How to repair a malware-damaged PC
What to do if you remove a virus and your PC still won't work
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Removing malware is usually a fairly straightforward process, at least once you've equipped your PC with a good antivirus tool. In just a click or two it'll be scanning your system, with any threats being safely despatched in just a few minutes.
Security packages aren't so good at repairing the damage that the malware might have done, though - and removing the infection may occasionally cause even more problems.
You may now be virus-free, then, but find that some programs don't work as they should, or others won't run at all. Perhaps Windows is behaving strangely, you're seeing odd error messages, in some cases your internet or network connections are broken - these issues can be major. But don't worry, there are two clear paths you can take.
The first option is to recover your PC to a known, virus-free state, either by restoring a pre-infection full system backup or reinstalling Windows. This will plainly be a major hassle, but at least when the process is complete then you'll know your system will be back to normal.
And the second option, which we'll be discussing here, is to try to manually identify and repair whichever areas the malware has damaged. This approach doesn't offer any guarantees: you might spend hours trying to figure it out, and end up having to reinstall Windows anyway.
In many cases, though, even apparently major virus damage can be repaired in just a few minutes, once you know the right tricks, and so in general we think this is always worth a try.
First steps
If your antivirus software says it's removed an infection, but your PC is still misbehaving, then the first question to ask is whether there's still some active malware causing problems.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Try running a deep scan with every detection option turned on, just to see what happens. And maybe get a second opinion from another package. G Data's antivirus is highly accurate, for instance (just install a trial), while Malwarebytes Anti-Malware is an effective free tool.
CLEAN UP: Don't start repairs until you've confirmed that your PC is virus-free
Keep in mind that having multiple antivirus tools on your system can cause problems, though, so you may want to remove your existing antivirus package before installing something like G Data's engine.
Or, if you've already installed several security packages in an effort to remove the original infection, then conflicts between them may be why your PC appears to be damaged. Choose just one package, uninstall everything else, reboot and see if that helps.
We would also recommend having Windows check itself for missing or corrupt files. It's easy: just click Start > All Programs > Accessories. If you have XP, click Command Prompt, while under Windows 7, right-click the Command Prompt link and select Run As Administrator. Once the window is open, type SFC/ SCANNOW and press [Enter], and wait to see what the program reports.
Nothing helps? Then you'll want to try a few manual fixes of your own. Some can be risky, so create a system backup, if you don't have one already - but then it's time to begin.
Restore default settings
What looks like virus-related damage to your PC can sometimes just be unauthorised changes to a few key settings, in which case restoring the Windows defaults may help you get things working again. (Of course you'll also lose any customisations you've made, so only apply these tweaks when you're sure they'll apply to an area where you're having problems.)
Is there something wrong with the Start menu, for instance? Right-click the Start button, click Properties > Customise > Use Default Settings and see if that helps.
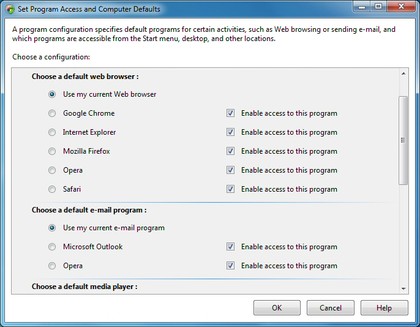
RESTORE: The Default Programs applets can restore your default browser, email client, media player and more
Malware will often mess with Explorer's settings, but again they're easy to recover: just click Tools > Folder Options, then click Restore Defaults in the General, View or Search tabs.
Maybe you've found the correct program isn't loading when you want to view a file, open a web page, send an email or something similar? Click Start > Default Programs. Choosing "Set program access and computer defaults" lets you choose your default browser, email program, media player and more, all in one operation; or clicking "Set your default programs" allows you to make a particular application the default for all the file types and protocols it can handle.
If Internet Explorer isn't working, then go to Control Panel > Network and Internet. If you have an idea what's wrong then you could try to restore the relevant settings individually, so for example clicking Internet Options > Security and clicking "Reset all zones to default level" (if it's greyed out, don't worry, that means the settings are the defaults).
