How to use Linux Commands
Linux is a multi-user operating system, even if you are the only person using your computer. The most basic of systems has two users: you and the superuser, also called root. Every file or directory is owned by a user and has settings, called permissions, that specify who can read or write to it.
This safeguards your files from being overwritten by another user, or possibly even read by them if so set. It also safeguards system files because they are owned by root and can only be changed by root. This includes writing to system directories, so only the root user can install new software there.
So how do you install software? See the 'Becoming root' box opposite for the answer. One word of caution when using data on multiple computers, such as with an external hard disk. While you may see your username as a name, say johnny99, the computer sees and stores it as a number, a UID or user ID.
During installation, your distro will have created a root user, who always has a UID of 0, and a normal user. Most distros start at 1000 for the first general user, but some start at 500. The point is, it's that number stored on the disk as the owner of a file, so the same username may not own the file when you move the disk to another computer.
Create a user
Every user has a home directory. This is usually /home/username but it can actually be anywhere – the user created to run a web server will have a home directory somewhere like /var/www. In addition to users, Linux also has groups.
A group is basically a collection of users. For example if you have a USB scanner on your computer, you often need to be a member of the scanner group to be able to use it. Now that we understand usernames, groups, UIDs and home directories, we can create a user:
sudo useradd -m -c "John Smith" -g users -G scanner,audio john
Sign up for breaking news, reviews, opinion, top tech deals, and more.
We use sudo here because only the root user can create users. The -m option creates a home directory at /home/john, -c specifies a comment to store for the user, which is usually the user's full name, -g sets the primary group of the user, while -G adds secondary groups.
Finally, we give the username. Not all of these options are necessary – if you omit -g, a default group will be used. Some distros use a single group called users for all non-system users, while others create a separate group for each user. The groupadd command works in a similar way, as do both of their counterparts – userdel and groupdel.
Add a password
We have created a user but he cannot log in yet because we haven't given him a password.
sudo passwd john
will ask you for the password twice. The passwd command can also be used to change the password of an existing account. If you run it without sudo or a username, however, it will change your own user's password, because only root can set passwords for anyone else.
It is considered good practice to change passwords regularly, and you can enforce this by using passwd:
sudo passwd --maxdays 60 -warndays 7 john
This password will become invalid after 60 days and john will be warned about the expiry a week before. The usual rules about passwords – make them long and mixed case, preferably with numbers – apply here, and doubly so to the root password, the key to the kingdom.
User details are stored in /etc/passwd, which may be edited should you wish to change them. However, making a mistake could prevent you from logging in, so use vipw to edit it. This loads a copy of /etc/passwd into your preferred editor (as defined in $EDITOR) and checks its validity when you save it, before replacing the existing file. The format of /etc/passwd is explained fully with:
man 5 passwd
Transfer ownership
If you want to change the owner of a file, you need chown:
chown john somefile
chown john:users someotherfile
chown john: someotherfile
chown -R john: somedir
The first makes john the owner of a single file. The second command also changes the group. If you do not give a group after the colon, as in the third example, the group is changed to the user's default group. When applied to a directory, the -R option also changes all files and sub-directories in that directory.
You can change just the group with chgrp. These commands must be run as root. Changing file permissions is done with chmod.
Becoming root
Almost all of the user management commands require root access. The superuser, often referred to as root, can do anything anywhere, regardless of any permissions. So how does a humble user do anything that requires root privileges? There are two ways of doing this.
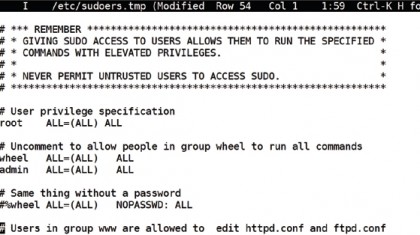
The traditional way is to use the su (for switch user) command, which allows you to become another user, provided you know their password. Run su in a terminal (it switches to root if you don't specify a user), and it will ask for the root password. Once you have entered this, you are root in that terminal session, and can do anything you like – muhahaha!
Of course, this is a bit risky, especially if you don't log straight out after doing what you need. It also means that you have to give the root password, and therefore full access, to any user who needs to run a root command – so sudo was invented. Sudo is used to run individual commands as root (or another user) but does not require you to know the root password. Instead, the root user must have set things up to allow you to run some or all commands as root, so it asks for your password. The normal installation of most distros allows the first user created to have sudo rights to everything, so you can install software, or do anything else, without ever having to log in as root, or spread the root password.
In fact, some distros have no root password by default, and sudo is the only way to run administrative commands. Sudo can be used to give individual users the right to execute only specific commands, plus it records every command it runs in the system log, along with who ran it, giving a far more secure and accountable system.
Current page: Linux Commands: User accounts
Prev Page Linux Commands: Core terminal programs Next Page Linux Commands: Accessing help with Man pages