
Data breaches, both internal and external, are on the rise, with no sign of stopping. Of thousands of companies surveyed, half have experienced breaches, mostly over the last three years, and nine of ten breaches occur not due to internal malfeasance or breaches to data protection companies, but rather due to employee errors giving bad actors inside access.
So rather than focus efforts on securing your network from external assaults, companies need to protect themselves from their own inattentive employees. While educating and training employees about potential threats is a good first step, it can only go so far. You need a more comprehensive solution. Unfortunately, the most effective solutions such as employee monitoring software might be seen by employees as breaching their privacy rights. These software track employees’ potentially suspicious or misguided activity; notify security teams instantly if a suspected breach has occurred; and give those teams the ability to instantly take over any workstation and cut off any potential data loss. Plus, the best software solutions analyze user behavior and predict insider threats. The software can even automatically act to block any dangerous activity that might lead to a data breach. In most cases you can step in and de-escalate problems before they become an actual security threat.
For most employee monitoring software companies, this is a blanket solution, with every employee treated as an equally potential threat and little regard is given to preserving privacy. But the industry-leading security service Teramind encourages its customers to eschew this us-versus-them mentality and transparently protect your employees from their worst impulses while also protecting their privacy from their own mistakes.
Save time and money by getting a tailored quote
We work with industry-leading providers to match your requirements with their products. Just tell us what you need from your employee monitoring software, and our most suitable partners will contact you to see if you want to take things forward.
1. Enter your details below. Simply tell us a bit about what you want from your software, and leave some contact details.
2. We search our database. We’ll match your requirements with the services and prices that our partners offer.
3. Partners will contact you. Only the suppliers who match your requirements will reach out to you.
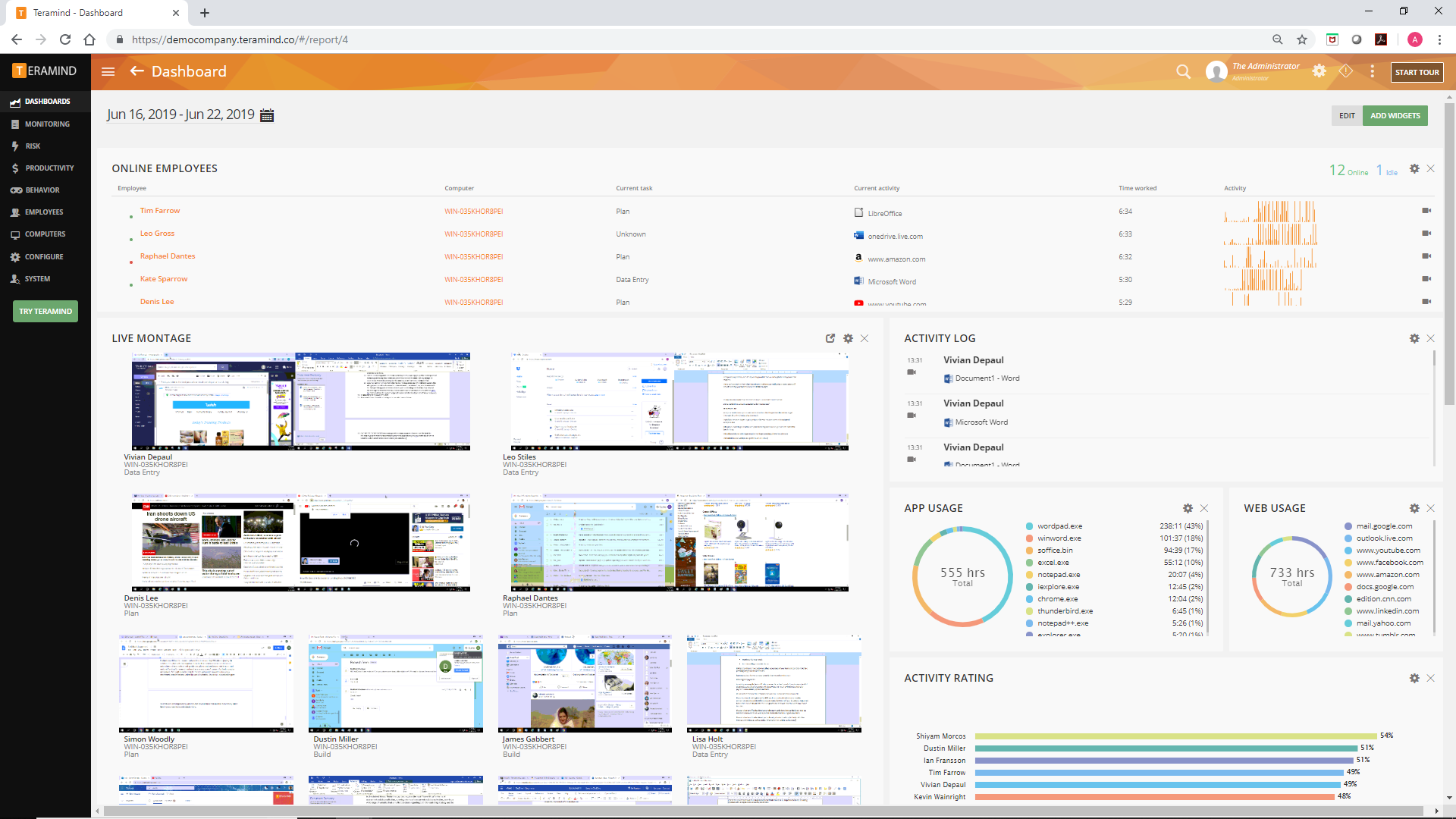
Teramind is an ISO2001:2013-certified company that aims to align its products with regulatory standards like CCPA, GDPR and HIPAA. And it has received acclaim from several tech sites for the effectiveness of its services, including TechRadar.
To protect your company while preserving user privacy, Teramind lets you choose and prioritize what you need to monitor. While you can track virtually all user activity from emails, keystrokes or individual file to any onscreen content, you can turn a particular monitoring feature off or modify its settings to track only specific actions and behaviors.
You can also choose between installing a “Hidden Agent” or a “Revealed Agent” into each monitored device. In the latter case, the user can decide when they should be monitored and for which tasks. This is especially useful for third-party, offsite contractors and freelancers who you’d like to track remotely during work hours, but not during their personal time: they can simply turn off the tracker whenever they’re not working.
To see how exactly you’ll be able to monitor employee action while minimizing the exposure of their private information, you can try out their interactive simulator, or sign up for a free trial.
