Garmin down: what happened during the outage
On July 23, Garmin services went down. Watches, bike computers and other devices had stopped uploading data, and the Garmin Connect app began displaying a message explaining that the sudden outage was due to ‘maintenance’. Pilot software and navigation database FlyGarmin (used for Garmin navigational systems) also went down, reportedly resulting in the grounding of some planes.
A tweet from the brand confirmed that it was “experiencing an outage that affects Garmin Connect, and as a result, the Garmin Connect website and mobile app are down at this time”, but as the outage stretched on, speculation began to circulate that it wasn’t just a technical problem, but the result of a ransomware attack that had encrypted critical data in Garmin’s systems.
We’d like to thank all of our customers for your patience and understanding. For more information, please visit https://t.co/U3vwBre4U2.July 27, 2020
What happened
Sources claiming to have first-hand knowledge of the situation told BleepingComputer that company data had indeed been encrypted, and the attackers were demanding a ransom to release it. The sources shared screenshots (allegedly from Garmin’s systems) showing files locked under the name ‘GARMIN.WASTED’.
ZDNet cited a report from Taiwanese technology site iThome, which claims a memo was sent to Garmin's Taiwanese production facilities saying that 'servers and databases' were attacked, and that production lines were being shut down for two days while they recovered.
The possibility of such an attack was very worrying. Garmin holds a lot of personal data on its customers – names, birthdays, contact details, GPS data and health information – and ransomware creators don’t always simply encrypt their targets’ data. If the ransom goes unpaid, they might then sell or leak it online.

TechRadar spoke to the brand after 48 hours of the outage and received a statement confirming that most of its customer services were still offline:
”Garmin is currently experiencing an outage that affects Garmin services including Garmin Connect and Garmin Pilot. As a result of the outage, some features and services across these platforms are unavailable to customers. Additionally, our product support call centers are affected by the outage and as a result, we are currently unable to receive any calls, emails or online chats.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
“We are working to restore our systems as quickly as possible and apologize for the inconvenience. Additional updates will be provided as they become available.”
The brand then directed TechRadar to a short Q&A, which reassured users that “Garmin has no indication that this outage has affected your data, including activity, payment or other personal information.”

On July 27, four days after the outage began, Garmin Connect services started to come back online, and the company finally confirmed that it had been the victim of an attack that had encrypted its data (though it stopped short of mentioning whether the attackers had demanded a ransom):
"Garmin [...] today announced it was the victim of a cyber attack that encrypted some of our systems on July 23, 2020. As a result, many of our online services were interrupted including website functions, customer support, customer facing applications, and company communications.
"We immediately began to assess the nature of the attack and started remediation. We have no indication that any customer data, including payment information from Garmin Pay, was accessed, lost or stolen.
"Additionally, the functionality of Garmin products was not affected, other than the ability to access online services.”

