AdGuard goes open-source with its custom VPN protocol that can mimic web traffic
TrustTunnel is already being used across AdGuard VPN apps and is now available to "use, run, tweak, extend, and build upon"

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- AdGuard has open-sourced its custom VPN protocol
- TrustTunnel uses HTTP over TLS to mimic normal web traffic
- The open-source code allows in-depth auditing and wider adoption
AdGuard has open-sourced its custom VPN protocol, TrustTunnel, which is designed to enhance privacy and dodge censorship by looking like regular web traffic.
As VPN adoption continues to grow worldwide, governments and organisations have stepped up their efforts to identify and block VPN usage more easily, implementing more and more sophisticated censorship measures. In response, the best VPNs are also upping their game, beefing up their censorship-resistant features as they innovate quickly to stay ahead of the market.
AdGuard follows suit and promises to make your VPN traffic virtually invisible thanks to its proprietary cryptographic protocol based on TLS. While TrustTunnel is already being used across AdGuard VPN apps, it's now available in open source to "use, run, tweak, extend, and build upon," said the provider.
How does AdGuard's TrustTunnel work?
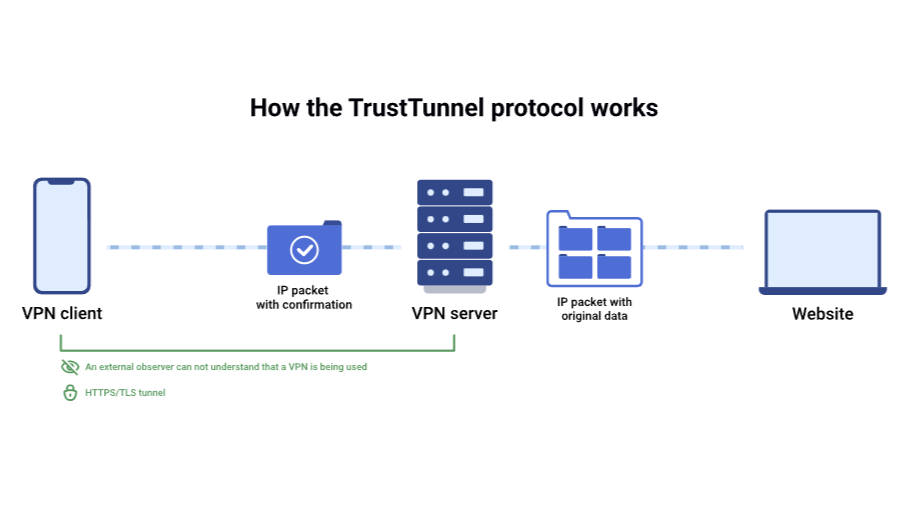
Unlike traditional VPN protocols such as WireGuard and OpenVPN, TrustTunnel uses HTTP/2 and HTTP/3 over TLS to mimic normal web traffic, reducing the likelihood of detection and throttling by ISPs and content providers – AdGuard explains in a blog post.
Governments, websites, and services are becoming more skilled at pinpointing VPN-related traffic on widely spread VPN protocols, even if the actual data remains hidden.
As a result, they can more easily impose traffic restrictions and limit speeds to discourage VPN use for a myriad of reasons, from bandwidth to licensing to censorship. This makes it more likely your traffic will be capped when using a VPN to share files or access restricted content.
AdGuard's HTTP tunnelling aims to make VPN connections less like distinctive VPN traffic and more like normal web browsing, allowing users to access content that is subject to regional restrictions, blocked by governments, or censored.
AdGuard’s move is more relevant than ever at a time when censorship is increasing around the world, with countries such as Russia enacting laws that criminalise the dissemination of information related to circumventing censorship, including the use of VPNs.
From a technical standpoint, the VPN provider also claims that by using both HTTP2 and HTTP3 as transport layers, AdGuard is able to ensure faster, uninterrupted connections, as each connection gets its own HTTP/2 (or HTTP/3) stream, reducing back-end congestion.
In addition, TrustTunnel allows users to create very specific routing rules: a user can decide which apps or websites to route through the VPN and which not to (for example, sending work traffic one way and personal traffic another), increasing user control and customisation over how their Internet data is handled.
Other features include a real-time request log that offers full transparency on where the device sends traffic, how routing rules are applied, and which connections use the tunnel.
An open-source move
The protocol has been active with AdGuard for over a decade, but by making it open source, the ad blocker specialist is now seeking to increase transparency and accessibility in the developer community.
Users can inspect TrustTunnel's code, modify it, and incorporate it into their own projects, allowing the programme to be audited, verified, and refined, strengthening trust among its users and potentially allowing other VPNs to adopt the tunnel.
The VPN provider has also released a client app for iOS and Android that offers advanced users the ability to connect to their home servers while protected by the TrustTunnel protocol.
The app is currently available on Google Play, where it has already racked up hundreds of downloads since its release on Monday.
With the launch, AdGuard joins the list of VPNs offering similar technologies, such as Nord VPN, which last year launched its “revolutionary” NordWhisper protocol, designed specifically to bypass strict network filters. And we expect others to join the list soon.
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!

Silvia Iacovcich is a tech journalist with over five years of experience in the field, including AI, cybersecurity, and fintech. She has written for various publications focusing on the evolving regulatory landscape of AI, digital behavior, web3, and blockchain, as well as social media privacy and security regulations.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.