Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
What tools do security professionals and hackers rely on? It's a question whose answer changes as quickly as the online threat landscape, but there are some favourites in the current toolkit that never go out of fashion.
Far from being major, comprehensive attack platforms, these utilities usually do one obscure thing quickly and reliably. Their developers simply keep updating them to add new facilities and, crucially, to make them easier to use.
Some of these utilities are online, while others can be carried on a USB pen drive. The common factor is that they're available to anyone. While every security researcher and hacker typically carries a small armoury of such tools, they have their own ways of using them to assess security or mount attacks.
Dig services
The first step in mounting an attack or securing an online information resource is to assess what is visible to others over the internet. For large organisations, more than just the mail and web servers will be visible. Sometimes this is a mistake on the part of the network administrator, but sometimes it's done for misplaced expediency.
However, both these reasons can lead to a full-scale exploit of the internal network. The best and safest way to assess what's visible is to use a public Dig service.
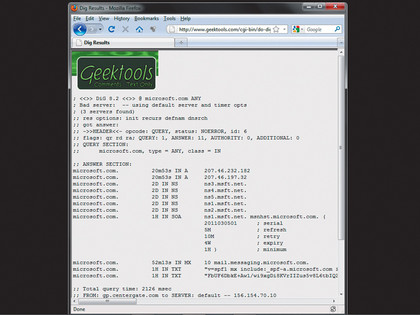
Dig stands for 'Domain Information Groper'. Such services interrogate the global DNS system for details about a target. Using a Dig service, you can uncover several classes of information, including the local DNS servers, web servers and mail servers (mail exchangers in DNS speak). It's sometimes also possible to uncover plenty of addresses of computers that really shouldn't be online, but which someone has added to DNS in the mistaken belief that others won't know they're there.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
This goes against the maxim that 'security through obscurity is no security'. One such Dig service is provided here. To get started, enter the name of a domain (without the 'www.') and click the button marked 'Dig'. Depending on how much information DNS holds about a domain, Dig's output can be very comprehensive, and gives a good overview of the parts of a network that can be seen from the internet.
The most important part of this information begins after the line containing the words 'ANSWER SECTION'. This gives the fixed IP addresses of any internet-facing servers. For a website hosted by a third-party company, this will be the IP address of the shared server on which the site resides.
You can focus the information returned by selecting the 'Type' dropdown menu. 'Network addresses' will return only the IP addresses of any server that can be contacted directly. You can also return only information about the mail exchangers and the domain's authoritative DNS nameservers.
Most Dig services let you try something called a zone transfer. This shouldn't be possible these days, but back when network administrators were less focused on security than keeping internet connectivity going, zone transfers were possible from many DNS nameservers.
A zone transfer is a transfer of authoritative domain information. It's meant to occur only between nameservers, but poorly configured nameservers will let anyone request one.
A zone transfer contains a long list of computers and their IP addresses, which, while not listed in DNS, have a direct connection to the internet and are vulnerable to attack. This information is ideal for hackers, who need to scan a range of IP addresses to build a list of targets without tripping any intrusion detection systems.
NMap
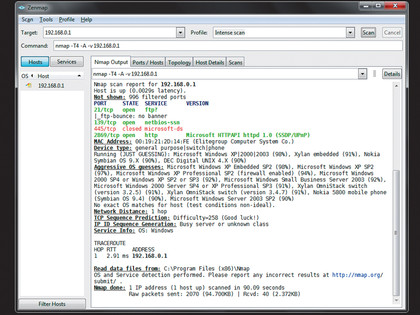
The next step is knowing which hosts are available on a network, and what ports they have open. The great granddaddy of port mappers is NMap.