How to get started with Tor Browser - a web browser designed for privacy
Using the secure browser to explore the dark web
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
If you seek utmost privacy when surfing the web, the Tor browser is your best bet. This free, open-source browser routes your traffic through multiple volunteer-run servers, scrambling your data and making it very challenging for third parties to track you.
Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for.
This guide dives deep into Tor, explaining how it works, its pros and cons, and how to utilize it to protect your online privacy.
Exclusive offer: Get real-time data from any website with Web Scraping API
Start your 7-day free trial with 1K requests and scrape data with a click. Unlock 100+ ready-made scraping templates, 100% success rate, advanced geo-targeting, and automated IP rotation. Don’t miss out – collect data without CAPTCHAs or geo-restrictions.
TechRadar Pro Approved Sponsored Offer
What is Tor?
Tor is an abbreviation for The Onion Router. It's an overlay network that enables encrypted, anonymous connections between computers. This protocol, a layer built atop the traditional internet layer, routes communication between random servers (called nodes or relays) to obscure the source. These servers, numbering in the thousands, are operated by volunteers worldwide.
While often used interchangeably, Tor and Tor Browser aren’t the same thing. Tor is a network designed to route traffic through multiple servers. The Tor Browser is a specific web browser, based on Firefox, that utilizes the Tor protocol to enable private browsing.
You can use Tor without the browser, but the Tor Browser is the most popular and user-friendly way people interact with the protocol.
The Tor browser routes your online requests through multiple nodes to obscure them from prying eyes. It conceals your location and other personal data that are exposed when using standard browsers.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
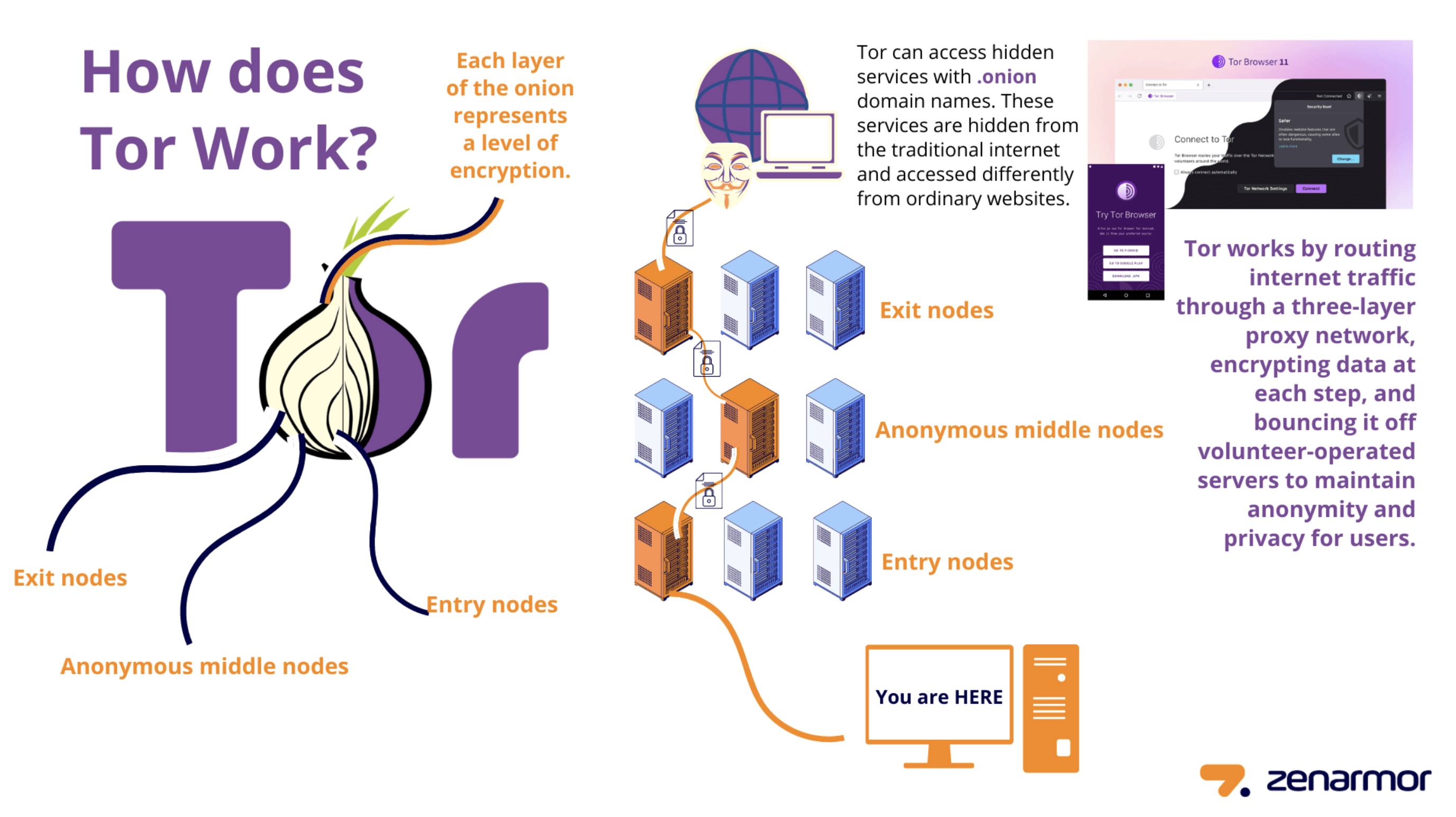
As illustrated above, the Tor browser routes your online traffic through at least three nodes: an entry node, a middle node, and an exit node.
The entry node knows your IP address but not the intended destination. The middle node knows the previous node but not your IP address or what you’ve requested online. The exit node knows what you’ve requested and connects you to it, but it doesn’t know your device and its IP address.
To put it less technically, the entry node knows who you are but not where you’re going. The middle node neither knows who you are nor where you’re going. The exit node knows where you’re going, but not who you are.
The above mechanism conceals your location and browsing activities from third parties like internet service providers (ISPs), advertisers, and web monitoring apps. However, Tor doesn’t guarantee 100% anonymity. Data can still be exposed if you log in to certain sites or download files over the network.
Who created Tor?