A personalized protection plan
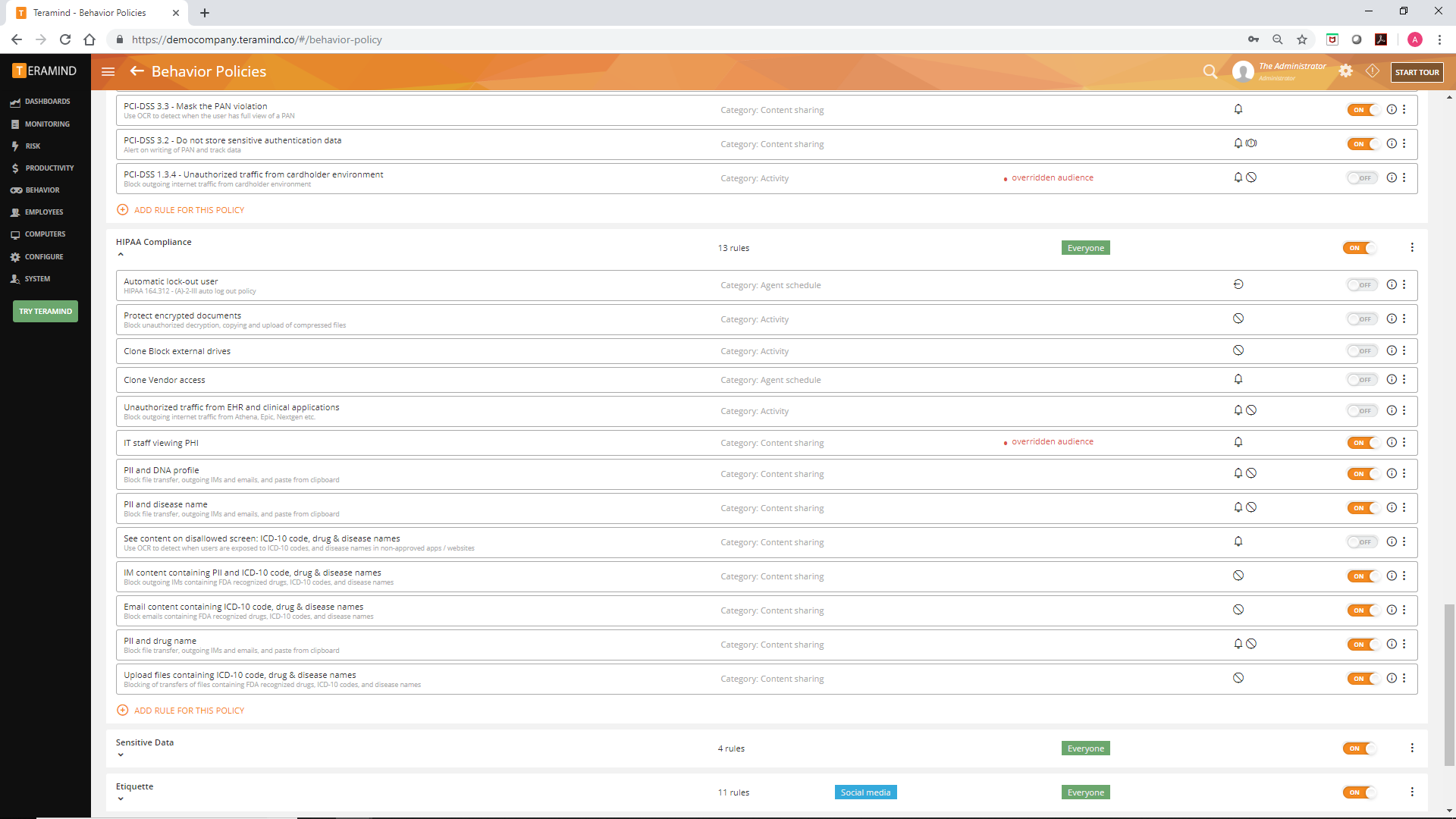
The solution comes with three pricing tiers and available as Cloud, On-Premise or Private Cloud deployment (such as AWS, Azure) making it suitable for SMEs to large enterprise customers.
Each of the three pricing levels offers at least some AI-based protection from data loss and monitoring of off-task employee behavior.
The first package, Teramind Starter, monitors by default, all websites and applications visited, tracks the time spent, and summarizes the data in easy-to-read form for each employee not exempted by you. It tracks and logs messages sent on popular IM apps like Skype or Facebook Messenger, keeps a history of web searches, and notes any social media posts sent at work.
This already represents a lot of private data, and Teramind recognizes that you may not have the time or inclination to individually read these reports. Instead, the system tracks and collates all of this data for you and generates a summary giving you a snapshot of all the key alerts, user activity level, overall app/web use and such. You can drill down to each of these reports complete with screen snapshots or video recordings of any activity or time.
Another major way Teramind helps you save time and reduce privacy concerns is through its smart rules feature. This way you can set up automated rules that flag employee activity that might violate your company policy or security. For example, when an employee uses hostile language on posts, spends more than a set amount of daily time on a site like Facebook, or opens a dangerous email attachment. This way, you can focus on employee behaviors that are of concern to you while minimizing intrusion to their private affairs.
