How to access all your cloud files in one place in Windows 10
Bringing clouds together

How to get started with TopDox
TopDox is a free application for Windows 10 that gives you easy access to files stored in the cloud, whether you’re using DropBox, Google Drive, Box or Microsoft OneDrive.
You can get access to all of your files stored on one cloud service for free, with additional services available via a low monthly subscription. TopDox has an easy-to-use interface that makes it simple to upload, view and share files on whatever service you’re using.
It’s also easy to download files for offline viewing when you don’t have an internet connection.
Cleverly, TopDox enables you to view and export OpenOffice and Microsoft Office documents as PDFs from within the app. You can also use the app to edit Google Docs and Sheets, and view cloud-based videos and photos too.

1. Sign up for TopDox
The first thing you should do once you’ve downloaded the TopDox app is create an account.
This gives you access to your workspace on any of your devices. You’ll then be asked to link one of your cloud accounts for free. If you want to add more services, TopDox gives you the option to pay a monthly fee. Enter your login credentials when requested.
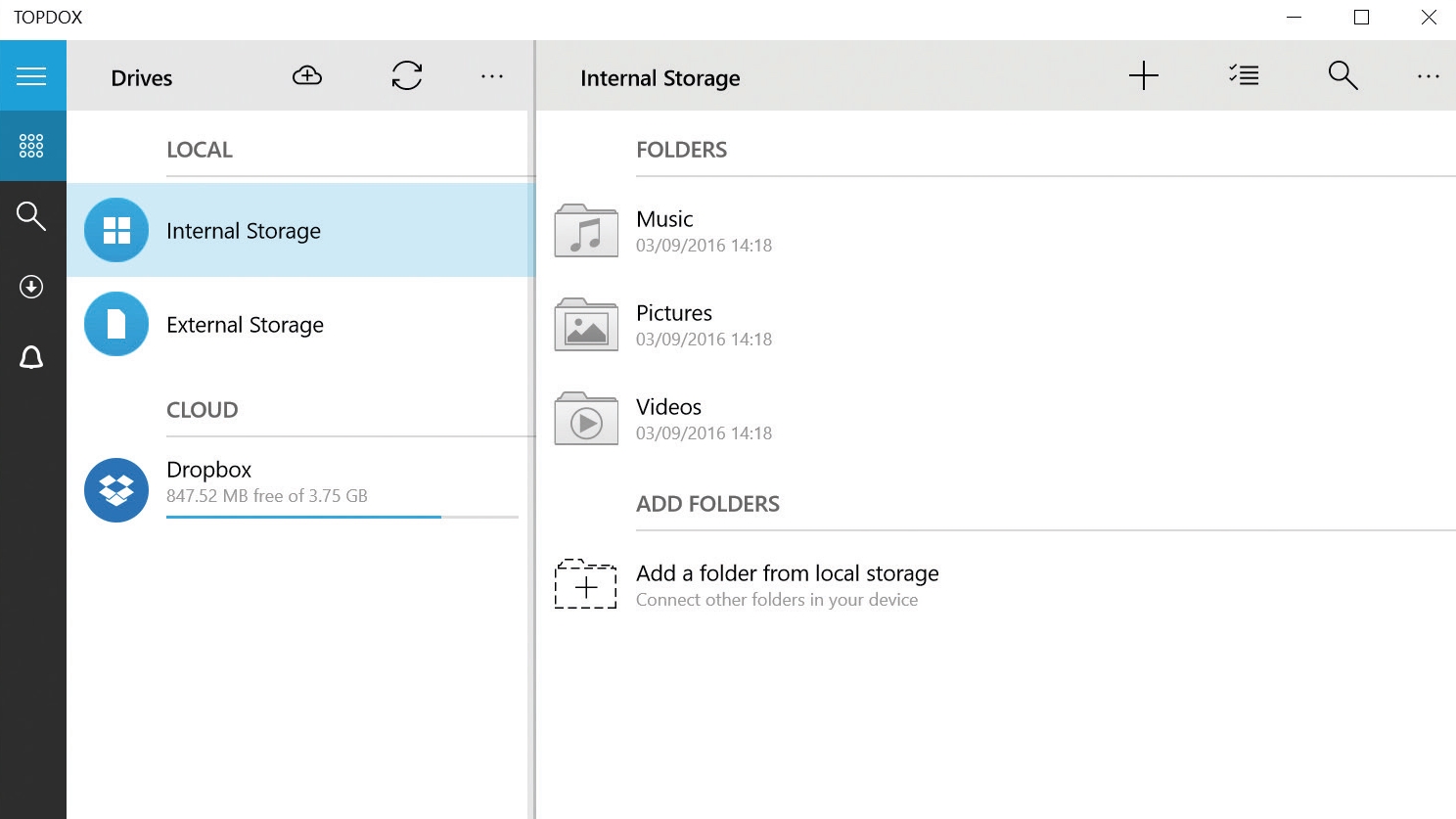
2. Access your files
The TopDox app gives you access to all of the files on your computer (Internal Storage); located on USB and other drives (External Storage); as well on the cloud service you’re using.