The Onion Router (Tor) was developed in the 1990s by researchers and computer scientists at the United States Naval Research Laboratory. It derives its name from the encryption system, which is structured like the layers of an onion.
Initially created to protect U.S. intelligence communications, Tor was released for public use in 2003. In 2004, the Naval Research Laboratory then released the code and made it open-source. Since then, volunteers and sponsors around the globe have maintained Tor and the Tor Browser.
Since its public release, researchers have discovered various vulnerabilities in Tor, which have been quickly patched. The Tor protocol isn’t 100% failsafe, but it goes a long way in preserving privacy when surfing the web.
How to install and use the Tor browser
1. Download the Tor browser
You can download the Tor browser from the official website, Torproject.org. The browser is available on Windows, macOS, Linux, and Android. There is no official Tor version for iOS because Apple requires all iOS browsers to use WebKit, which affects Tor's privacy features.
Click on the download button for your relevant operating system, and the download should begin immediately.
2. Install the Tor browser
Open the downloaded file on your device to begin the installation process. The process is similar to installing any other software – follow the on-screen instructions and wait for the installation to complete. Once complete, you can add Tor to your shortcuts menu for easy access. You can now open the browser.
3. Connect to the Tor network
To surf the web privately, you need to connect to the Tor network from your browser. You can do it manually or automatically. Manually implies clicking the Connect button each time you open Tor, while automatically means an automatic connection whenever you open the Tor browser.
Automatic connection is the most convenient option. To enable it, check the Always connect automatically button on the homepage.
To connect manually for the first time, click on the Connect button on the homepage and wait for Tor to establish a connection.
4. Explore the web
With your Tor connection established, you can begin surfing the web with the utmost privacy. Like standard browsers, Tor has an address bar where you’ll type the domain you want to visit.
For example, we typed TechRadar.com into the address bar and accessed the website without any issues.
You can access many other sites via the Tor browser, and your requests will be routed through multiple servers to avoid monitoring. However, some websites consider Tor traffic suspicious and make users jump through several hoops, including CAPTCHAs. Others outrightly block Tor users from accessing their platform, so you might not be able to open some popular platforms.
Likewise, you’ll experience slower browsing speeds when browsing via Tor, as your requests get bounced through several servers before being processed. These are tradeoffs to be aware of as a Tor browser user.
5. Search the web
Tor uses DuckDuckGo as its default search engine, which is expected for a privacy-focused browser. DuckDuckGo is a search engine designed to maximize privacy. It doesn’t track your IP address, search history, and other personal data.
DuckDuckGo uses its web crawler and also curates data from over 400+ sources, including Google and Bing. Hence, you’ll see accurate search results similar to searching on Google.
The tradeoff is that you don’t get personalized search results, as DuckDuckGo doesn’t collect user data. But this tradeoff is worthwhile when seeking to browse with the utmost privacy.
6. Monitor your traffic routing
We’ve talked about the Tor protocol bouncing your traffic through multiple remote servers. However, seeing is believing, and the Tor browser allows you to see which servers your traffic passes through.
Whenever you visit any website, click the circuit button next to the domain to open a menu displaying the servers through which your traffic passes. As illustrated in the screenshot below, our request was routed through servers in Luxembourg, Germany, and Austria when visiting TechRadar.com.
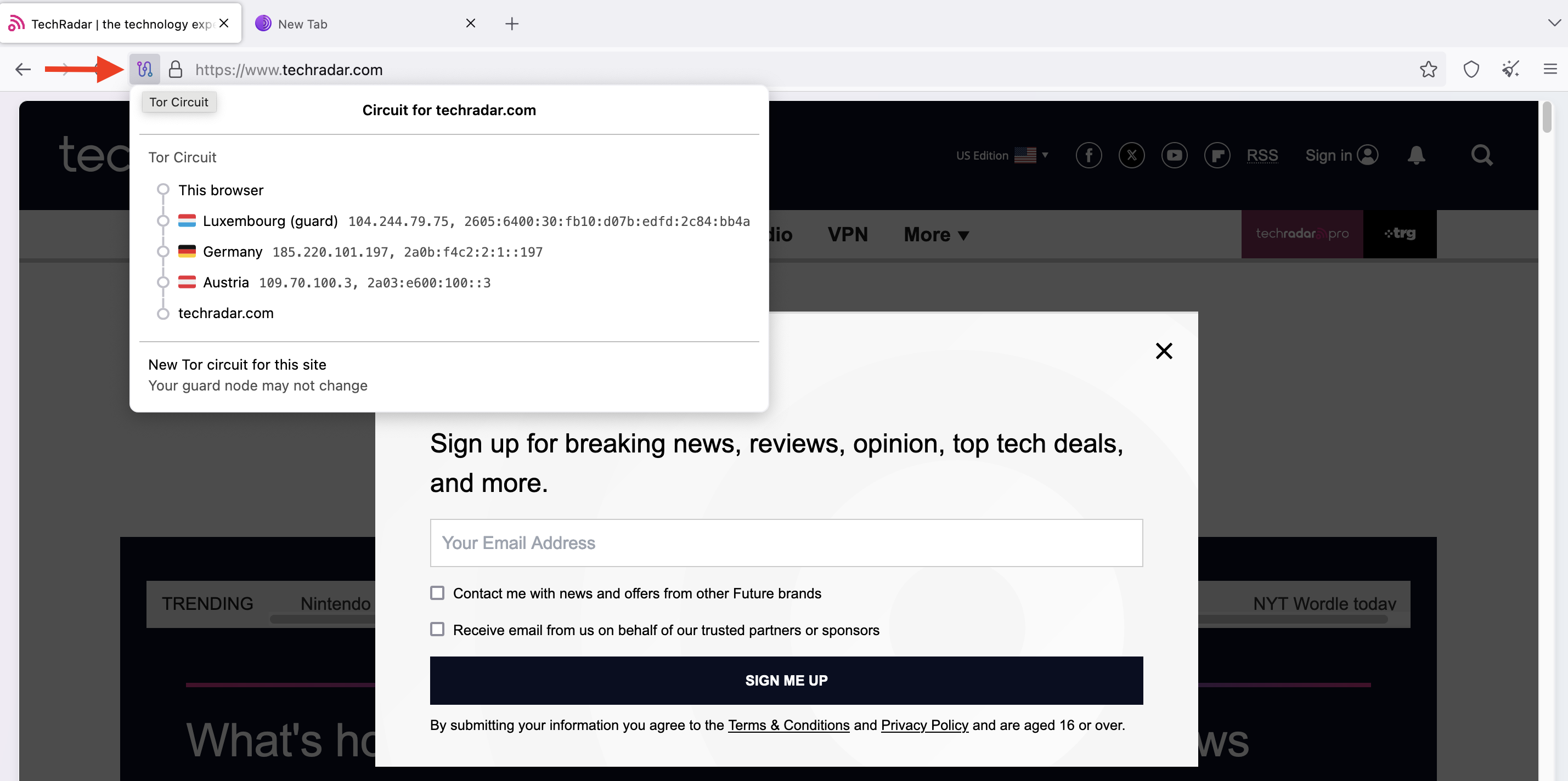
Each server our request passed through had a distinct IP address. The website could only see the IP address of the last server (exit node), not our actual IP address.
