
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Ten years ago, a laptop was an expensive and specialist purchase, but today it's become an everyday item widely used as people's primary work device.
That casualness breeds complacency and that leads to leaving a laptop on the train, unattended in a café or library and having it stolen (we do still have libraries don't we?).
That's besides it being an easy target when someone manages to break into your home. So what are the options for protecting your vulnerable laptop or netbook?
Article continues belowWe've looked at solid ways of bolstering the log-in password and ways to protect the sensitive services accessed through your web browser. But once a device is in the hands of a stranger, the defensive position has to change.
One tactic that we'll get to is encryption from single files to full-drive encryption: it's a way you can lock-down sensitive information in a way that even the FBI can't crack.
The alternative approach is to go on the offensive. There are now a number of well known stories about people managing to get laptops recovered by the police using third-party remote access software.
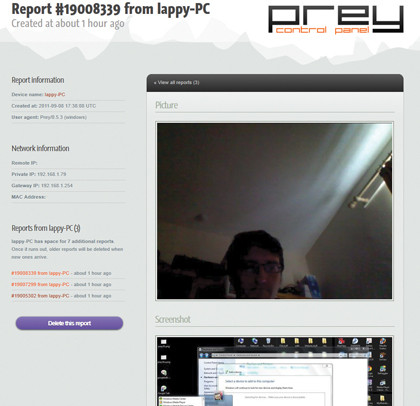
One of the more recent was Greg Martin, a UK-based security expert who used to work for both NASA and the FBI. He had his Mac Book Pro stolen during the London riots. He was running a rather excellent open source protection system called Prey, which can be downloaded from preyproject.com.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Using this, he logged his laptop as missing within the Prey system; as soon as it came back online he was emailed a notification. From that point onwards, Greg's criminal friend was doomed. Able to watch him surf the web, taking webcam shots of him as he did, eventually he logged onto Facebook and that was his fate sealed.
With a full breakdown of his name, age, secondary school, IP address, ISP, address and photos both from Facebook and the laptop's webcam, Greg simply supplied the details to the police and let them reclaim his property.
The biggest potential stumbling block with this type of software is whether the perpetrator can figure out how to log onto the system intact or not. It's a good argument for leaving a Guest account active, so you can be assured the tracking software will always be accessed. Prey is a fabulous system that also has software that can cover your desktop and mobile phones.
The other common solution is Logmein.com for PC and Macs, which provides a basic free service. This is focused more on enabling remote log-ins to your system, rather than reclaiming stolen or lost devices. However there is a stealth mode available in Logmein.com, so if someone is using the system you're able to log in covertly, take a few screen grabs and webcam shots, and watch them browse the internet.
For your eyes only
We've already touched on the issue that a solid password isn't much help, if an attacker can get their hands physically on the hard drive. Again, on a desktop system this may seem less of an issue, but with a laptop or netbook the likelihood of having a device stolen is far higher.
Encryption is the answer and of course more passwords, probably. Both the Business and Ultimate editions of Windows 7 and Vista both come with file, folder and full-drive encryption options built in.
Right-click on folder or file, select Properties > Advanced and click Encrypt contents to do just that. There are no passwords involved and it's locked to the system and user log-in details. This system generates a cypher key that needs to be backed up. Windows will prompt you to do so, as without it, if Windows needs to be reinstalled you won't be able to access any encrypted data.
The Ultimate and Business editions of Windows 7 and Vista both come with a full-drive encryption solution called BitLocker. This works slightly differently for the Windows boot partition and all other partitions. The big difference is that for all other partitions you're able to just use a password. For the primary boot partition, your hardware has to use a compatible Trusted Platform Module (TPM), more common on business-targeted desktops and laptops than home consumer systems.
The quickest way to check is to fire it up by opening the Start Menu, typing BitLocker and pressing return. If you click the Turn On BitLocker link for the Windows drive, marked with a Windows flag, you'll be given the good or bad news. Often the TPM will need to be switched on within the BIOS and then initialised using the TPM link from the BitLocker Control Panel that generates the secret key.
Once initiated it'll begin encrypting the entire drive, which can take quite a while, so set aside a few hours of downtime if you plan this.
BitLocker To Go extends the protection to removable devices. If you're not running a version of Windows that supports encryption worry not.
The TrueCrypt open source system is a long standing, well regarded and highly secure partition, full drive and virtual drive encryption solution. It'll happily encrypt a Windows boot partition, even on the fly as you continue to use it, along with handling the pre-boot environment.
Other cool extras include its ability to create a file that's then mounted as an encrypted virtual partition, while 'hidden modes' enable you to enter an emergency encryption code that keeps the true partition hidden but reveals a working fake one.
If these all seem a little full-on then we'd also suggest AXCrypt. This sweet little freeware program is right up to date, supporting 32-bit and 64-bit versions of Windows 7 and back to Windows 9x. Once installed it enables you to encrypt single files and folders with just a right click and the entry of a password. Job done, and that will be all of your stuff protected end-to-end - from on the internet to your home devices.
- 1
- 2
Current page: How to protect your laptop from data theft
Next Page How to track a stolen laptop with Prey