design it is freely available online for security experts and the community to examine. This makes it much less likely that any flaws or malicious code will be detected.
One example of this is ExpressVPN, which openly details that the encryption is AES 256-bit, via the OpenVPN protocol.
ExpressVPN also offers its own custom protocol called Lightway, which is also open source and uses powerful encryption. NordVPN also offer their own protocol, Nordlynx, which is itself based on Wireguard.
These are both major, respectable VPN providers, so you shouldn’t avoid using them just because they use their own protocols. Instead, research exactly how much of the protocol is “open source” and whether they support any other protocols.
If your provider supports OpenVPN for instance, you won’t have to rely on installing their ‘client’ software on your device : use an open source client like OpenVPN Connect instead for extra peace of mind.
Slow speeds
As all the data gets routed through the VPN, a robust provider is needed to keep up with your demands. After all, you paid for a certain level of bandwidth from your ISP, and a better VPN should be able to keep up with it, with minimal loss of throughput.
A bad VPN is often oversold, with servers that get overloaded. This then severely limits that bandwidth that can be used, translating to slow browsing, and frequent hiccups when trying to enjoy streaming content.
On the other hand, a reliable VPN provider can actually speed up your connection. This is because some ISP’s actually practise bandwidth “shaping” whereby they deliberately slow down certain web content like streaming video (think Netflix). If you use a good VPN provider, all data will pass through an encrypted tunnel between your device and the VPN server. This means your ISP won’t know exactly what you’re doing so can’t choose to slow down certain types of traffic.
A good VPN provider will also have a number of reliable servers around the world. This means there’s a better chance they’ll be one close by to which you can connect, which reduces latency, so increasing speed.
Free VPNs
That expression about “If the service is free, you are the product,” does apply to free VPNs. After all, it does cost the VPN service money to run, and otherwise how can it maintain profitability?
Many free VPN providers balance the books by selling users’ personal information. Some are open about this in their privacy policy. Some just do it anyway. This is one of the many reasons we say that “free” VPN’s could end up costing you a lot more than you planned.
This is especially true if a “free” VPN hasn’t been set up for good reasons. In September 2022 for instance, a Canadian-based free VPN provider Betternet was alleged to have links to the Iranian government, which strictly censors the Internet.
There have been multiple examples of VPNs that are downright malware. These free VPNs grab user’s data via their software, routing it back to the company, which can then package it and sell it to interested third parties. In 2022, cybersecurity researchers found that some VPN apps available for download via links in SMS or Telegram channels were actually infected with spyware.
This lack of privacy is precisely what a reputable VPN can secure, so be sure to avoid these insecure VPNs, and go only with reputable ones.
You’ve a much better chance of downloading reliable VPN software by using official channels like the Google Play and Apple app stores. Our advice is you should only use these if you don’t mind your personal information being shared over the internet. This may not worry you, if you only want to stream video over the Internet, for instance but we’d still recommend using a paid service.
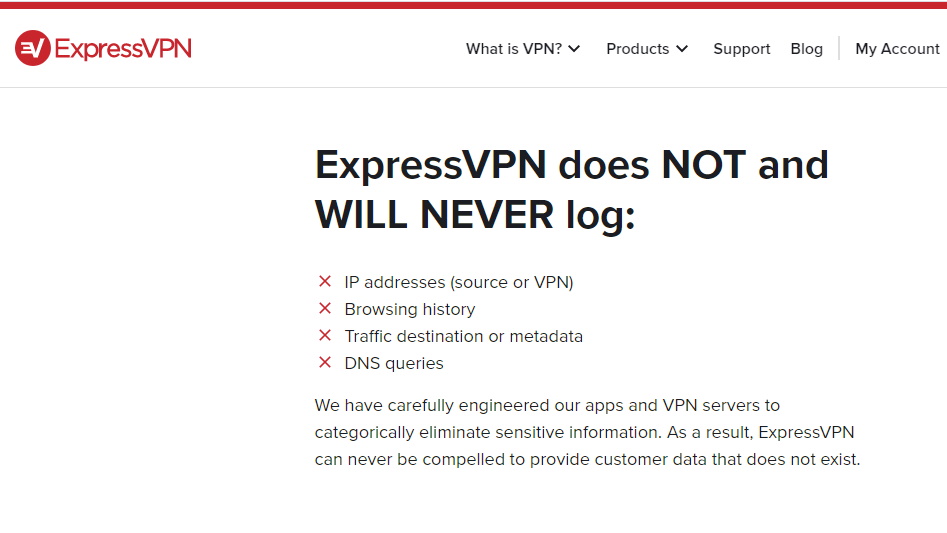
Absent or unclear no logs policy
The key to any VPN is that it indeed provides privacy. An important component of this privacy is that it does not log the data. Many VPN’s claim not to do this through having a “no logs” policy.