7. Using a new circuit
If you’re having trouble accessing a website via Tor, it could be that a node, especially the exit node, has a problem connecting to the site. We discussed how some websites block Tor traffic entirely; they do this by blocking IP addresses known to be Tor exit nodes.
If you’re facing a connectivity issue, you can troubleshoot it by choosing a new circuit. This option routes your traffic through different nodes and attempts a new connection.
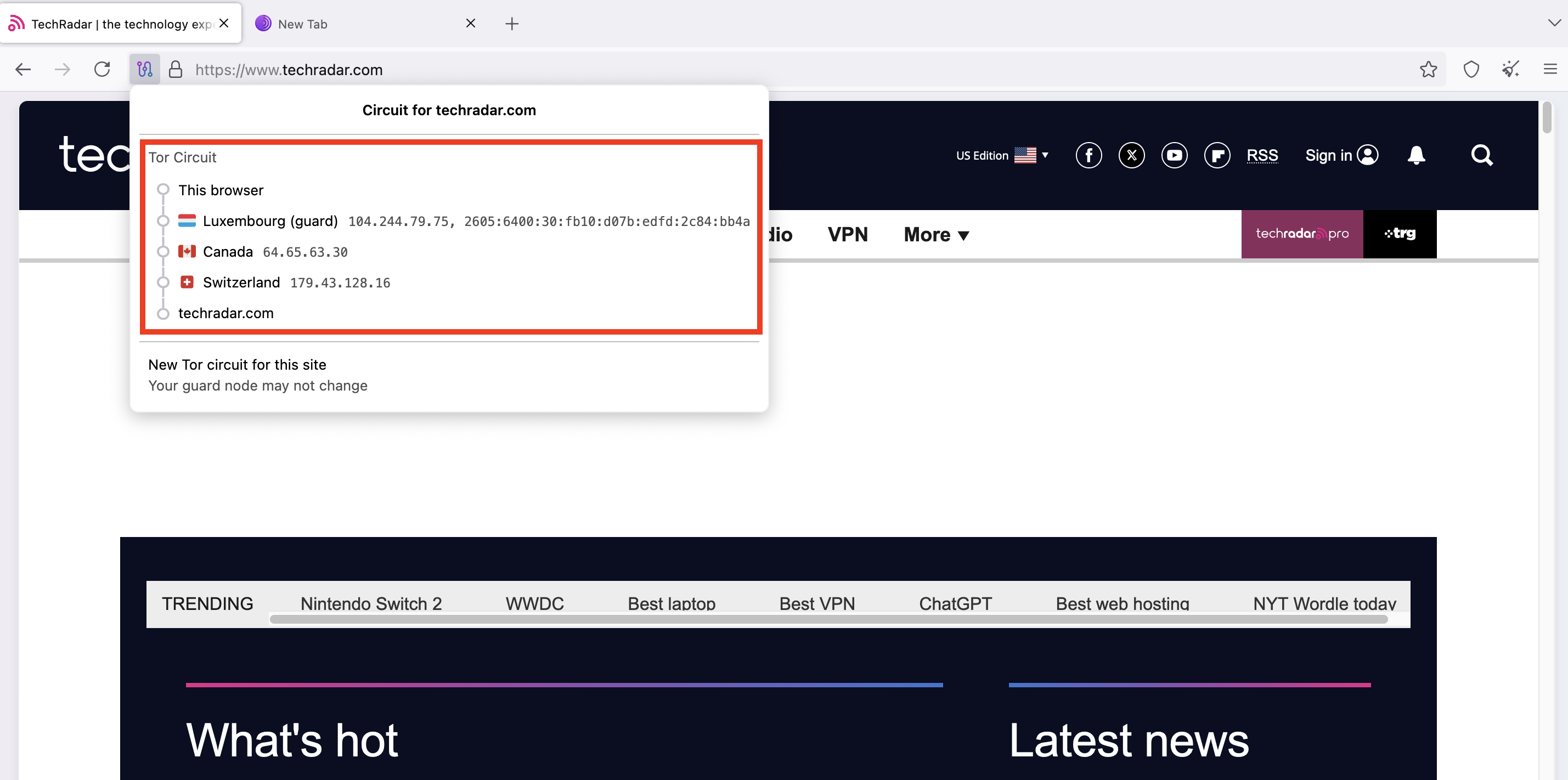
To use a new circuit, click the circuit button next to the domain. Then, click on New Tor circuit for this site, as illustrated below. This button will reload the site with a new circuit, which may solve the connection issue.