You can switch between them using the left menu bar. Each view also gives you the option to transfer files between different drives and the cloud. You can also use it to create new folders at any time.
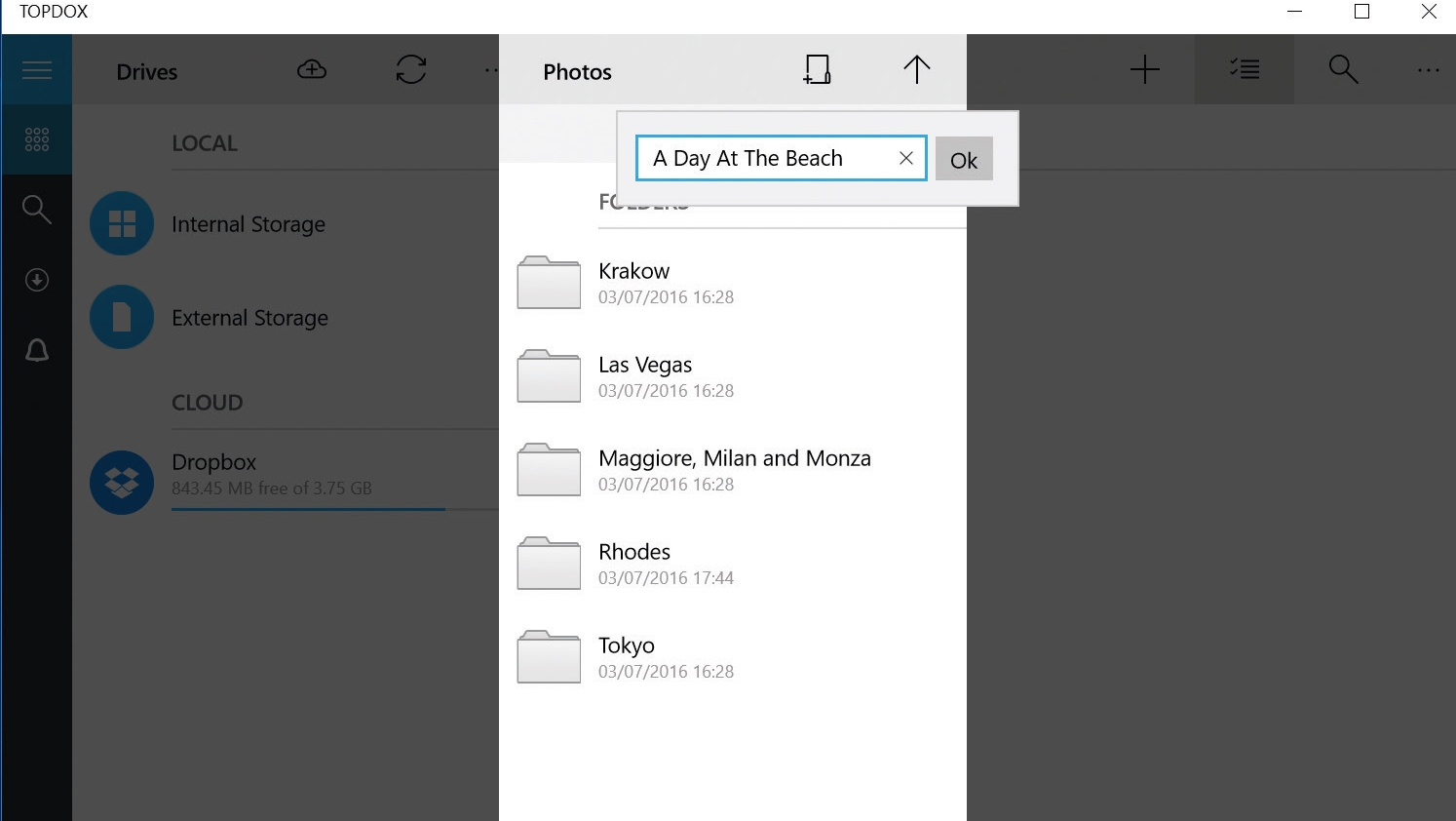
3. Upload your files
To move files from your PC to the cloud, open the relevant folder, then choose the ‘Selection’ tool.