On July 30, as services continued to resume, Garmin’s president and CEO Clifton Pemble addressed the attack in a speech at the company’s annual earnings call.
"[...] Most of you are aware of the recent cyberattack that led to a network outage affecting much of our website and consumer-facing applications," Pemble said. "We immediately assessed the nature of the attack and started remediation efforts. We have no indication that any customer data was accessed, lost or stolen.
"Additionally, the functionality of Garmin products was not affected other than the ability to access some online services. Critical affected business systems have been restored, and we expect to restore remaining systems in the coming days. We appreciate the patience and kind words of support we've received from customers and friends during this challenge."
Is my data safe
It seems so. Garmin has taken every opportunity to reassure its users that their data hasn’t been compromised, and a recent report from TechCrunch, citing two sources it claims have ‘direct knowledge of the incident’, says that the ransomware used doesn’t appear to be able to steal or pull data from locked files.
Your day-to-day data during the outage was saved on your device - whether that's your body battery, stress levels or your daily step counts - and that data should now be syncing with Garmin’s servers.
What about Strava?
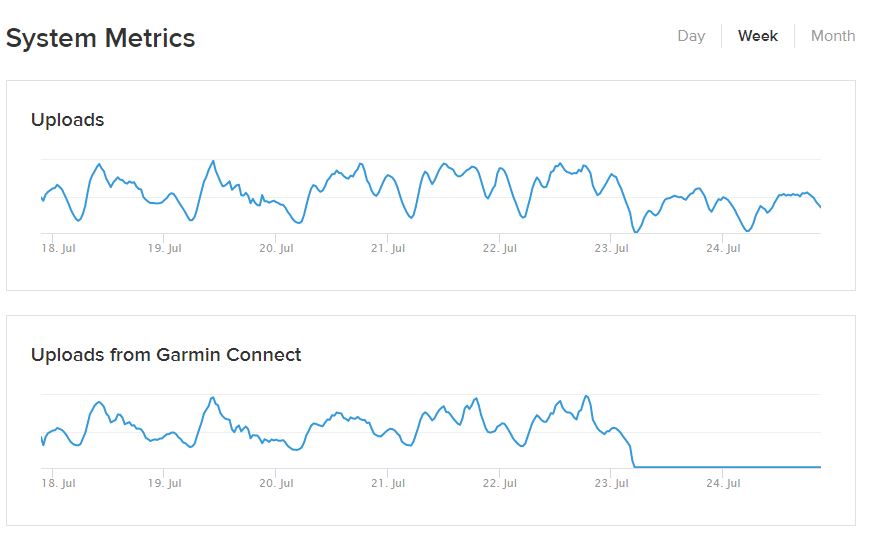
Strava wasn’t directly affected, but workouts recorded using Garmin devices weren’t uploaded during the outage. A graph of its Strava’s statistics shows a complete drop-off in activities from Garmin from July 23, and overall uploads dropped by a third.
Workouts gradually began to sync to Strava on July 27, but Strava warned that due to the sheer size of the backlog, it could take a week or even longer for all activities to sync, so don’t worry if yours have been slow to appear. If you can't wait that long, you can upload your activities to Strava manually.
Who was behind it?
It's not been confirmed, but the name GARMIN.WASTED given to the locked files suggests that the ransomware in question is a variant of WastedLocker, which is operated by a Russian gang known as Hacking Corp and can be tailored to attack very specific targets. As Sky News reports, the group’s members were sanctioned by the US treasury last year of committing "two of the worst computer hacking and bank fraud schemes of the past decade".
If correct, this could have put Garmin in a very difficult place. The sanctions prohibit US persons from engaging in transactions with the criminals – and as Garmin is a US company, paying a ransom to unlock files might be just that. However, it’s not clear whether this would apply when a business or individual is being extorted, but anonymous sources speaking to Sky said that Garmin had not made a direct payment to its attackers to release its data.
What is ransomware?
Ransomware is a type of malicious software (malware) that encrypts data, rendering it useless until the victim pays a fee for the decryption key. Payment is demanded in Bitcoin so it can’t be traced, and goes towards funding criminal activities. There’s also no guarantee that paying up will allow you to recover your data.
Home users can be affected by ransomware, but gangs find it much more lucrative to target companies that hold a lot of sensitive data and have pockets deep enough to pay a hefty ransom.
As Malwarebytes explains, WastedLocker attacks demand ransoms ranging from $50,000 (about £40,000, AU$70,000) to over $10 million (about £8 million, AU$14 million) in Bitcoin.
Removal tools do exist, there are so many different strains of ransomware that encrypt files in different ways, you can only decrypt your files if you know exactly what you’ve been infected with, and a developer has been able to build a fix for it.
The best way to deal with ransomware is to be proactive and regular backups, so you can restore your files without paying the fine. These backups should be kept completely separate from the rest of your system, otherwise they could be encrypted too.
Attacks can be tailored for a particular organization or even a specific person, who might receive the ransomware installer as part of a very authentic looking email from a colleague, full of information that a third party wouldn’t be likely to know.
"Ransomware attacks are frighteningly common," computer security expert Graham Cluley told TechRadar. "It's been one of the biggest types of cybercrime in the last few years. They hit both individuals and organizations, and have sometimes netted cybercriminals millions of dollars."
"Obviously not everyone can afford to pay - which means they may not only lose precious work, but irreplaceable files of sentimental value such as family photographs. The moral? Make regular secure backups and ensure that they work.”
- Now that services have resumed, check out our guide to the best Garmin waches

Cat is TechRadar's Homes Editor specializing in kitchen appliances and smart home technology. She's been a tech journalist for 15 years, having worked on print magazines including PC Plus and PC Format, and is a Speciality Coffee Association (SCA) certified barista. Whether you want to invest in some smart lights or pick up a new espresso machine, she's the right person to help.