Sponsored by ThreatLocker
EDR vs MDR vs XDR: What is the difference?
These days, it’s often not clear which security tool does what

These days, it’s often not clear which security tool does what, since there is quite a bit of overlap in their functionalities.
The fact that some companies tend to coin their own acronyms to describe their unique products and services, even if they are variations of existing concepts, certainly doesn’t help.
Detection and response tools are no different, despite being a key part of any cybersecurity strategy, thanks to their ability to catch threats that somehow managed to find their way around defense lines.
With that in mind, how about some clarification on EDR, MDR, and XDR, so you can make better decisions and fill potential gaps in your organization’s security?
Try ThreatLocker for free for 30 days
ThreatLocker is a cybersecurity platform designed to give businesses complete control over what runs on their networks. It uses zero-trust application control, ringfencing, and storage control to block unauthorized software and prevent ransomware attacks. Businesses can easily deploy it to protect critical data, enforce policies, and monitor activity.
What is EDR?
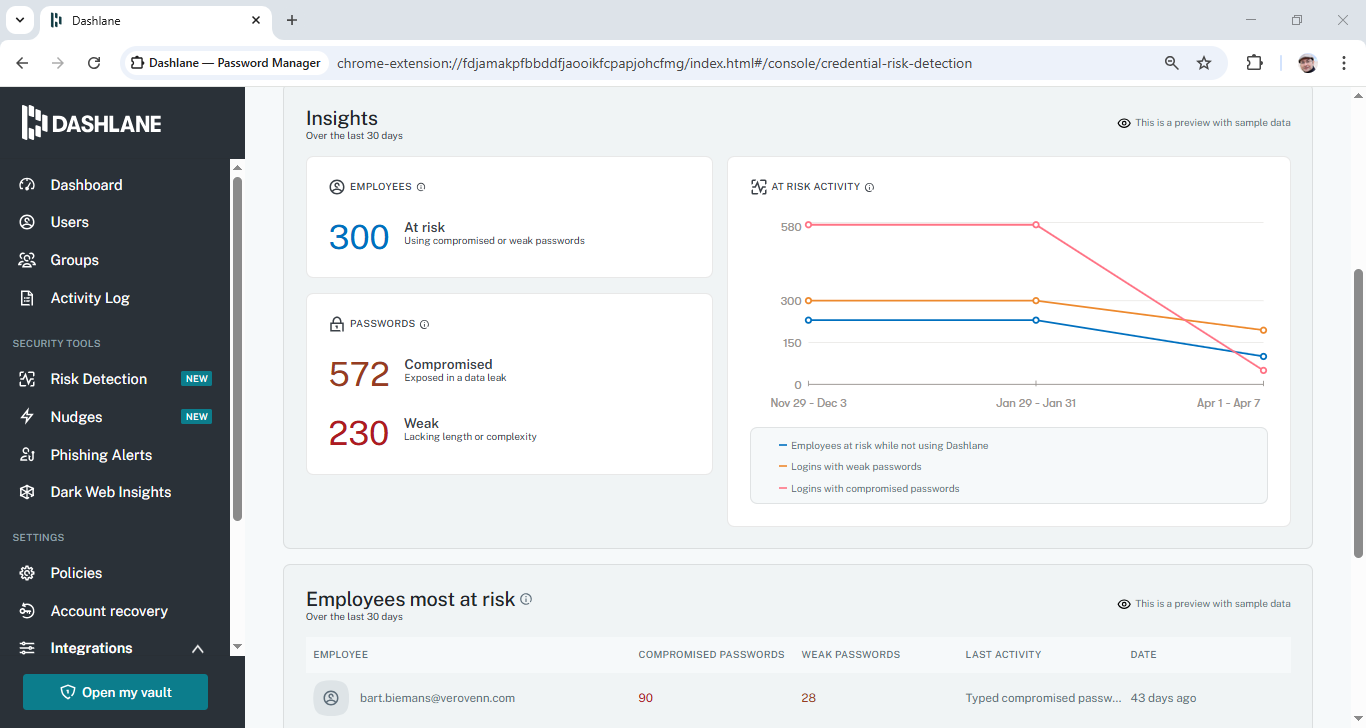
Short for endpoint detection and response, EDR is a cybersecurity technology that continuously monitors and collects data from endpoints, like laptops, desktops, servers, and mobile devices, to detect, investigate, and respond to cyber threats.
An EDR platform acts as a foundational security layer, as it goes well beyond traditional antivirus software by providing a deeper level of visibility and a more proactive approach.
It combines real-time monitoring, data collection, and advanced correlation to address suspicious activity at endpoints, which enables security teams to quickly identify the danger and react.
