NordVPN blocks 90% of phishing sites and earns AV-Comparatives certification – again

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- NordVPN has been recognized for its ability to detect and block phishing websites
- NordVPN’s Threat Protection Pro blocked 90% of phishing websites in the test
- Threat Protection Pro is available for NordVPN Plus, Complete, and Ultra subscribers
NordVPN’s phishing protection has been again certified by AV-Comparatives, further cementing its status as the best VPN on the market today. This adds to the growing evidence of the effectiveness of NordVPN’s anti-malware tool, Threat Protection Pro.
AV-Comparatives, an independent testing lab, had already recognized Threat Protection Pro’s ability to detect and block phishing websites in 2024. A repeat result in 2025 sees NordVPN awarded an anti-phishing certification for the second year running.
Threat Protection Pro detected 90% of phishing URLs in AV-Comparatives comprehensive testing, well ahead of the 85% minimum required to earn the anti-phishing certification. The news means that NordVPN is still the only VPN with certified phishing protection.
How Threat Protection protects you from phishing sites
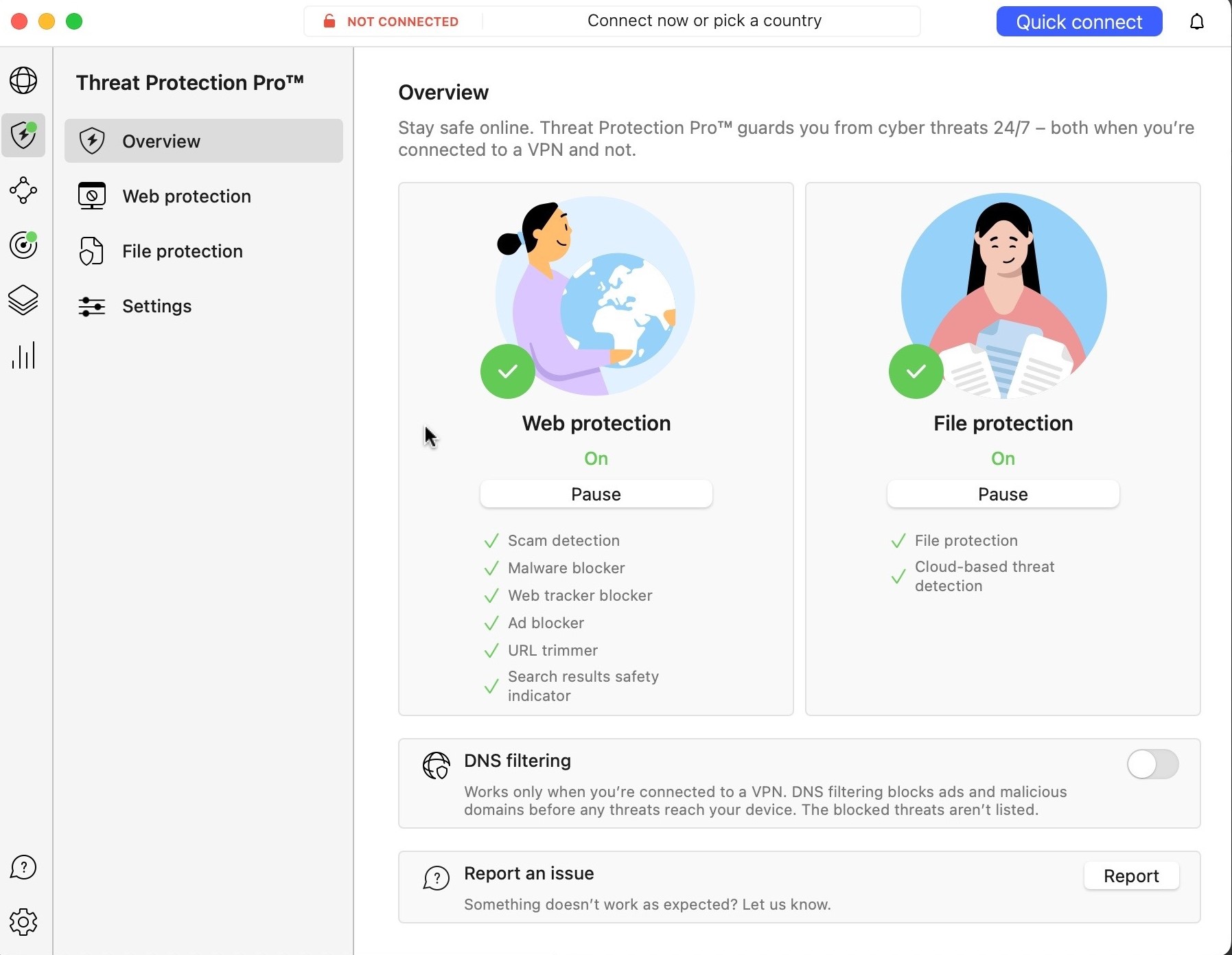
Introduced to NordVPN’s feature lineup in June 2024, Threat Protection Pro helps NordVPN users avoid not only phishing attempts, but a variety of other online dangers including tracking, malware, ads, and scams.