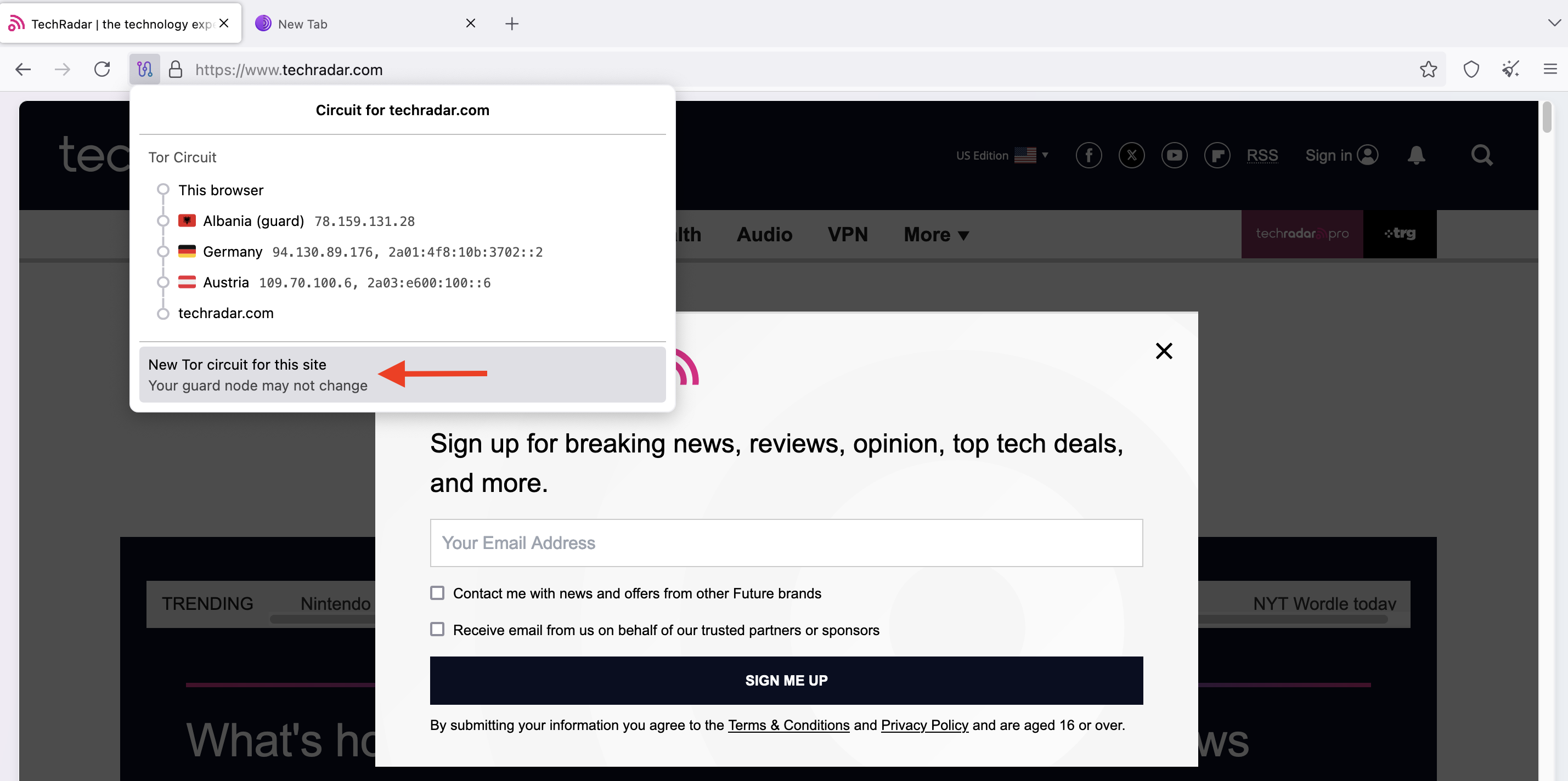
In the screenshot below, you can confirm that the nodes have changed after clicking the New Tor circuit button. It followed the Luxembourg > Canada > Switzerland node path, rather than the previous Albania > Germany > Austria path shown in the image above.
8. Enhancing your security
By default, Tor has stricter privacy settings than most standard web browsers. However, the default settings aren’t the farthest you can go. Users can take further steps to maximize privacy when browsing with Tor.