Checkboxes will appear next to the left of each file. Choose the ones you want to upload, then select ‘Copy To’.
You’ll now be taken to a new window, which enables you to choose the files’ destination. To create a new folder select the Folder tool from the menu bar.
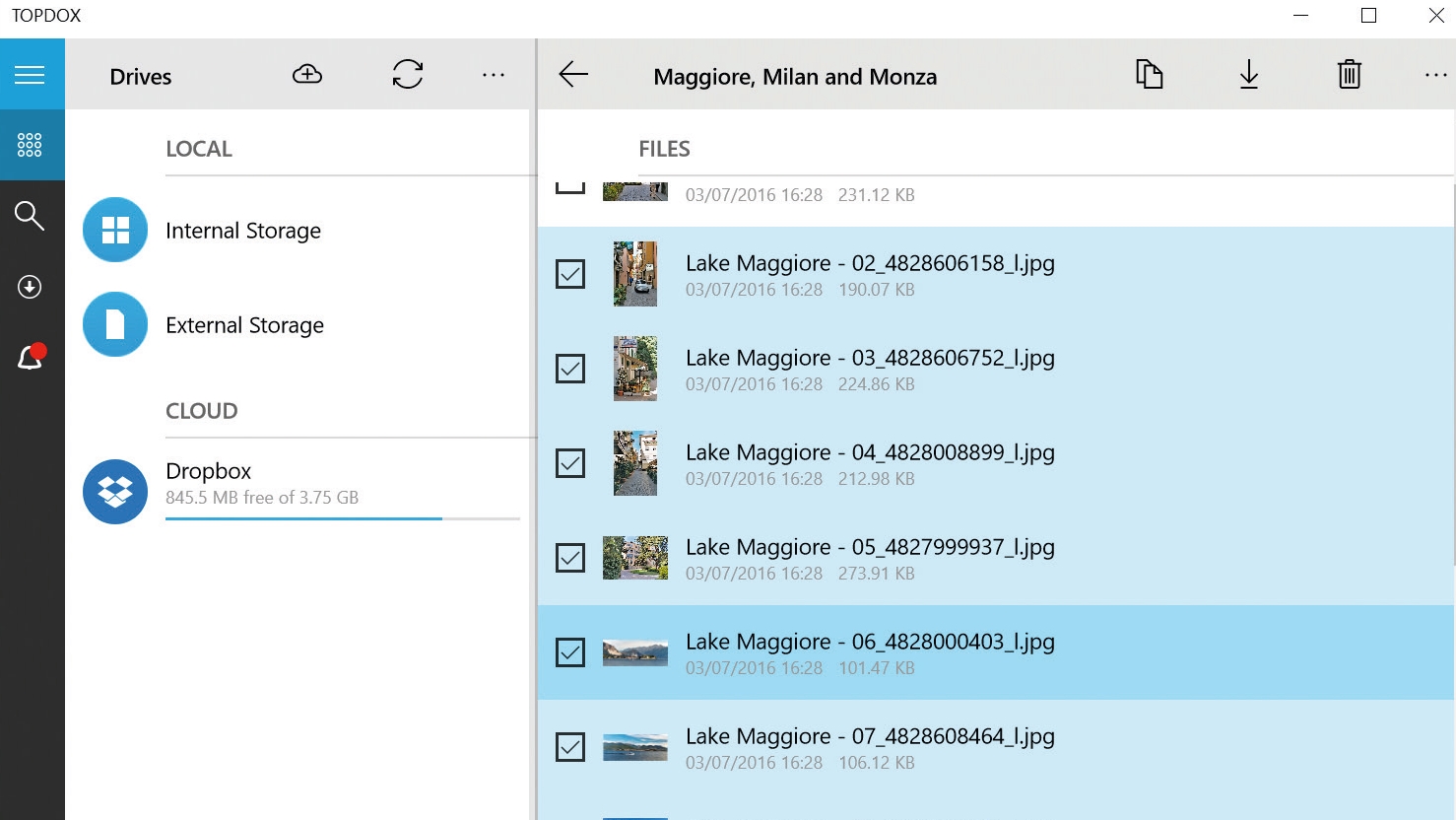
4. Download some files
Fetching files from your cloud service works the same as uploading – except this times it’s in reverse.
