Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Imagine a world where people can easily copy your front door key, just by watching you use it a few times. Or where people only use a few base front door keys, so someone trying to break into your house could just guess which key you happen to be using.
On top of that, you're using the same front-door key for your car, to open your safe and to get into work. Why are you being so lax with your key? Protect it!
This is exactly what you're doing when you use the same passwords to log into WoW, Steam, Origin, Google, PayPal, your bank, Windows, that forum you can't talk about - the list goes on. Worst-case scenario is using 'password' as a password or the favourite - as revealed by surveys - '123456'.
There are tricks and tactics for making stronger static passwords, but no matter how long, how complex, how impossible to guess a password is, a static password is always vulnerable to many types of attack.
Putting aside brute-force attacks and other hacks, there are still malware keyloggers, someone watching you, a social engineering attack or someone finding a post-it note that has the password written on it.
Adding factors
These types of regular breaches have made services - usually where money is involved - look at ways to strengthen the password, aka user authentication. This area of security is known as multi-factor, or more commonly two-factor, authentication and refers to the user having to prove who they are in two or more ways.
The traditional static password is a single-factor system: enter your user name, prove who you are with a secret password and you're in. The glaringly obvious flaw is if an attacker can learn the password - through fair means or foul - they can gain unfettered access to the account.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
A two-factor approach requires the usual user name and static password as the first factor, but then an additional authentication factor that is one of three things: something you have, like a device, something you are, such as a fingerprint, or something you know, such as a further pin or other challenge response.
The solution most companies are opting for is the first, something you have, and they use it to supply what is known as a one-time password (OTP). These are passwords that are used just the once. The whole system hinges on passwords being generated on the fly using a cryptographic algorithm; these can be time-based, part of a pseudo-random sequence or based on a supplied random code.
Smarten up
The genius part of this is that with the wide use of smartphones, companies can use your mobile as the second-factor, delivering the one-time password (OTP) via an SMS, email, push-message or a dedicated app. Generally this makes it easy for both you and the company to implement the OTP system.
Setting up such a secure system is easy: you register, a secret key is sent to your phone and from then on only your phone will be able to generate the correct one-time password. As you can imagine, even if someone has your user name and standard password without the device they will never be able to log in. It's not even possible to brute-force crack it as the OTP changes with time.
Such systems have already been rolled out by quite a number of high-profile online services - usually as an optional secure system but often with banks as a mandatory system - such as Google, Facebook, Blizzard with World of Warcraft, PayPal and HSBC, to name just a few. Once in place, you'll always need the addition of the OTP supplied via your phone or whatever verification device has been supplied.
Downsides
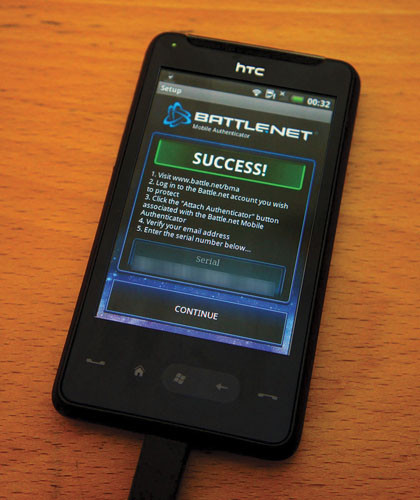
Of course there are downsides to this. If you're stuck without your verification device then no access for you. In the case of your mobile phone this would be less likely as it's something you'll carry around with you.
However if the OTP is delivered live and you're in an area with no signal, again no OTP for you. Many systems use a locally generated code so signal is not a problem. What is a problem is if your phone is stolen or lost. Systems are in place for dealing with that, but again these can weaken what would be otherwise a secure system.
There are also middle-man attacks that use social manipulation to extract the OTP from the user, under the guise of a system test, for example. Even so, the window of opportunity for an attacker to exploit vulnerabilities in the system are massively reduced, down to having to steal the authentication device, trick you into handing over a live OTP or subvert the recovery process that usually triggers a warning message being sent to your email account and authentication device.
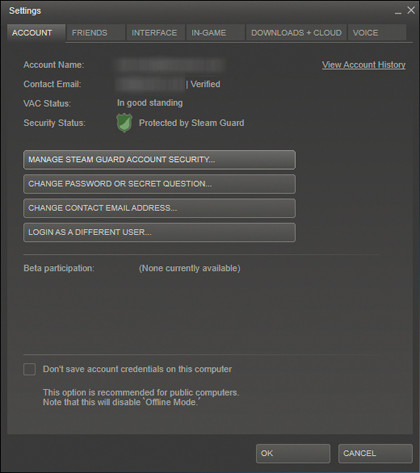
Steam Guard
Steam has beefed up its security around accounts and log-in procedures, but doesn't require any additional authentication devices. So how secure is that?