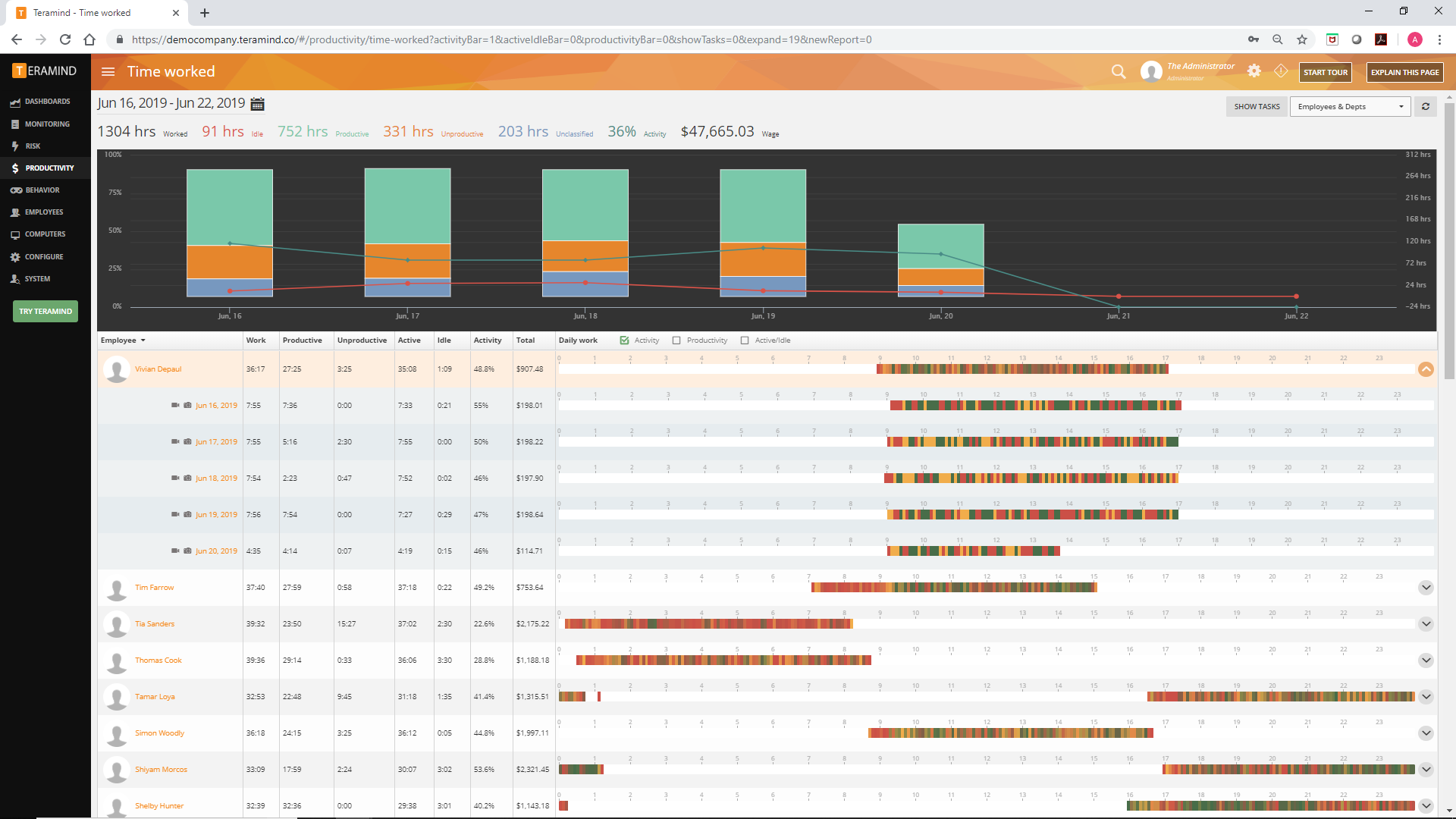
Even when an employee misbehaves, you don’t necessarily need to have your security team step in themselves. The system can take automated actions for you. For example, you can set up automated alerts notifying an employee if they’ve spent too long on a non-work site, and then deny access to that site for the rest of the day. This makes the employee actively aware of the monitoring and ensures they know they’re being held accountable for their actions, rather than falling into repeatedly bad habits without realizing the harm.
