How to free up RAM
Master your memory and speed up your PC
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
There are many reasons why your PC might slow down, but few have quite such a dramatic effect as running short on available RAM.
If this happens to you then you'll notice the hard drive begin to thrash, as Windows writes blocks of memory to your paging file.
Before long your system's performance could slow to a crawl. And if you're really short on memory then some apps may not be able to cope, crashing or displaying odd error messages, and your system will become virtually unusable.
It pays to keep an occasional eye on how your RAM is being used, then, to identify ways in which it's being wasted, and free up the memory for more important things. It's a surprisingly straightforward process, and just a few minutes of exploration can make a real difference to your PCs performance.
Remove RAM-hungry applications
The best way to begin to free up RAM is to understand how your system is using it right now, and the best tool for doing that is Process Hacker.
This powerful free tool comes in a compact 1.4MB ZIP file, runs on all versions of Windows from XP SP2 upwards, and doesn't even require installation: just unzip it, browse to the appropriate folder (x86 for 32-bit Windows, x64 for 64-bit), launch ProcessHacker.exe and you're ready to go.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
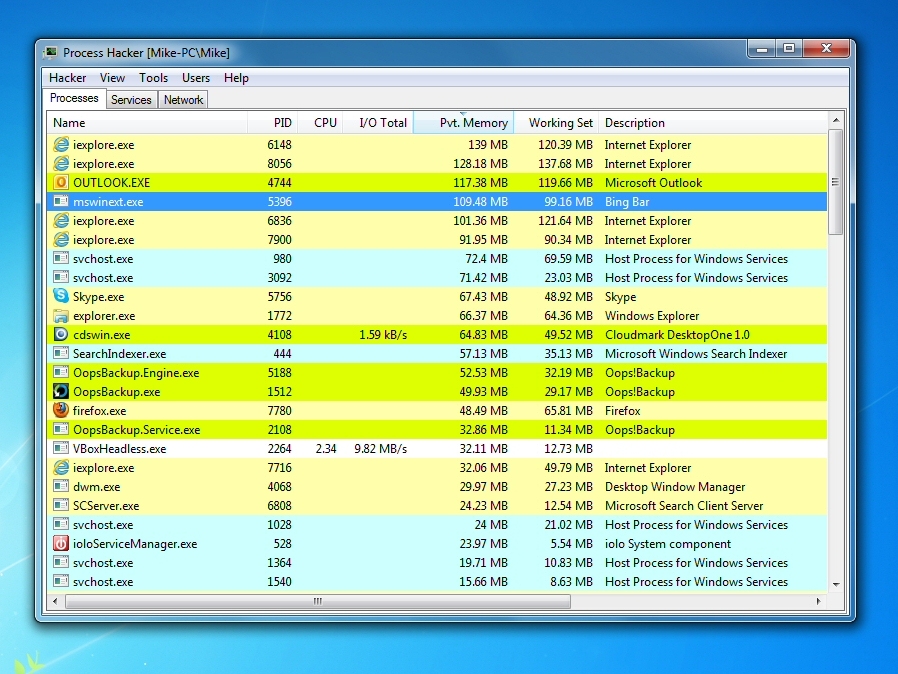
The Process Hacker "Processes" tab will immediately tell you more about the processes running on your PC. We'll need to make sure it's displaying the right information, though.
Right-click on the Name column, and make sure the Active Columns list includes Name, Pvt. Memory and Description at a minimum (having other values as well isn't a problem). If you don't see one or more of these, find and select them in the Inactive Columns list, and click OK to add them to the display.
We added "Pvt. Memory" (Private Memory) here because it tells us the RAM that each process alone is using, memory that isn't in use by anything else - it's probably the best single indicator of how RAM hungry an app might be. And to see what that means, click the "Pvt. Memory" column header twice to sort your list of running processes by memory use, with the highest value at the top.
Now it's just a simple matter of scanning down the list and looking for programs that you don't really need. Such as? We tried this on a demo PC, to find out.
EATING RAM: Do you really need all those system tray programs, running in the background?
Top of our RAM-use list were Internet Explorer and Outlook. They both have to stay, but if we wanted to run a memory-hungry program, like a game, it's a good reminder that we'd benefit from closing those first.
Third from the top, consuming more than 90MB was "MSWinext.exe", which the Description column told us was the Bing Bar, bundled with Windows Live Essentials. Browser toolbars can be real memory hogs; if you have any that you can do without then uninstall them for a quick RAM boost.
Our test PC also had a SVCHost.exe process, consuming 72MB. You'll see many SVCHosts, as they're used to support Windows Services, but double-clicking this one and selecting the Services tab told us what was grabbing our RAM here: Windows Defender.
If you have a full antivirus/antispyware package already and you don't use Windows Defender as a backup, then there's no point having it running in the background. Launch the program, click Tools > Options > Administrator, clear the "Use this program" and click Save. When you need reboot Defender won't be relaunched, and you'll have freed up more RAM.

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.