When visiting any website via Tor, you can click the shield icon in the top right corner, and a Security Level menu will appear.
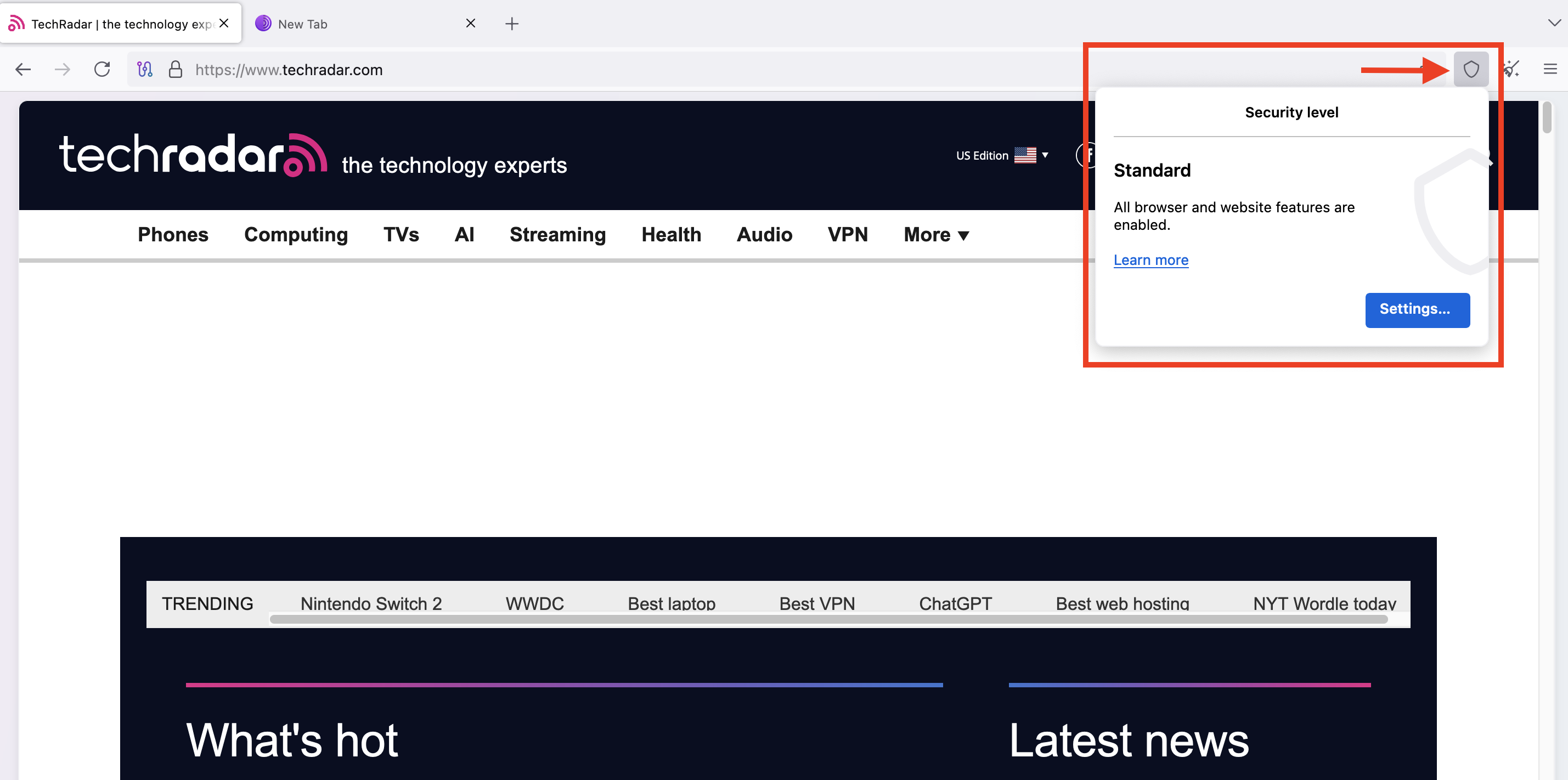
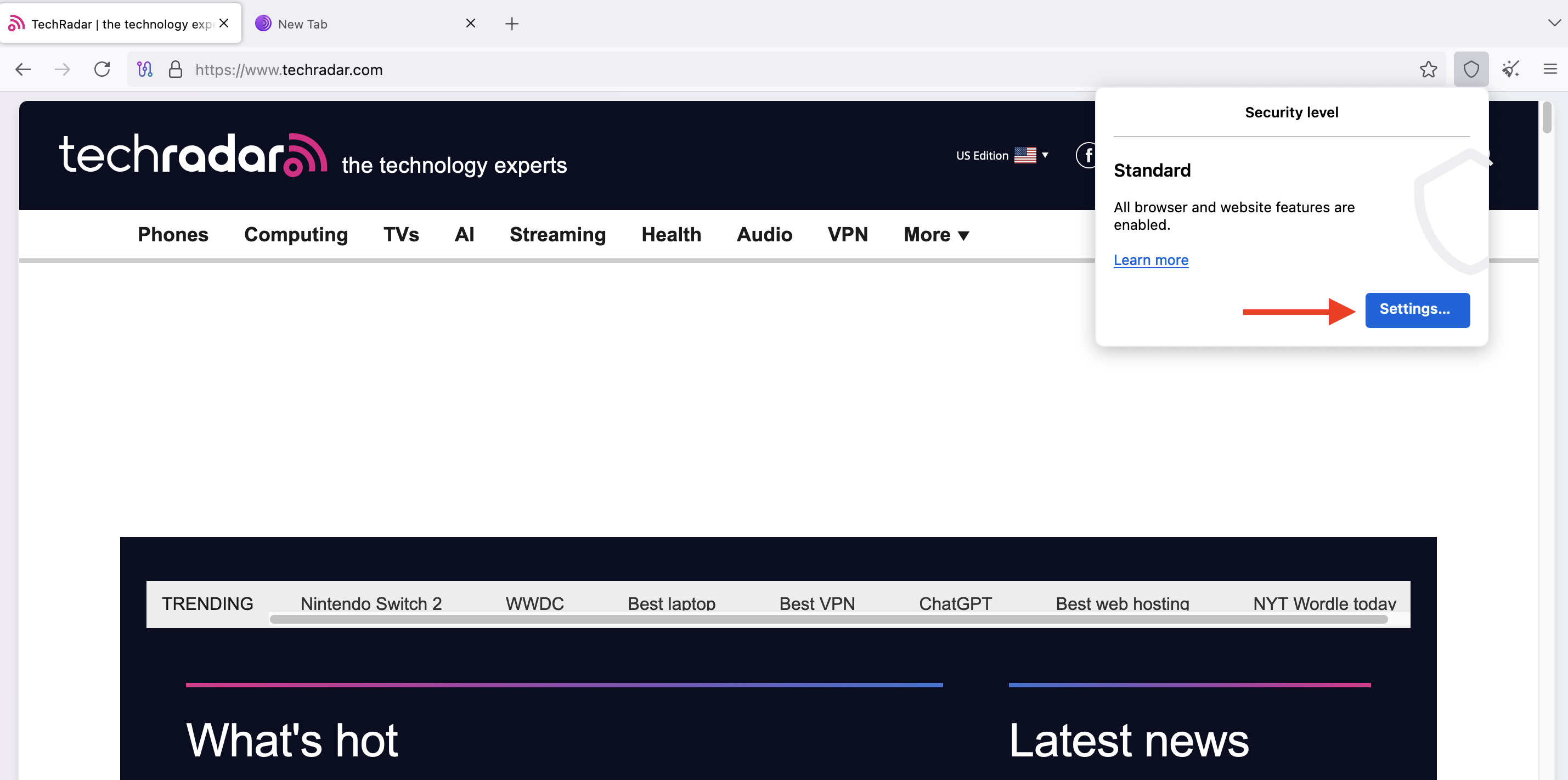
By default, Tor uses the Standard security level, but you can upgrade it to Safer or Safest. To do this, click the Settings button in the Shield popup menu.
Then, choose your desired security level. The Safer option disables all potentially dangerous website features, while the Safest option enables only the features necessary for basic website functions.
