Computing Security
Explore Computing Security
Latest about Computing Security
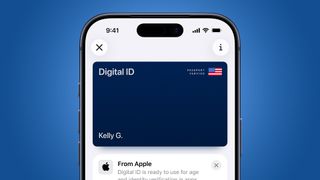
Apple's Digital ID sparks privacy concerns
By Chiara Castro published
Apple launches a new Digital ID tool, but the feature doesn't convince privacy purists.

I spoke to Amazon, Google, and Roku about Fire Stick's latest piracy crackdown measures – here's what they said
By Rob Dunne last updated
Is Amazon really about to quash pirated content for good, or is it just a temporary fix?

In the wake of the Louvre heist, Proton steps in to offer free password protection
By Rene Millman published
Cultural institutions can get two years of Proton's premium password manager for free

These are the vital components of a good cybersecurity solution
By Sead Fadilpašić published
Sponsored by ThreatLocker
There is no universal checklist of exactly X features that a cybersecurity solution must have, but these should be prioritized.

Here are the 5 essential features an EDR should have
By Sead Fadilpašić published
Sponsored by ThreatLocker
Despite some vendors using slightly different terminology or emphasizing certain aspects, the core functionalities are consistent across the board.

EDR vs MDR vs XDR: What is the difference?
By Sead Fadilpašić published
Sponsored by ThreatLocker
Some companies tend to coin their own acronyms to describe their unique products and services.

Stay safe online with 30% off at ESET with our exclusive code
By Paul Hatton published
Save up to 30% on ESET Home Security Essential, Premium, and Ultimate with our exclusive code
Sign up for breaking news, reviews, opinion, top tech deals, and more.


