Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
It's grown into an essential tool for anyone interested in online security. NMap was originally a Linux command line tool, but it's been ported to Windows and given a snazzy GUI front end called Zenmap. The underlying NMap has a huge number of command line options, but Zenmap makes it considerably easier to use. Get the Windows version here.
The installer includes the WinPcap driver software that forms the special packets needed to probe the TCP/IP stacks of remote hosts, and gain information identifying the OS running on that host.
Once installation is complete, run Zenap and the user interface should appear. Enter the IP address of a computer on your own network in the 'Target' box, and select 'Quick scan' on the 'Profile' menu. Click 'Scan'. This produces an overview of which ports are open and listening on the target PC. This includes the MAC address of the target's network card, which Zenmap uses to determine the manufacturer.
This is the kind of information that a hacker will use to look up exploits that may grant him access or the ability to create mayhem due to bugs in the firmware on the network card. For a more comprehensive view of the machine, select 'Intense scan, all TCP ports' and click 'Scan'.
This fires a large number of packets at all 65535 ports on the target PC. It also interrogates the machine, revealing clues about its running OS. This information is vital in determining the next course of action to penetrate the system.
One of Zenmap's particularly useful features is the ability to scan an entire subnet for targets, which it then interrogates for details. Simply substitute the last number in the IP address for an asterisk ('192.168.0.*' for example). This is also a great way to see if anything has been connected to your network secretly.
NBTEnum
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Once we know what targets are available to a hacker who has penetrated our defences and can see our network, the next task is to try to discover what facilities each machine offers for exploit. This is important because, even if the hacker can't exploit them directly, they may well be able to interrogate them to produce much more useful information.
NBTEnum, originally written by Reed Arvin, is a very old utility that is now difficult to find, but don't let its age or obscurity fool you. NBTEnum can uncover shockingly large amounts of information from an unprotected Windows PC just by asking for it. You can currently download NBTEnum from the Packet Storm security website.
Open the ZIP file and move the contents into a new folder. NBTEnum is a command line utility, so open a command prompt and navigate to its directory.
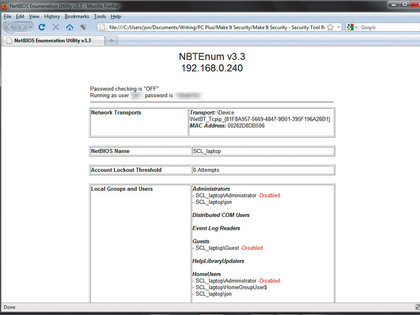
To run enum, enter the command NBTEnum -q , substituting the address of a Windows PC on your network where appropriate. If the target accepts connection requests via its NetBIOS service, NBTEnum will create a web page detailing what this shockingly indiscrete service tells it.
Open this in a browser and you should, at minimum, see that NBTEnum has enumerated the shares (if any) that the target says are available for remote mounting. If you know a username and password on the target computer, you can reveal a huge amount of information.
Enter NBTEnum -s , making the necessary substitutions. NBTEnum generates more verbiage, but the resultant web page can offer masses of detail.
NBTEnum can also recover the open shares, users and groups, whether accounts are enabled, their lockout threshold and on Windows 7, a full list of services including which ones are currently running. This is all still possible because so many people insist on having no password, one that is simply guessed, or one that is the same as their username.
When I was a network security consultant, finding a network populated by targets running older versions of Windows usually meant a day running NBTEnum against them with a username of 'Guest' and no password. By default, the guest account was enabled and unprotected - perfect to shock network administrators into disabling such accounts.
InSSIDer
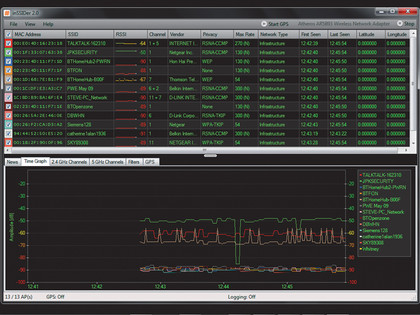
We live in an increasingly wireless world, but the nature of a wireless signal means the information it carries is broadcast over a wide area. There are a large number of tools that can be used to survey the local Wi-Fi landscape, but one of the best is the Windows port of InSSIDder 2 by Metageek. You can download InSSIDer here.
When run, InSSIDer begins discovering and enumerating the Wi-Fi networks in range. The top half of the interface fills with details of the networks, including their security level. Those with 'none' are wide open for anyone to log in and look around. Those using the older WEP protection are potentially vulnerable to attack, because the algorithm has weaknesses that can be exploited.
In the average neighbourhood, there could be as many as three dozen networks in range, some without any protection. InSSIDer's also displays the Wi-Fi channel used by each router within range.
Change yours to a channel not used in your area and you could see an improvement in overall data transfer speeds.