Typically, software agents on endpoints capture a wide array of data, from process executions to user activities.
By employing behavioral analysis, machine learning, and threat intelligence, an EDR tool can identify suspicious patterns and kill a malicious process, quarantine files, or isolate infected devices. You also have the option to perform deep investigations and manually remediate.
Types of threats EDR works best against
EDR is specifically designed to combat advanced and sophisticated threats that can bypass traditional, signature-based security tools. It looks for telltale signs of an attack (e.g., the sequence of events and the behavior patterns) as opposed to just a specific malware signature.
Due to EDR’s focus on anomalous behavior, it can detect fileless malware attacks that execute entirely in memory, as well as zero-day threats and new, polymorphic ransomware.
For instance, if a process is trying to encrypt a large number of files, EDR will automatically shut it down before it can cause widespread damage.
The ability to monitor user and process behavior also allows EDR to stop insider threats, as it can flag suspicious activities from within the network, such as a trusted employee suddenly accessing a large volume of sensitive data or a “regular” user attempting to gain administrator privileges.
What is MDR?
Building on what EDR does, managed detection and response, or MDR, is a turnkey service (rather than a technology) that adds human expertise to the mix.
Through the use of threat intelligence and security analytics, a third-party team of cybersecurity experts proactively hunts for perils within your environment, not just reacting to alerts.
In this case, an MDR team continuously monitors your environment for signs that a threat may have evaded automated defenses.
When an alert is triggered, even a low-severity one, they investigate it to determine if it's the real deal or a false positive, saving your internal team time and resources.
The service also includes containment and neutralization, making MDR an affordable solution for an organization that wants highly skilled professionals looking after its assets.
Types of threats MDR is effective against
It's fair to say that MDR is effective against the same bad stuff as EDR, but with the added caveat that it provides a superior, more certain defense.
Case in point: a brand-new, zero-day attack that doesn’t have a signature or a known pattern. An MDR analyst, drawing on their deep knowledge of adversary behavior, can identify this novel threat through intuition and an understanding of the attacker's intent.
With the advantage of human expertise and continuous service it provides, MDR is highly effective at neutralizing sophisticated attacks.
Through experience in dealing with complex strikes that involve a combination of techniques, such as a phishing email followed by a fileless attack, or lateral movement, where attackers move to other connected devices in an effort to escalate their access.
And because human analysts are involved, they are well-positioned to spot advanced persistent threats, which are subtle and long-term attacks from inside the network that might not trigger an automated alert.
An MDR team can trace the attack's path, identify lateral movement, and find the root cause of the intrusion.
What is XDR?
Extended detection and response (XDR) is a unified security platform that automatically collects and correlates data from multiple security layers, including endpoints, email, network, cloud, and identity systems.
As the name says, it extends the principles of EDR by increasing visibility and response capabilities beyond just endpoint security to cover the full attack chain.
If your company uses an EDR, SIEM, IAM, and other platforms, XDR integrates these data sources at a product level to provide a single, unified interface for investigation.
That way, it eliminates security blind spots by linking seemingly unrelated events across different systems, allowing it to automatically correlate alerts and provide a single, highly contextual incident alert and adequate response, instead of separate ones.
Compared to MDR, XDR is built to break down silos between different security tools and data sources, leveraging technology-driven response actions that are either automated or semi-automated (orchestrated).
Types of threats XDR is effective against
Obviously, XDR's primary strength is its ability to provide a comprehensive, cross-domain view of an attack.
This makes it particularly great for battling threats that leverage multiple attack vectors where infiltrators pivot from one compromised system or segment to another.
One example would be an attack that starts with a phishing email (email security), then leads to a compromised identity (identity and access management), and later uses that access to exfiltrate data from a cloud storage service (cloud security).
XDR also works great when it comes to supply chain attacks, where a third-party vendor or software is compromised.
It can provide visibility into the initial breach point, whether it was through a malicious email, a web server exploit, or an endpoint vulnerability. By linking these events, XDR can pinpoint both the source and the extent of the attack.
Which should you choose?
Ask around, and quite a few cybersecurity experts will tell you that EDR, MDR, and XDR aren’t competing with each other.
Rather, they are parts of the same security chain. It's certainly not a one-size-fits-all choice, so figuring out which is best suited for you depends on your situation and security posture.
As a foundational technology for monitoring and securing individual devices, EDR is a starting point for companies with mature and well-staffed security teams that want granular control.
For organizations that have a small (in some cases, overwhelmed) or nonexistent security team, outsourcing to an MDR provider will be the optimal fit.
Lastly, for enterprises with complex IT infrastructures and hybrid cloud environments, XDR provides the broadest, most correlated view of threats by breaking down data silos between endpoints, network, and cloud.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.