Many VPNs in fact do log user’s data, and keep it for some time, which is quite contrary to the privacy that they purport to provide.
Sometimes they do this in an open way and tell you what data they retain: for example any VPN that places a cap on the amount of data you can download per month will need to inspect your data, to see how much has moved across their servers.
Other VPN’s may not do this but could be subjected to a court order to hand over your records. Worse still, some jurisdictions don’t even allow the VPN to inform you that this has happened.
Look for a reputable VPN (e.g. NordVPN or IPVanish) that has a transparent and detailed ‘no logs’ policy.
It should be clearly stated that user data is not logged, and not kept for any amount of time. You should also expect your provider to list exactly what data it doesn’t record and what it does (if any). The policy should also be easily located on the VPN service’s site.
See the screenshot above, which is ExpressVPN’s policy, and demonstrates a solid no logs policy.
Many reliable VPN providers like ExpressVPN, NordVPN and SurfShark also regularly submit themselves to audits. This is where a trusted third-party (such as PricewaterhouseCoopers Switzerland in the case of ExpressVPN) examines the provider’s servers to make sure no personal information is stored.
Of course, this won’t necessarily prevent your VPN provider from being served a secret subpoena to record all your data from now on. The best defence against this is to choose a provider that’s registered in a country which doesn’t have such laws.
Any VPN servers you use in different countries may also be seized under the laws there, so make sure to check with your provider what safeguards they have in place to stop that happening e.g. ProtonVPN operate their own bare metal core servers and based in Swizterland, so it’s very unlikely they could be ordered to hand over/record your data.
You can also gain some peace of mind through using a VPN which has a warrant canary, like NordVPN.
This involves your provider regularly releasing a statement e.g. through a monthly video address on Twitter to say that they have not been subjected to any secret subpoenas or search warrants. Given that they might be under a “gag” order not to inform users that their information is no longer safe, this is a convenient way to let people know. If the canary fails to ‘sing’ each time it's due, you can close your account and switch providers.
Unclear privacy policy
A VPN might have a clear “no logs” policy but will be sketchy when it comes to its overall privacy policy.
There are certain red flags to watch out for. First and foremost you should check using a search engine to see if the privacy policy for this VPN provider has been copied from somewhere else.
For example, you can Google this extract from ExpressVPN’s Privacy Policy (in quote marks):
“We want you to understand what information (including Personal Data) we collect in connection with your use of our Services”
You’ll see that this exact wording has been copied into the privacy policy of another VPN service.
The policy should also be clear and detailed, especially when it comes to how they handle your payment information.
This is extremely important, as no matter how little data your VPN provider keeps on you, they’ll need to have this on file e.g. your credit card number in order to maintain your subscription and comply with local tax laws.
If this is a worry for you, consider using a VPN provider which accepts anonymous payment methods via cryptocurrencies like Bitcoin.
The good, the bad, and the ugly
As you’ve learned, not all VPN Providers offer a reliable, secure service. This is especially true for “free” providers or those offering you “lifetime” memberships.
When choosing a provider, look for clear explanation of the available VPN protocols and links to download client software in the official app stores for your device. Your provider should also have detailed, well-laid out “no logs” and privacy policies.
Any reliable VPN provider will either offer you a free trial or allow you to pay for just one month’s subscription with a refund guarantee if you’re not happy. You should always do this at first to check they’re living up to their promises.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Jonas P. DeMuro is a freelance reviewer covering wireless networking hardware.