Proton Mail doesn't guarantee anonymity—unless you do this
Privacy and anonymity aren't interchangeable
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
You might have heard of Proton Mail. An encrypted email service, it's especially popular among activists, journalists, and privacy purists alike who stand by the company's promise to protect their privacy.
This is why the recent news of the Swiss firm disclosing to Spanish authorities the recovery email of a pro-Catalan activist that led to his arrest is likely to have unsettled many Proton Mail users. However, this could have been very easily prevented exactly by the incriminated user.
The suspect willingly decided to add the optional recovery email: an Apple iCloud address. Due to the recovery email not being encrypted—Proton would need to be able to read the address to recover the account—it had to be handed over to the authorities. Subsequently, the Big Tech giant ultimately discolsed identifying information connected to this account to law enforcement.
The main takeaway here is that had the activist not used a recovery email, authorities would have not been able to track down his/her real identity. Proton Mail is a secure email service that promises to offer privacy by default, not anonymity (more on this below).
Realistically, complete anonymity online is almost impossible to achieve—not even if you use the best VPN services out there—but there are still some key things you can do to make yourself more undetectable. Keep reading as I share some simple tips on how to protect your anonymity when using Proton Mail, ensuring you'll avoid a situation like the one above.
Privacy vs anonymity
Let's start with the obvious elephant in the room. Privacy and anonymity are two very different things and they are not interchangeable.
Privacy refers to the level of control you have over your personal information—the freedom from unauthorized intrusion. Anonymity indicates your liberty to conceal your identity to avoid being identified. For instance, while everyone can access a post you share on Reddit, the anonymous nature of the platform makes it impossible to trace it back to your identity.
Most importantly, privacy and anonymity are distinctive concepts by law. Privacy is mostly recognized as a human right. Whilst, anonymity simply isn't. As we have seen, mixing up these two definitions can be costly.
What Proton Mail does
Proton Mail is a private email service that uses different forms of encryption to secure users' communications. Encryption refers to the process of scrambling data into an unreadable form.
As the provider explains in a blog post, emails sent between Proton Mail users or non-Proton Mail users using PGP (short for Pretty Good Privacy) are always end-to-end encrypted. The system uses cryptographic keys to encrypt the data on the sender's device and decrypt it only when it reaches the intended recipients, adding an extra layer of security to the messages in transit. Zero-access encryption is also applied to messages you store on Proton's servers.
All this means that Proton, for instance, is unable to share the contents of emails you send or receive because the company itself cannot access them. This is also true for all your stored messages.
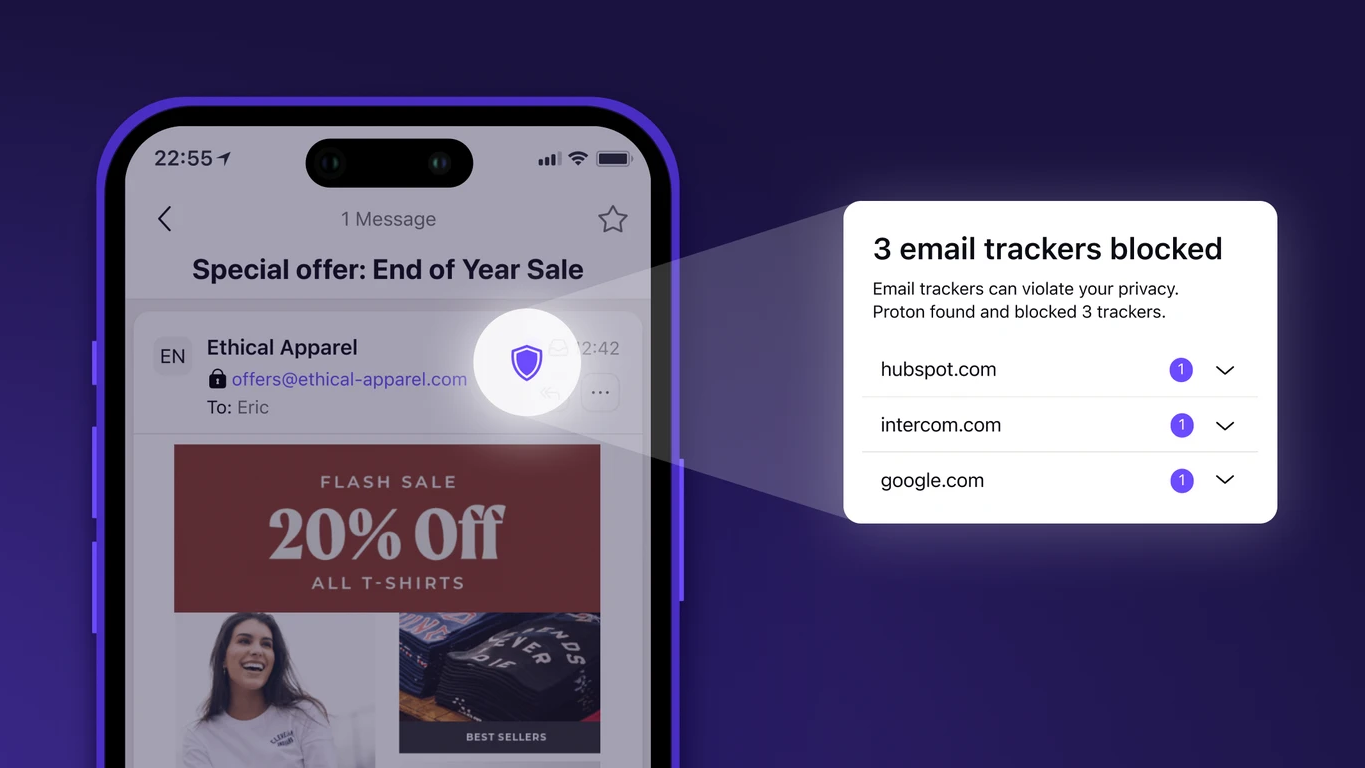
You also have the option to set a timer on some of your chosen emails so that they can automatically self-destruct after the expiration date for maximum security. Other advanced privacy features include unique email aliases and a tracker blocker.