TopDox doesn’t give you the option (yet) of copying folders, only the option to transfer the individual files within each one. However, this isn’t too much of a problem if you only want to upload and share individual documents or photos.
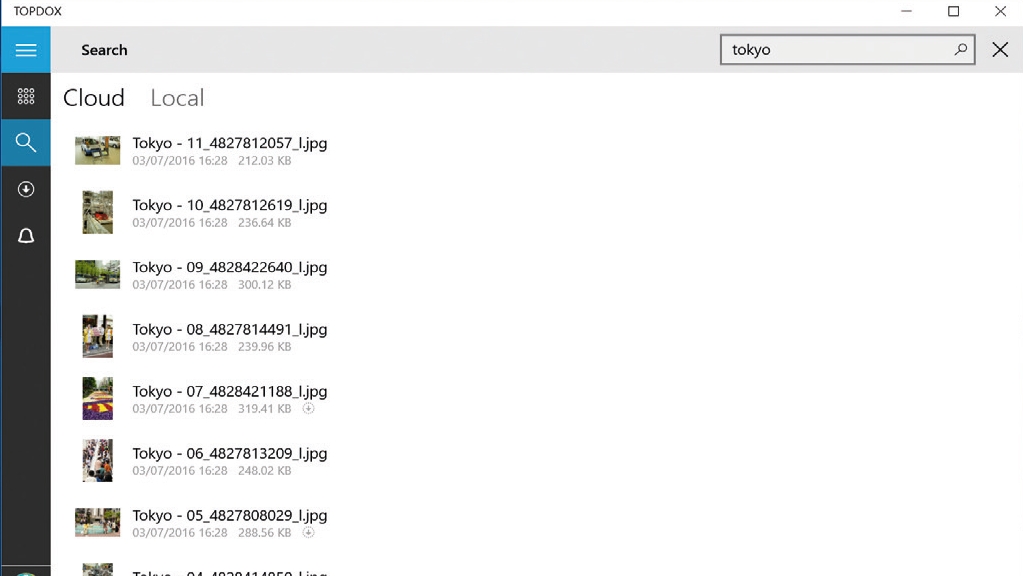
5. Find your files
If you have a lot of stuff in the cloud, it can be hard to remember what’s stored where.
Luckily, TopDox comes with its own global search tool, which will find all your cloud-based files as well as your local ones. To find a file select the magnifying glass icon from the left menu (or the top bar in Drive view) and type what you’re looking for into the search box.

6. View a document
If you want to view a document that you or someone else has uploaded, double-clicking its icon will open it within the TopDox app.
Use the back/forward arrows at the bottom of the screen to move from page to page, and the magnifying glass to zoom in and out. To save the document as a PDF tap ‘…’, then ‘Print’ to open the Microsoft Print to PDF viewing screen.

7. View a photo or video
TopDox also enables you to see photos and videos stored in the cloud. Double-click to open the file you wish you view.
After downloading it will open in TopDox’s main window. With photos you can use the magnifying-glass tools in the bottom-right corner to zoom in or out.
Videos include playback and volume controls and even allow you to cast video to another device.
8. Edit a document
One thing you can’t do in the Windows 10 version of TopDox is edit Microsoft Office or OpenOffice documents from within the app – you’ll need to use the relevant app on your PC instead.
But, if you’ve linked TopDox to your Google Drive account, you can edit Google Docs as you would if you were using any other web browser with all the text tools at your disposal.
- Enjoyed this article? Discover how to get the most from your PC and new things to do in Windows Help & Advice. Take advantage of an exclusive offer in our sampler today.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful