Who's hacking your PC?
Watch a Hollywood film and it'll depict hackers as fast-talking American kids – pale faced, coke swilling, super-smart and capable of doing the impossible. This is, of course, a fiction.
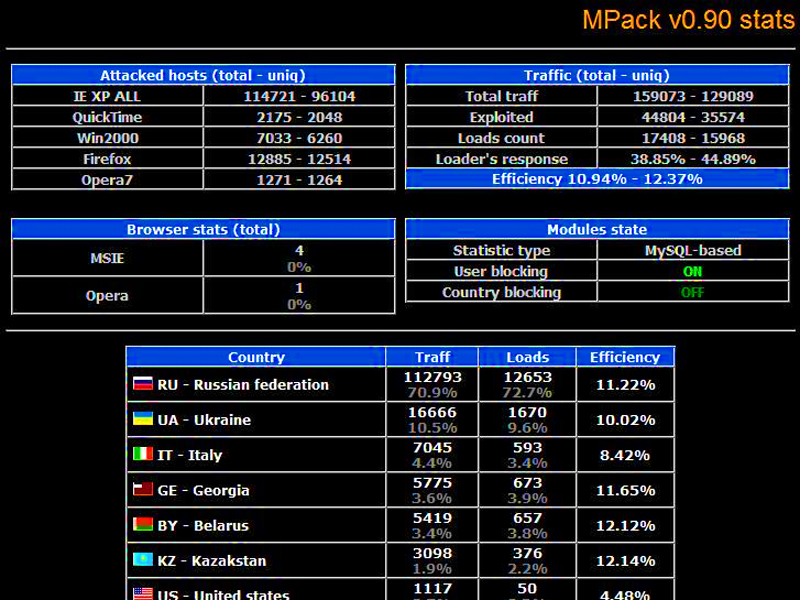
If you were a career computer criminal, would you choose to base yourself in a country with mature computer crime laws and strong-arm enforcers? No. You'd want to be somewhere comparatively lawless. If you're looking for hackers, look east – towards China and Russia – and you'll be barking up the right tree.
That's what the analysts say. But even here myths and rumours get in the way. The Berlin Wall may have fallen but the KGB is still alive and clicking. Beijing has an army of hackers eyeing the West's data. Stories of dark doings and espionage at the keyboard abound. The truth, however, is hard to come by.
Take Russia. While there's no doubt that the ex-Soviet state is genuinely computer-savvy, is there any hard evidence that it poses a greater threat to your PC than, say, South America? In case you're wondering, Brazil is regarded as a leader in banking trojan technology.
Are the Russians phishing like there's no tomorrow? Or are security firms reviving Cold War paranoia in the hope of making 'the enemy' look bigger and uglier, all in order to sell us antivirus software?
The code war
Boris Miroshnikov seems almost proud of the criminals that he chases through cyberspace. He's a Lieutenant General with the Russian police's Department K, which fights domestic cybercrime. Speaking at the 2005 E-crime Congress in London, Miroshnikov told delegates: "Our software writers are the best in the world; that's why our hackers are the best in the world."
Sign up for breaking news, reviews, opinion, top tech deals, and more.
"You're right in thinking that Russia and Eastern Europe are playing a big role in organised webcrime," says Con Mallon, Symantec's Product Marketing Director for Europe, the Middle East and Asia. "Information made public by various arrests of underground economy groups suggests that groups in Russia and Eastern Europe are more organised and professional operations, and that they also possess greater abilities and manufacturing facilities to mass-produce physical credit and debit cards."
Many Russians have been convicted for cybercrime in the past decade. Vasiliy Gorshkov and Alexey Ivanov are from Chelyabinsk, 75 miles from the Kazakhstan border. In 2001, the FBI tricked them into visiting the USA, where they were arrested and charged with 20 counts of conspiracy, fraud and other offences.
In 2004, Department K broke up a criminal gang that had extorted money from nine British bookies, causing a total of over £45million in lost business. And after extorting more than £2million from British companies in 2006 using distributed denial of service (DDoS) attacks, Ivan Maksakov, Alexander Petrov, and Denis Stepanov were convicted after an international effort by Interpol, the FBI and the UK's now-defunct National High-Tech Crimes Unit.
During their six-month spree, the gang launched over 50 blackmail attempts in 30 countries. When UK based bookmaker CanBet Sports refused to pay the $10,000 demanded, the subsequent DDoS attack saw the company lose around £100,000 per day.
In May 2007, Estonia came under a concerted botnet DDoS attack that knocked out the tiny Baltic state's government, media and business websites, halting its largely web-based banking systems. Similarly, during the Russian invasion of Georgia last year, hackers poured DDoS traffic into the troubled country in order to knock out its infrastructure. But were these hackers Russian?
Reasonable doubts
Ken Munro is Director of the Penetration Testing Division of the National Computer Centre (NCC). "The people who do use botnets are extortionists, and we know there are huge volumes of compromised machines out there, synchronised, ready to run, and you can point them wherever you like," he says. "Who's to say that [the Georgian attack] wasn't another foreign power trying to undermine the Georgian government, and it just happened to coincide with the Russian attack?"
The problem with botnets is that the infected computers could be anywhere. As a result, it's difficult to quantify the amount of cybercrime originating from Russia. "I'm not going to give you a figure," says Munro. "The problem with all these things is that no one genuinely knows. And even with vendors who give you numbers, all they're relying on is what they perceive to be the source IP addresses. That means absolutely nothing, because anyone could use an open proxy on a compromised machine and relay their traffic to any other system in the world."
Even if you trace malicious traffic back to a single machine, it might not be the real source. "It could be some poor home user who's got an XP system sat there on the internet and doesn't know they're being used as a back door," confirms Munro. "So, there's almost no confidence in the statistics."
There's no denying that press reports of Russian hacker convictions are true and that they're on the rise, but there have also been plenty of non-Russian convictions over the last decade. Some of the crimes perpetrated by US and non-Russian European hackers have been very sophisticated.
Take Gabriel Bogdan Ionescu, for example. He's a 22-year-old Romanian currently serving three years in an Italian prison for setting up a cloned copy of the Italian Post Office's website and siphoning off money in a sophisticated phishing scam.
Meanwhile, in the US, Robert Moore was convicted of what, to most people, looked like an ingenious scheme to steal VoIP services and sell them through a second company. In an interview before he was due to start a two-year prison sentence, he described what he had done as being "so easy a caveman could do it". In all, Moore broke into 15 telecommunications providers and "hundreds" of private companies.
And Kiwi hacker Owen Walker, who was convicted in April 2008, managed to create a botnet of 1.3 million compromised computers as his part of a large online crime ring. The botnet was used to siphon off millions of dollars from unsuspecting users' bank accounts.
The now-infamous Estonian DDoS attack of 2007 was initially linked to the Russian government by the press. However, a subsequent investigation revealed that it had been perpetrated by an impromptu 'flashmob' who were angry at the removal of a Russian war statue in the Estonian capital Tallinn. Though the first person to be convicted of the attack, Dmitri Galushkevic, was Russian by birth, he lived in Estonia and attacked from within.