Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Locked bits
With performance worries neatly brushed under the rug, we can go back to wondering why we want encryption and how we can easily implement something useful.
The idea of encryption is to put up a barrier so complicated to vault, it's not worth the attacker's time to overcome it, but there's always a chance that they could discover the key or back door, or you might reveal the data by accident. It's therefore important to follow procedures when creating passwords and handling data - the classic gaffe being getting drunk and leaving an unencrypted copy of your data in a pub or on a train.
For protection we're going to look at a number of solutions that cover local files on specific drives, including removable drives, encryption of emails and files sent from your local machine, and full-system encryption of the boot drive. A number of the tools we've used here come with Windows, but we also turned to freely-available, open-source options that are just as secure, but run on most operating systems too.
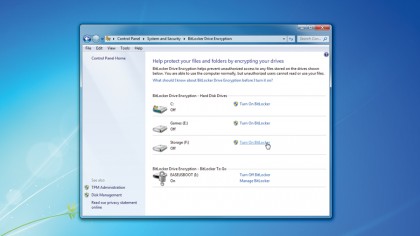
Let's kick things off by covering BitLocker, which is the official full-drive encryption system offered by Microsoft. The major limitation of BitLocker is that it's only available to the Enterprise and Ultimate Editions of Windows Vista and Windows 7, along with Windows 8 Pro and Enterprise Editions. It's something of a shame it's not available to all, because it offers a well-integrated and straightforward encryption system, but we guess Microsoft didn't want your average Joe securing their data then locking themselves out from it.
You can easily find BitLocker settings under the System and Security Control Panel. Just type BitLocker into the Start Menu (what do you mean Microsoft stole it?) and select 'BitLocker Drive Encryption'. For any drives other than the boot partition, including removable drives, there are really no restrictions; just activate BitLocker for that drive via the Control Panel.
BitLocker supports standard password protection and smartcard readers with a PIN, but for home use the latter option isn't likely. Just set a password that's at least eight characters long (which you should print and keep it somewhere safe, just in case) and Windows will take care of the rest.
For the Windows boot drive, you'll need a spare inserted USB drive so that BitLocker can store the encryption key. Ideally you want a system kitted out with a Trusted Platform Module, as this takes care of all the boot-time key handling and authentication in total security. The extra complexity is required as the BitLocker system has to handle the boot-time transfer from the BIOS to a fully-encrypted Windows system. For a non-TPM system, it boots via the USB drive that stores the encryption keys and the code to swap the boot process to a much more secure partition.
Sign up for breaking news, reviews, opinion, top tech deals, and more.

We've mentioned the Trusted Platform Module (or TPM), but not really explained what it is. Much was made of it when it was first conceived, but it's most often found on business systems as an optional extra. The TPM provides cryptography features to the PC, including secure key generation and storage, true random number generation and system authentication.
As part of a secure ecosystem the TPM alone can be used to authenticate a system, or it can be used alongside a PIN or also a USB key. So for example, if a drive is removed and transferred to another PC, even with the PIN and with a USB key, the TPM won't decipher the data.
True encryption
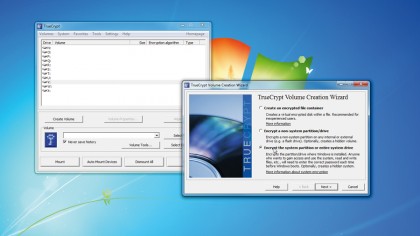
In its hallmark style, Microsoft has made BitLocker as useless as possible by limiting its availability. Well done Microsoft. This isn't a problem though, because the open source community supplies arguably the best cross-platform, high-performance, full-system encryption solution around in the form of TrueCrypt.