Android security apps: do you need them?
Do the many Android virus claims pose a real threat to your phone?
Malware, malware, viruses, attacks, phone numbers being stolen, lives put at risk, solar flares wiping out the communications grids and so on. All of those scenarios have been blamed on Android recently, as antivirus companies pitch Google's mobile OS as the next worst thing that'll ruin your life.
But is Android malware an actual real thing? Or is it largely a myth, proven only in exploits performed under laboratory conditions?
Chet Wisniewski, from anti-virus firm Sophos, told us: "It is not terribly widespread outside of China, but the number of malicious apps is increasing dramatically."
"In 2010 we saw around 40 threats, in 2011 more than 400. Evidence for 2012 suggests that number will continue to increase. To date the majority of threats are on unofficial/pirate markets, but we have seen several apps make it onto the Google Play store, only to later be discovered and deleted."
Why is Android vulnerable?
"The ability for users to load software 'off market' opens the door for malicious applications to be distributed without the need for a vulnerability," says Wisniewski, meaning anyone can write an app and anyone can install anything on their Android phone, granting it permission to go wild with their personal data.
Google's main defence is the Android Permissions notifier, which tells you exactly which phone features an app will be able to access once installed. The problem is, no one reads these permissions. It's a boring list of things most of us don't understand. How is the everyday man expected to know if it's right or wrong for a particular app to require access to his contacts details?
There's also the problem of software updates, which has been the bane of Android over the last year or two, as Google relentlessly releases new OS versions and the networks struggle to keep up.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
"The other factor that increases the risk for Android users is the lack of patches that fix the vulnerabilities that are discovered," says Wisniewski. "Even if Google fixes the flaws in the core version of Android, most carriers and phone makers lag far behind integrating the fixes, if they bother at all."
Which all sounds very worrying, but then again it's common practise and advice throughout the tech world - always update to the latest version of any software. If you've been stranded with an unsupported Android model that's sitting on version 1.6 of the software, you may well be more vulnerable. The hackers have had longer to work on exploits.
Do you need an Android security app?
Wisniewski thinks so, explaining: "Not all security applications are the same, some are more of a marketing effort than a true security application. As the number of attacks increase it is likely we will need to provide protection on the device as well as more carefully screening applications submitted to the marketplaces."
At the other end of the spectrum, a famous rant published on Google+ by Google man Chris DiBona, who's the Open Source Programs Manager at Google, said: "Virus companies are playing on your fears to try to sell you bs protection software for Android, RIM and IOS. They are charlatans and scammers."

Most Android malware scare stories are based around one of two extreme premises - theoretical breaches discovered by researchers in their offices but not actually spotted in the real world, or apps that spawn numerous pop-up adverts designed to pull in ad revenue for the few days they're allowed to run riot on Google's Play Store.
The latter is by far the most common. In the run up to the Android launch of iPhone smash Temple Run, numerous clones popped up on the Play Store. Some were rather malicious, redirecting users' browsers to ad-covered web sites and inserting bookmarks, but they didn't have the power to break your phone beyond repair – nor were they technically malware, as they were only doing what users had granted them permission to do so.
No security or anti-virus app will stop something you're specifically handing permission to, so they are, in cases like this, entirely useless.
So while there's certainly a lot of boundary-pushing, invasive software that can legitimately take its place on Google's Play Store, actual reports of phone-breaking data-thievery are extremely rare to come across.
Is my phone infected?
Sophos' most recent Android malware report concerned a game called 'The Roar of the Pharoah' which, it claimed, contained a trojan that could gather your phone number and IMEI code, with the ability to send SMS messages to premium rate services.
Only problem is, this app wasn't found on the Google Play Store. Sophos found it on unnamed "unofficial download sites," so it's entirely possible that no users whatsoever were infected by this apparent threat that gained a lot of internet column inches over the past month.
Another common Android malware fighter and evangelist is McAfee. Its 2011 threat update [PDF] made for worrying reading, claiming that two new viruses - Android/NickiSpy.A and Android/GoldenEagle.A - were found on Android phones in the last quarter of 2011.
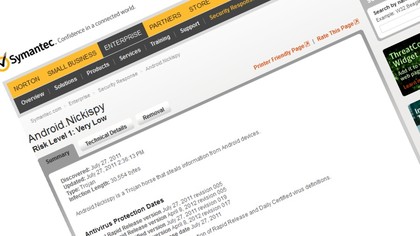
Symantec supplies some data on the number of infections, which show that the Android.Nickispy trojan, which is claimed to have the ability to record users' phone calls, has infected between 0-49 devices. Which is statistically about zero when Google's selling 700,000 Android gadgets every day.
Will it get worse?
Anti-virus firms say yes it will, while Google has recently introduced an app-scanning tool it calls Bouncer, designed to detect common forms of malicious code uploaded to its Android Market and delete them before they can inflict pain on users.
With over 200 million Android devices out there today, and a rather patchwork approach to updating their software, it's inevitable that some older models will be exploited and found more
The rule of thumb is to keep it official, only downloading apps through Google's Play Store, as at least that way you have some form of safety net and the backing of Android's own army of app-checking reporters. And check those permissions when installing an app, as boring a task as it may be. They're your first indication that something's trying to work its way a little too deeply into your phone.
And while anti-virus apps from the big name PC software protection companies are on the rise on Google's Play Store, they won't stop the adware spam apps and fakes, as they rely on you granting them permission to run.
As with most things in life, the sad fact is you're going to have to start paying more attention to the small print if you want to stay exploit free.
- We've also highlighted the best antivirus