Creative keyboard attack allows passwords to be stolen using the heat from your fingers
Thermanator wants your keyboard, your body heat, and your passwords…

Security researchers are arguing that passwords represent an increasingly wobbly method of verification, following the discovery of an exploit that can potentially discern a password using the thermal energy residue left on recently pressed keys.
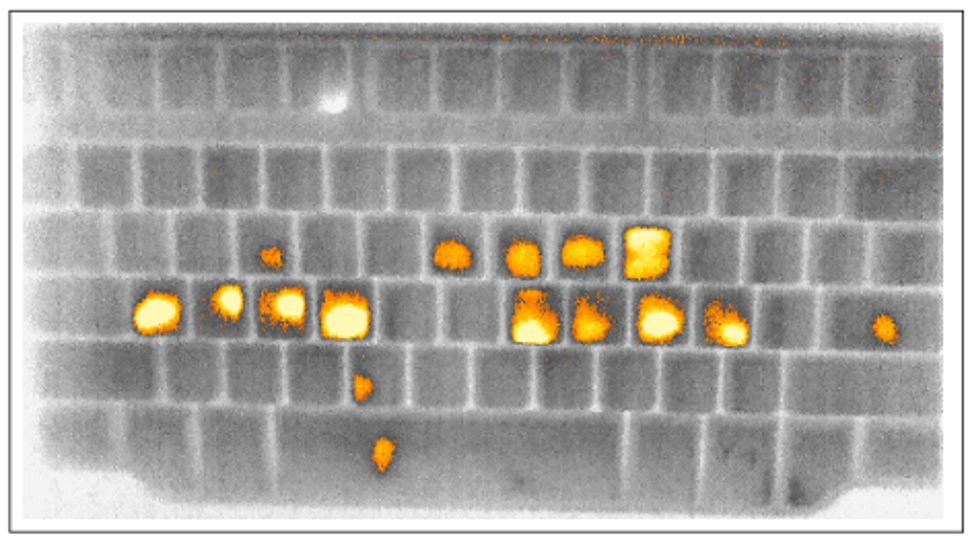
As spotted by Bleeping Computer, computer scientists from the University of California, Irvine (UCI), have named the attack Thermanator, and it involves the usage of a ‘mid-range thermal camera’ to scan the keys and detect the heat residue left on them.
Gene Tsudik, a computer science professor at UCI, observed that an attacker could “capture keys pressed on a normal keyboard, up to one minute after the victim enters them”. He added: “If you type your password and walk or step away, someone can learn a lot about it after-the-fact.”
Of course, this is not a trivial exploit to pull off. The attacker needs to have the thermal camera in place with a clear view of the keys, and there’s a time limit as the heat residue fades, as mentioned. But if the attacker moves quickly enough – i.e. within 15 seconds or so – the thermal imprints left are quite strong.
If the keys used to type the password are discerned, the attacker can later crunch this data and engage in a dictionary attack (repeatedly trying combinations) to brute force the login in question.
The researchers ran laboratory tests, and the paper on the exploit observed that: “Entire sets of key-presses can be recovered by non-expert users as late as 30 seconds after initial password entry, while partial sets can be recovered as late as one minute after entry.”
The researchers also found that ‘hunt and peck’ (i.e. two finger) typists were more vulnerable to this exploit, as the thermal traces they left when typing were stronger.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
So is this a good reason to learn to touch type? Well, in all honesty, the odds of you being hit by this sort of attack in a real-world situation are vanishingly slim, at least right now – but it does point the way to the perils of the future.
Mission: Possible
And it’s not unthinkable that this sort of thing could happen in the near future. The researchers noted: “As formerly niche sensing devices become less and less expensive, new side-channel attacks move from 'Mission: Impossible' towards reality. This is especially true considering the constantly decreasing cost and increasing availability of high-quality thermal imagers.”
If you’re concerned, one mitigation technique the researchers offer up is simply to run your hands across the keyboard after a password entry in a public place. It’s also a good idea to never leave your notebook unattended in public, too – but that’s just general good security practice.
There are other potential vulnerabilities here aside from laptop or PC keyboards, and thermal imaging tricks could be used to try and discover PIN numbers at ATMs, for example.
Furthermore, there are a range of other exploits to determine key presses and work out passwords, too, such as using the physical vibrations made by tapping the keys. Going forward, the researchers argue that traditional passwords need to be consigned to the dustbin, in favor of more secure methods of authentication like biometric.
- Even the best laptops require good security practices
Darren is a freelancer writing news and features for TechRadar (and occasionally T3) across a broad range of computing topics including CPUs, GPUs, various other hardware, VPNs, antivirus and more. He has written about tech for the best part of three decades, and writes books in his spare time (his debut novel - 'I Know What You Did Last Supper' - was published by Hachette UK in 2013).