Unlike Big Tech competitors like Google Gmail or Microsoft Outlook, Proton also promises to never track you across the internet nor use your personal information to build a digital profile around your identity.
What Proton Mail doesn't do
While it's important to understand what your privacy software can protect you from, it's vital to be aware of its limitations.
On its side, Proton Mail has a clear and transparent Privacy Policy—which I strongly recommend familiarising yourself with—and does not make outlandish claims on its website. However, the provider still has access to some identifiable information.
This is known as metadata, and these details include recovery email addresses, phone numbers linked to a Proton account, and even IP addresses. Law enforcement can force companies to hand these details over as part of ongoing investigations.
Looking again at the Spanish case, we can see that Proton had just one, albeit valuable, piece of information related to that account: an iCloud email address used as a recovery email.
It's also worth mentioning that the provider releases every year a Transparency report about the number of legal complaints received, contested, and complied with. In 2023 alone, the company received 6,378 legal orders. The team successfully contested 407 of them, but it had to comply with 5,971.
How to use Proton Mail more anonymously
As Proton spokesperson Edward Shone recently pointed out to TechCrunch: "Proton provides privacy by default and not anonymity by default because anonymity requires certain user actions to ensure proper [operational security]."
As a rule of thumb, you should be aware of the metadata that could end up revealing your real identity. The good news is that there are some steps you can take to boost your anonymity when you're using Proton Mail.
This is your regular reminder that metadata matters.In this case, the activist was deanonymized via the backup email for the Protonmail account that he used to set up Wire, which was an iCloud account linked to his real identity. https://t.co/sxGfCaAwIyMay 8, 2024
1. Careful with the information you share
As the Spanish case taught us, you need to be really careful with the information you voluntarily share and link to your Proton account.
First of all, you should never include any recovery email or phone numbers that can directly trace back to your real identity. I advise creating alternative accounts or using burner phone numbers instead, for an extra layer of anonymity.
While Proton Mail, and any other Proton product, is always free to use, you can also upgrade to one of its paid plans. If that's the case for you, I also suggest opting for an anonymous form of payment to further minimize the personal details you'll share with the provider. Proton Mail, for instance, accepts Bitcoin and even cash.
2. Use a no-log VPN
In 2021, Proton Mail had to hand authorities another identifiable detail about a French activist during an investigation: the real IP address. Again, the user could have easily prevented this from happening.
A VPN, short for virtual private network, is security software that boosts your anonymity by encrypting your internet communications and hiding your IP address. The latter is a unique identifier assigned to you by your internet service provider that acts as your home address for the internet.
Using a VPN is a straightforward way to prevent Proton from recording and potentially sharing this sensitive piece of information about your real identity. Proton VPN is one of the best services out there, that also comes with a capable free VPN plan.
In case you want to look elsewhere for the VPN app—some experts suggest turning to another provider might be an even better option for people with a high-threat model looking to minimize the data a sole company might have on them—I recommend getting a strict no-log VPN. That's a guarantee that the provider never records any of your identifiable logs (Proton VPN is one of them). Our top recommendation at the time of writing is NordVPN.

3. Access your account via Tor
Similar to a VPN, the Tor browser is an effective way of evading online surveillance and boosting your anonymity. However, Tor uses a so-called Onion routing system. through which the traffic gets routed through multiple servers (at least three) and encrypted each step of the way.
Using Proton Mail over Tor brings several advantages. As mentioned, it makes it difficult for any third parties to wiretap your internet connection, preventing them from knowing that you're using the app in the first place. Tor's encryption layers also shield you from man-in-the-middle and DDoS (short for distributed denial of service) attacks. As well as making you more anonymous, spoofing your IP also grants you access to Proton Mail even in countries where the service might be blocked.
Proton offers an Onion site that you can use to access all its security products, Proton Mail included. While you can use Proton Mail via Tor also from the regular site, the Onion site is generally more secure.
While I recommend combining Tor and a VPN for extra security, you should bear in mind that these additional encryption layers will slow down your connections.
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
Sign up for breaking news, reviews, opinion, top tech deals, and more.

Chiara is a multimedia journalist committed to covering stories to help promote the rights and denounce the abuses of the digital side of life – wherever cybersecurity, markets, and politics tangle up. She believes an open, uncensored, and private internet is a basic human need and wants to use her knowledge of VPNs to help readers take back control. She writes news, interviews, and analysis on data privacy, online censorship, digital rights, tech policies, and security software, with a special focus on VPNs, for TechRadar and TechRadar Pro. Got a story, tip-off, or something tech-interesting to say? Reach out to chiara.castro@futurenet.com