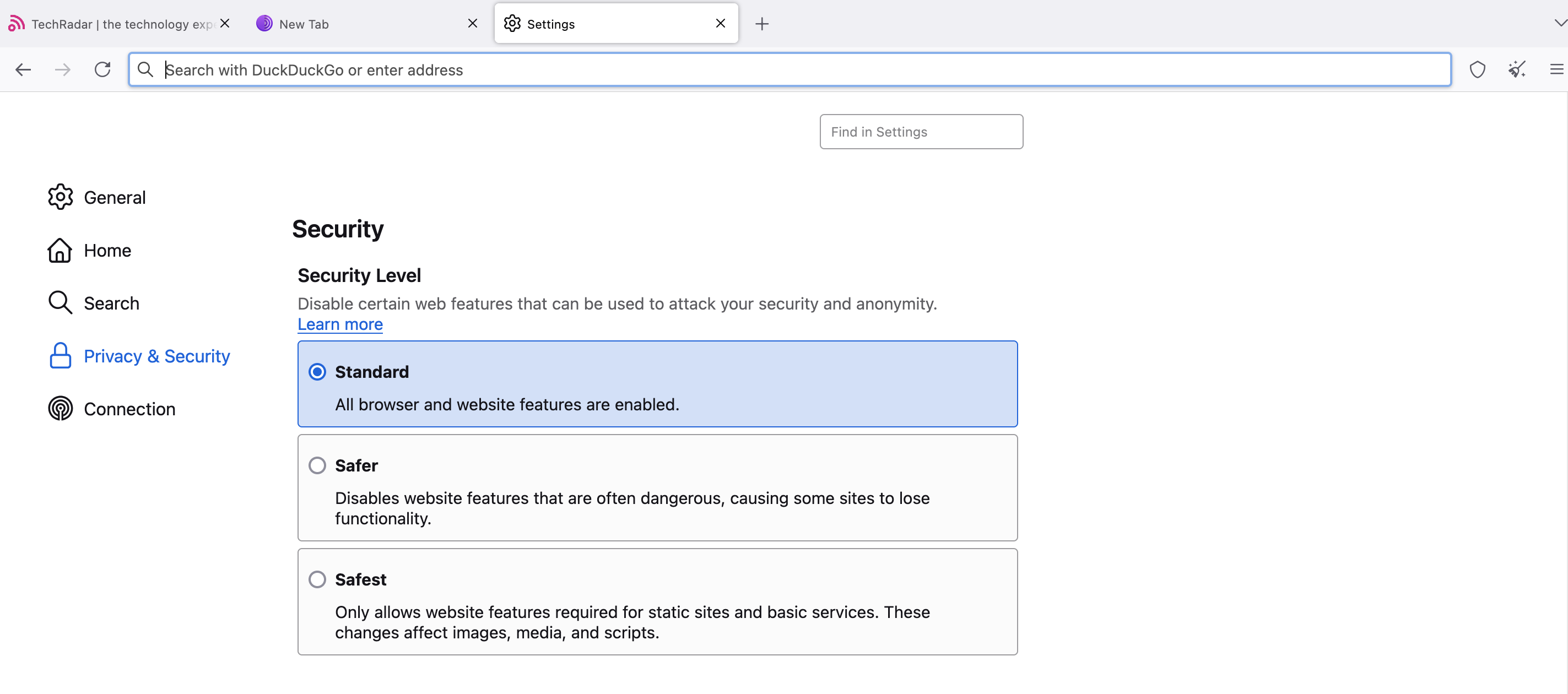
For example, in Safer mode, JavaScript is turned off on non-HTTPS (insecure) sites, but in Safest mode, JavaScript is turned off entirely for all sites. Images load normally in Safer mode, but some complex images may not load in Safest mode.
Upgrading to Safer or Safest mode improves your security but affects website functionality, so you should be aware of the tradeoffs. The good thing is you can always switch between different modes when needed.
To maximize security, you should avoid logging into personal accounts, such as Facebook and Gmail, via Tor. Although the Tor Browser is designed with strict privacy, logging into personal accounts can expose your real identity.
The same applies to downloading files, which often contain tracker elements. You should avoid downloading files via Tor to maximize your anonymity.
Websites can install cookies on your Tor browser, just as they can on standard browsers. The difference is that Tor deletes all installed cookies and data whenever you close the browser. This feature can’t be changed because it’s integral to Tor’s privacy focus.
However, you can block specific websites from installing cookies on your browser. To do this, click on the three horizontal lines in the top-right corner, then open Settings.
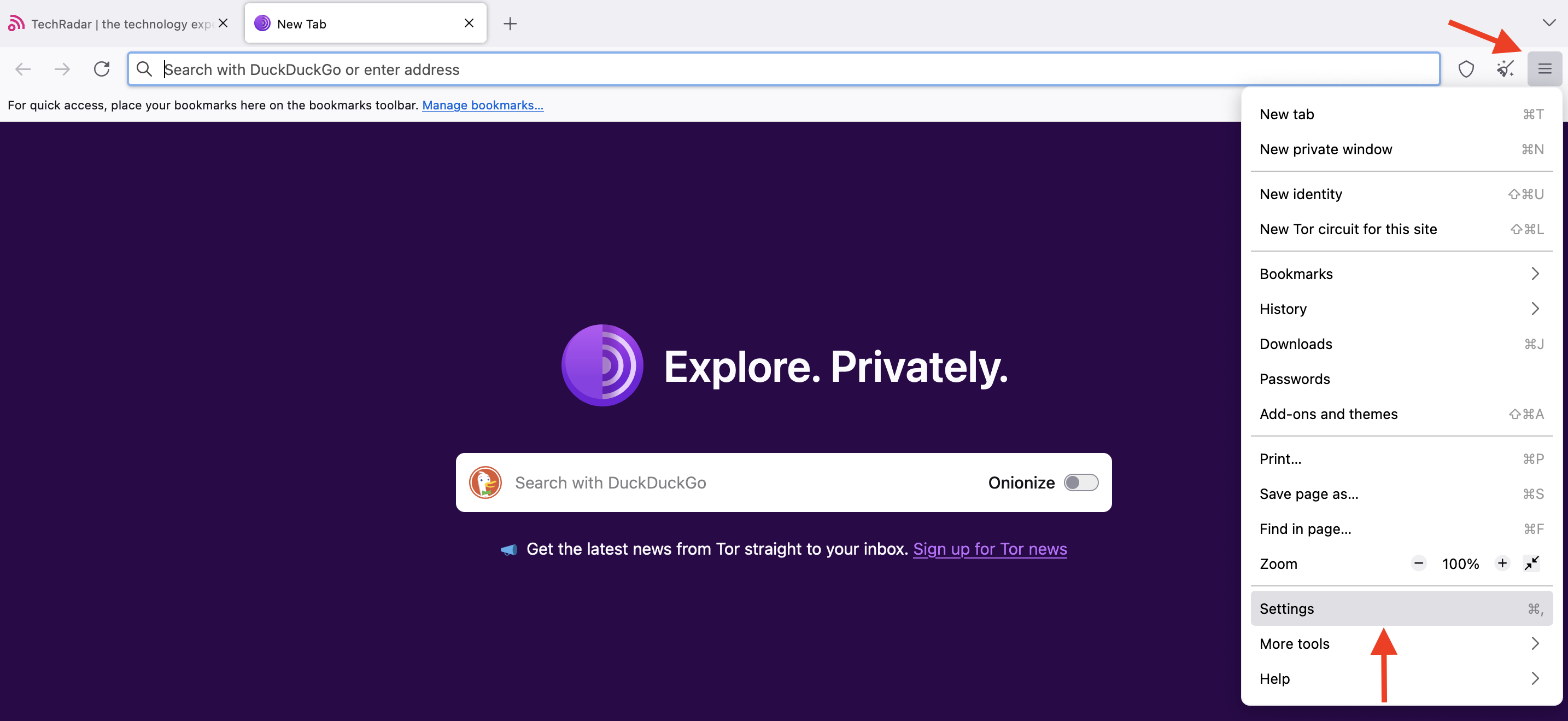
Next, click on the Privacy & security menu.