"Phishing websites are one of the biggest threats to internet users worldwide. They steal personal data, login credentials, and financial information from unsuspecting users," said Product Director at Threat Protection, Dominickas Virbickas. "We put our greatest effort into protecting our customers from the consequences caused by these sites."
Threat Protection Pro is available with NordVPN Plus, Complete, and Ultra subscription plans. Subscribers to the Basic tier won’t have access to Threat Protection Pro and its independently certified phishing protection but do benefit from Threat Protection.
Not to be confused with Threat Protection Pro, Threat Protection is a DNS filter capable of blocking ads and malicious domains. In contrast, Threat Protection Pro works at the URL and Javascript level and, unlike Threat Protection, doesn’t require you to be connected to a NordVPN server to benefit from its protection.
NordVPN is still the only VPN with certified phishing protection
This isn’t the first time NordVPN’s Threat Protection Pro anti-malware tool has been recognized by AV-Comparatives.
In 2024, it ranked as the third-best software for avoiding online shopping scams out of 35 competitors, emerging as a top tool for avoiding online shopping scams.
Two more independent audits further confirmed NordVPN's blocking capabilities. Experts at AV-Test awarded NordVPN as the winner among five recognized VPN providers. During testing from West Coast Labs (WCL), NordVPN scored a hugely impressive 99.8% malware protection rate.
What else you can do to prevent phishing attacks
Threat Protection Pro has been proven to offer a solid line of defence against increasingly sophisticated phishing attacks. However, there are still some things you can do to further reduce your risk of falling victim:
- Think before you click. Tell-tale signs of phishing attempts include poor spelling or grammar. Scare tactics are also common in an effort to prompt you into action. When in doubt, re-read messages and carefully check the sender’s contact information.
- Enable two-factor authentication. Make use of two-factor authentication (2FA) which adds an extra layer of security to your online accounts. It requires you to provide an additional method of authentication to log in, such as a code sent to your phone.
- Check for HTTPS. Get in the habit of checking URLs in your browser’s address bar. When you do this, check for HTTPS and confirm the domain is correct. Some URL changes can be difficult to detect such as a number “1” instead of the letter “l”.
- Keep devices and software up-to-date. Phishing attacks may look to exploit unpatched vulnerabilities. Keeping your devices and software updated via official sources helps close off these vulnerabilities.
- Verify the source. Phishing often relies on impersonation with messages designed to look like they’ve come from someone you trust. If at all suspicious, you should avoid clicking or replying and instead contact the person or organization via official channels to verify the message’s authenticity.
You might also like

Mark is a Tech Security Writer for TechRadar and has been published on Comparitech and IGN. He graduated with a degree in English and Journalism from the University of Lincoln and spent several years teaching English as a foreign language in Spain. The Facebook-Cambridge Analytica data scandal sparked Mark’s interest in online privacy, leading him to write hundreds of articles on VPNs, antivirus software, password managers, and other cybersecurity topics. He recently completed the Google Cybersecurity Certificate, and when he's not studying for the CompTIA Security+ exam, Mark can be found agonizing over his fantasy football team selections, watching the Detroit Lions, and battling bugs and bots in Helldivers 2.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.