Alternatively, there's always the nuclear option, clicking Internet Options > Advanced > Reset. This will recover all IE's settings to their defaults, but it'll also wipe your cookies, remove installed add-ons, delete your web history and so on, so it's really a last resort.
Remove system policies
Another common malware trick involves setting system policies to prevent users from running certain programs, seeing particular Windows applets or carrying out other normal Windows maintenance tasks.
If you can't run the Registry Editor, for instance, download the free lite edition of Registrar Registry Manager, and browse to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System and HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System, deleting the DisableRegistryTools value if it's present in either key.
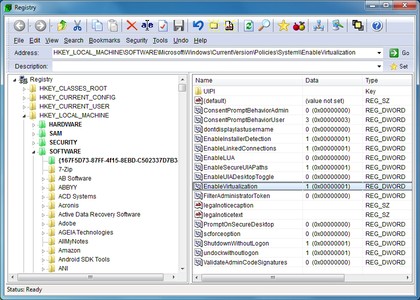
RUN REGEDIT: Can't run REGEDIT? This free Registry editor will quickly save the day
You can't launch Task Manager? Look for and delete the DisableTaskMgr value in the same keys.
If you find you can't run particular programs, check HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer (and the HKEY_CURRENT_USER version) for a RegistryRun value, and delete it if present.
And there are many other possibilities. If you're running a high-end version of Windows - Professional, Ultimate, Enterprise - then try running the policy editor (GPEdit.msc). Going to, for instance, User Configuration\Administrative Templates\Windows Components\Windows Explorer will show you many common restrictions, which you can then reverse from the editor.
Otherwise, simply browsing beneath HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies may offer some clues. If you can't see the Folder Options setting in Explorer, for instance, finding a Policies\Explorer\NoFolderOptions value will tell you why - delete it and reboot.
Don't simply wipe everything out, though, as that may lead to undesirable side effects: enter the name of any policy value at Google first, to be clear that you understand it, before deleting anything.
Resetting the network
Sometimes removing deeply embedded malware can break your network connection to the point where you're no longer able to see local machines, or maybe even access your internet connection.
If you're using the Windows firewall, you might want to start by using the "Reset Defaults" link in its Control Panel applet. (If you've tweaked the firewall settings to allow particular applications to work then those settings will now be lost, though - you'll have to apply your tweaks again.) Reboot and look for any changes.
RESTORE DEFAULTS: It only takes a moment to reset the Windows Firewall. Be careful, though, this may break other programs
If that doesn't help, click Start > All Programs > Accessories > Command Prompt, and in the command window type
netsh int ip reset c:\resetlog.txt
(replacing c:\resetlog.txt with an appropriate drive and file name for your PC, if necessary) and press [Enter]. This resets TCP/IP, and if you reboot then your system may be working again.
Failing that, open the command window again, entering
netsh winsock reset
and reboot. This removes many networking addons, which is great for problem-solving, but also may be enough to break other low-level networking tools, like firewalls. Reinstall any programs which stop working and they should be fine.
Recovery tools
If all these manual fixes sound a little too much like hard work, then there are alternatives: free tools which will reset various Windows settings to get your PC working normally again.
At least, that's the plan. We would treat these very much as a last resort, though, because if any of these programs includes a bug, maybe tweaks the wrong setting or uses the wrong value, then it could cause more problems than it solves. Only try these if you've a full system backup to hand.
If you're happy to continue, then, Complete Internet Repair is a great place to start. It can fix many networking issues in a click or two, as well as repairing IE and (for some reason) the Windows Event Viewer.
SMART is a handy tool for resetting your Windows services to their default states, perfect if some have been accidentally disabled and you're not sure which. (Although you may also break some of your existing applications, so be careful.)
The Crisis Aversion Tool can reenable Task Manager, reset Windows Update, fix Windows Installer and solve many other problems in just a few clicks.
And the Windows Repair Tool, perhaps the best of all, can solve Registry and file system problems, repair icons, proxy settings and much more. It's a great utility, but as with all of these programs, is risky if you choose to apply a fix which isn't relevant for you. Make sure you create regular system restore points, so you can recover your original settings if you have any problems.
EASY CLEAN: If you prefer the easy life Windows Repair is ideal - it fixes a host of Windows problems in a click

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.