Finally, in the event of a serious problem, you can remote access any computer and then block any malicious activity. But in order to detect said activity, Teramind offers a much more comprehensive toolset with the Teramind UAM package.
With Teramind UAM, you have a wider monitoring scope than the Starter pack. For example, the Keylogger tracks every keystroke; the Email Monitoring tool tracks both desktop mail clients and webmails; the File Transfer tracker monitors file movements over local, intranet or cloud drives; Printer Monitoring detects print jobs containing sensitive documents; and more. With the Network monitor, if the software detects unusual network activity of any kind, it will step in and deny access to whatever the source of the intrusion is, such as accidentally downloaded malware or remote access by an unknown device. Its most sophisticated tool is its OCR (optical character recognition) program, which can scan for text on the screen, even inside images or videos. This allows you to build powerful rules to take automated action when certain text or pattern is detected on the employee’s screen. For example, setting up an alert when a user sees a full credit card number on screen violating the PCI DSS compliance.
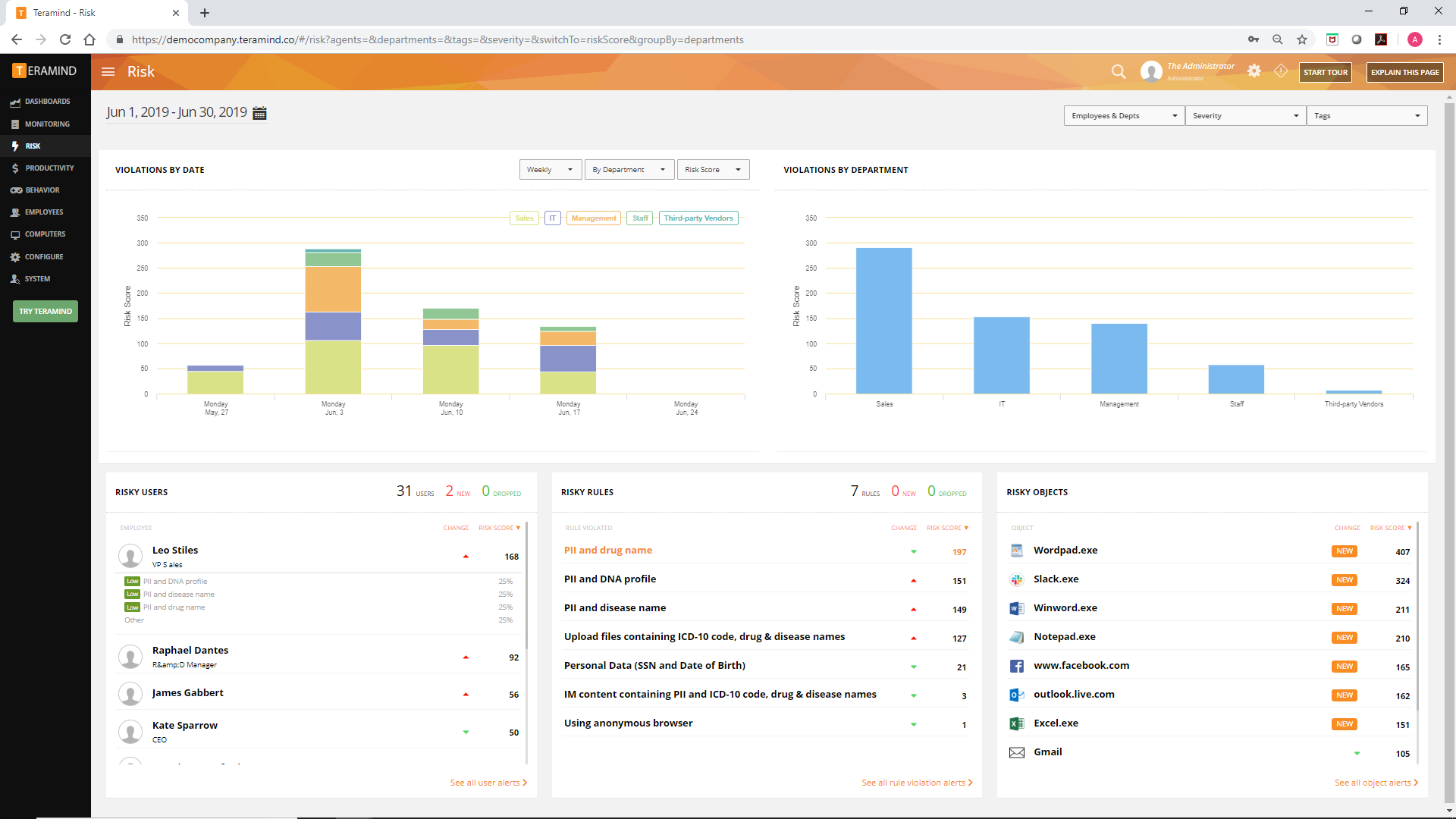
Ultimately, you will have the power to set rules on what behaviors are inappropriate for your company’s situation. For example, you can restrict sending work emails from personal accounts to prevent important data being kept in less secure accounts, or get notified if your employee is uploading company files to their personal cloud drives on Dropbox or Google Drive.
Even in the midst of this comprehensive data access, you can configure it to to protect your employees’ privacy. For one example, you can set it up so that when the OCR detects a credit card number on the screen it will automatically black out that footage so that admin users can’t steal someone’s private information. Plus, the system allows you to set up strict access control policies, so that admins can’t abuse their privileges to (for another example) view an employee’s private information or export such data to an off-network site. After all, security or IT can have bad actors too.
