You don't have to be overly careless to lose your laptop - it can happen to the best of us - but that doesn't mean you should just accept the fact that you your beloved machine is gone forever.
With the open source package Prey, you can pull a fast one on the thief. You can keep an eye on the perp's whereabouts and see how he or she is using your device - information that will come in handy when you're reporting the theft to the authorities.
Prey works on several operating systems, including recent releases of Windows, Mac OS X, and even Linux distributions. It also works on Android devices, and the developers are working on an iPhone version. Best of all, it's free for tracking up to three devices.
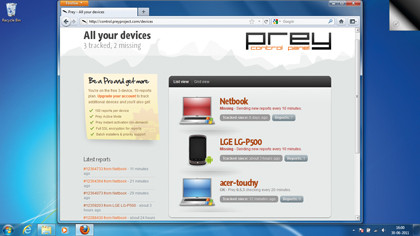
You control Prey via a web console, which covers all your devices. When one of them goes missing, you can mark it as such in the control panel from any computer, after which Prey will keep an eye out for it. As soon as it sees that the device is online, Prey will send you lots of information about the device, and more importantly, its location.
Set up a device
Prey can only track devices if you install it before they go missing. This isn't a retroactive tool, sadly - you have to be organised. However, installing Prey is a walk in the park as long as you have administrative privileges under the OS you're installing it on.
It's a good idea to lock your Prey administrator account with a strong password, which will prevent the program from being removed from the system if a thief realises what it is. Prey runs in the background without the thief's knowledge, so lure them with a Windows user account with no admin privileges and no password. As soon as they log in, they're all yours!
Once it's installed, Prey asks you to set up a reporting method. The reporting method controls how the tracking software communicates with the devices and reports back to you. The recommended method is to use Prey's web-based control panel, which can be used from any machine. Before the control panel was developed, Prey could only run in standalone mode and required you to set up your own mail server - an awkward process.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Once that's taken care of, you'll need to set up a user account. The Prey setup process asks you for your name, email address and a password. It also picks up the name of the device and its type from the OS, which you can edit either in this screen, or later from Prey's control panel.
For subsequent installations on other devices, select the option to link the device with your existing account. That's all there is to it - you're now ready to set up Prey's behaviour.
Start by launching the Prey configuration tool, and selecting the 'Manage Prey Settings' option. This lets you enable a password-free guest user account under Windows to lure whoever has stolen your device into using it. You should also activate the 'Wi-Fi auto-connection' option, which discreetly connects to the nearest open Wi-Fi hotspot and starts sending you reports.
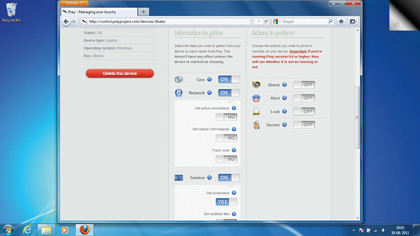
After you've set up your device, you can configure its behaviour via Prey's web-based control panel. The control panel is broken into various sections that control different aspects of the device.
Lay your trap
First, head to the 'Configuration' section, from which you can alter the name of the device, as well as its operating system. The default values in this section vary from machine to machine, and are the ones automatically detected by Prey.
Besides the configuration options, there's the Hardware section, which gives you detailed information about the hardware on a particular device, including its serial number and that of its motherboard. If you have a feeling the thief has scavenged your machine for its hardware, you can perform a manual hardware scan via the configuration settings.
You can also ask Prey to notify you with an email when it detects any changes to the hardware of the device. This is especially useful for desktop computers in a public place such as a cyber cafe or a public library. The chances of somebody making off with a desktop tower without anybody noticing are remote, but stealing a memory chip from a public desktop computer doesn't take very much effort.
The various options under the 'Main' configuration section are separated into two groups. 'Actions to perform' lists actions Prey will take on your device. Although these actions will be performed irrespective of whether the device is marked as missing, it's best to keep them turned off until the device is actually lost.
There are a couple of options to dissuade the thief. The first is the alarm option, which sounds a loud noise from your missing device to help you find it if it's nearby. Then there's the Alert Message option, which changes the wallpaper of the device and displays a warning that tells the thief the device is being tracked by Prey.
Lock your phone
If these don't work to discourage the thief, you can use the Lock option to prevent the computer from being used until a password is entered. The best thing about this option is that you can activate it, set a password and lock the device with the password remotely after it has been stolen.
Alternatively, instead of locking the computer, you can set Prey to discreetly gather information about the miscreant. As soon as the device is brought online, Prey can use nearby Wi-Fi access points to interpolate the location on your device and mark it on Google maps. Along with this, it gathers other network-related information such as the public and private IP address of the network the device is connected to.
You can also ask Prey to run a trace-route (to www.google.com) from the missing machine through the thief's router. If you're interested, you can ask Prey to gather lots of information about the desktop session - a list of running apps, which files have been modified in a particular directory, along with a screenshot. Over time, you can build quite a repository of the sites that the swindler frequents, the apps they like to run regularly, and the files they have created on your machine.
Sooner or later you will also get a screenshot of them logging into their webmail account or some other website. While you won't get their password, you'll be able to clearly see their username, which you can use to contact them.
If your device has a built-in webcam (most laptops and netbooks do these days), Prey will also secretly take snapshots of whatever the webcam sees. It won't take long before you catch the crook in front of your stolen device.
On some machines though, such as out Lenovo netbook, there's a small LED that lights up when the camera is on. If the crook sees this, they might cover the webcam.
You can set the interval after which Prey wakes up and collects the information you've asked for. In the free version, this can be between 10 minutes to 40 minutes. The Pro version enables you to create a persistent connection with the device.
Although you should still take every precaution to ensure you don't lose your device, in case you do, you are now fully prepared to take on the perp who's got it, and either force them to return your device or build a strong case for the authorities to act upon.