We've talked a lot about one-time passwords and two-factor authentication: as it turns out Steam Guard is a two-factor system, but the second factor is your PC, which is something you have.
Using a combination of hardware configuration, if Steam detects someone attempting to log into your account on an unauthorised system, a OTP is emailed to your nominated email account, which then must be entered before Steam allows access. This enhances security as it requires the attacker to have additional information, including knowing what email account you use, plus the user name and password for that.
As long as you're not using the same Steam and email password, security is enhanced though the reliance on a personal email to deliver any necessary OTP is the weakness in the system.
As with most of these systems, Steam Guard is entirely optional, at least at this stage. It can also be turned on or off and enables you to deauthorise all other computers than the one you're currently using. This does provide a good level of flexibility, as it's something you can enable when you know you'll be travelling away from home. Once you get back, just in case anyone was trying to hijack accounts, you're able to deliberately deauthorise all the systems you've used.
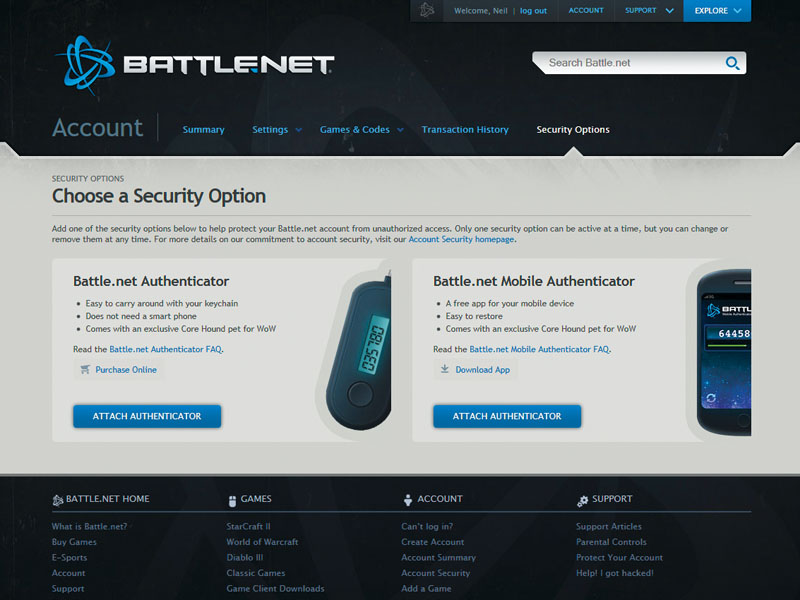
How to secure your WoW account with an authenticator
1. Security upgrade
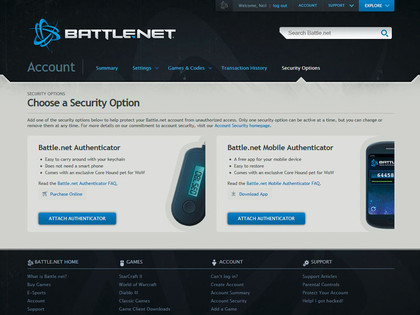
Quickly to Battle.net! You should see on the left an Account Security heading; click the Manage Security Options link. Blizzard offers two options: a paid-for key-fob or a free phone-based app. The latter supports Android, iPhone/iPad, BlackBerry and Windows Phone 7. So get downloading!
2. Be verified

Click Attach Authenticator and if it's not already you'll need to first verify your current email as being valid. At this point you'll need to turn to your phone and start setting the Battle.net app up correctly. It'll provide you with a key and a passcode that are entered into Battle.net.
3. Get gaming
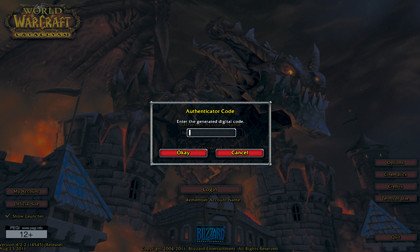
And you're done. The phone app and your account are now linked. The app produces time-based codes that correlate to when you have to log into your WoW account. Without the phone with the correct key, you won't be able to log into the account. So it's as safe as houses.
------------------------------------------------------------------------------------------------
First published in PC Format Issue 259
Liked this? Then check out The best PC upgrades for gamers
Sign up for TechRadar's free Week in Tech newsletter
Get the top stories of the week, plus the most popular reviews delivered straight to your inbox. Sign up at http://www.techradar.com/register
Follow TechRadar on Twitter * Find us on Facebook * Add us on Google+