Finally, Teramind offers its premier data loss prevention solution Teramind DLP. It takes all of the features from Teramind Starter and Teramind UAM, and bundles them with additional content based rules and better support for compliance standards such as PCI DSS, HIPAA, GDPR etc. Altogether, it’s the most powerful version of all the Teramind offerings.
Using content-based rules for employees’ file transfers, emails and clipboard, the DLP system notes any potentially sensitive information—aided by any definitions you add of what in particular is sensitive—and prevents any possible method of smuggling that information outside. Something like customer credit card info, for instance, will be instantly detected anywhere outside of where it should be.
But Teramind DLP doesn’t stop there: it comes with many data classifications for protected information, including PII (personally identifiable information such as names, phone numbers and addresses), PHI (protected health information such as drug names or DNA profiles) and PFI (personal financial information like credit card numbers and bank codes). Teramind’s solution allows you to quickly create rules to detect and protect those sensitive data in transferred or printed files, emails or even a real-time chat conversation. Or if these default classifications don’t fit your specific industry needs, create your own classifications easily with powerful Natural Language Processing (NLP), Regular Expressions, Keywords or upload your own whitelist / blacklists from a CSV or Excel file.
Putting a price on security
Even with the Teramind Starter package, you take an important first step towards securing your company from data theft stemming from employee actions (intentional or otherwise).
Ironically, the more powerful the package and the more information the system collects, you not only further protect your company from harm; you also make it easier to avoid skimming through your employee’s private lives, relying on the objective nature of the machine learning algorithms to catch moments of real harm and trusting that evidence of slacking or unhappiness can hopefully be resolved with a simple conversation.
Ultimately, we recommend that you try out the various packages for yourself, and see what best fits your needs. Go to the Teramind website and try a free trial period with the software, or schedule an appointment to try the Teramind interactive simulator, for a first-hand look at what top-of-the-line security looks like.
Sign up for breaking news, reviews, opinion, top tech deals, and more.