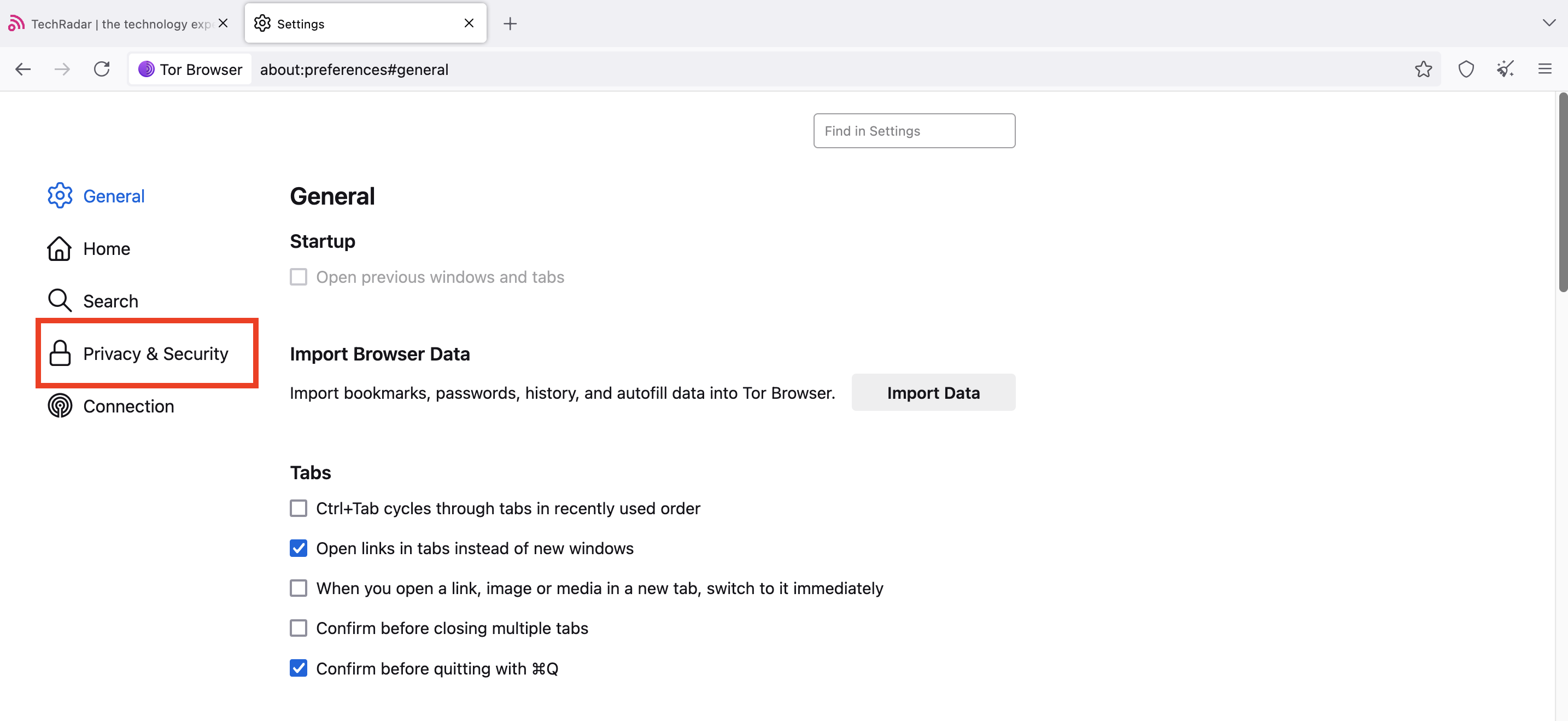
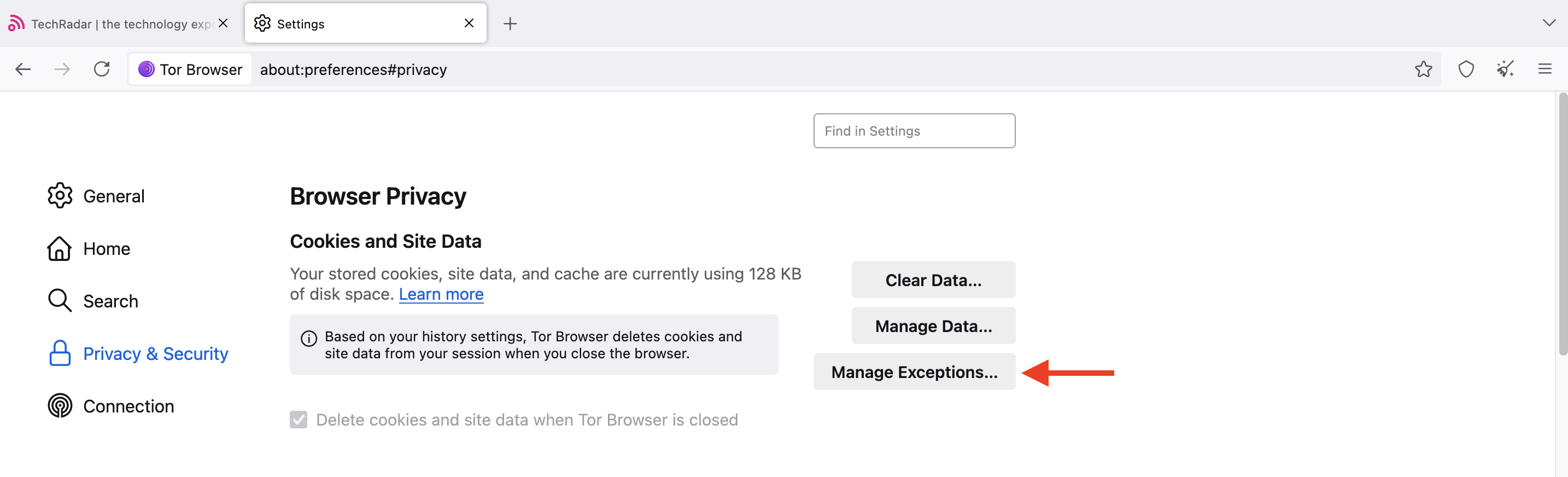
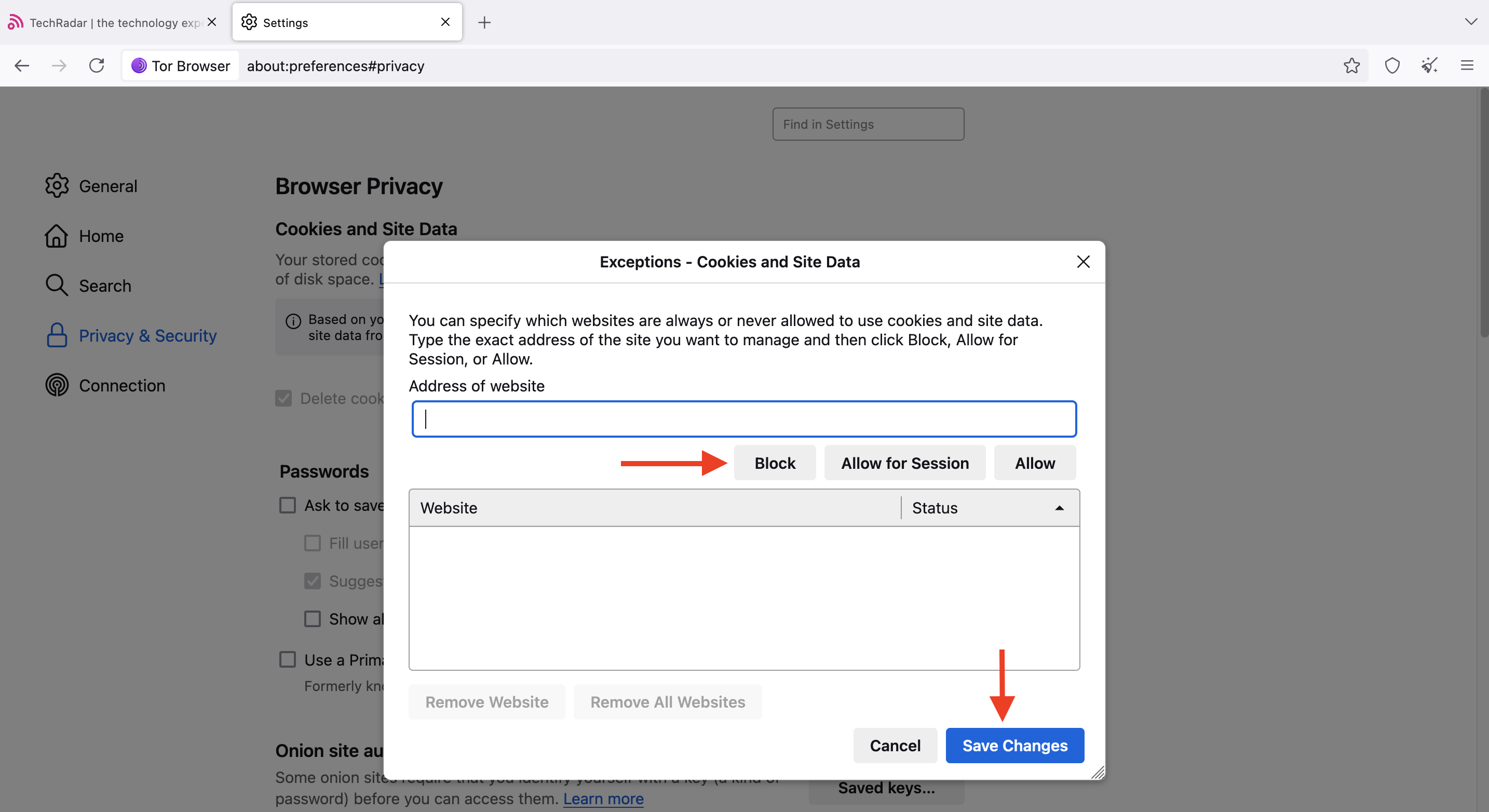
Under Privacy & security, select Manage Exceptions, then type the domain you want to block from installing cookies. Finally, click Block, then Save changes.
The above configurations help improve your security when surfing the web via Tor.
9. Access onion sites
We’ve demonstrated how to use Tor to access normal websites. However, the most secure way to use Tor is via .onion sites, which are built exclusively for the Tor network.
Onion sites are websites hidden inside the Tor network, and only the Tor browser can access them. Many popular websites, such as Facebook and DuckDuckGo, have Onion versions, so check if yours has one. If so, it’s better to use the onion address instead of the standard one.
Onion sites are hosted on the Tor network, enabling them to share information without revealing users' IP addresses. They facilitate secure communication over the web and protect from third-party surveillance. Regular browsers can’t open Onion sites because they aren’t part of the standard domain name system.
Onion sites end in “.onion” instead of “.com,” “.co,” “.net,” etc. For example, DuckDuckGo.com’s onion address is https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion/.
You can find other onion sites via dedicated directories. You can also use DuckDuckGo to find onion sites across the Tor network.
However, be cautious when exploring onion sites. Tor’s anonymity has spurred many malicious actors to host dangerous sites on the network, including scams, phishing links, malware, and illegal content.
Always verify a site's legitimacy before visiting – onion addresses are long, random strings, making it easier for malicious actors to create lookalike addresses for phishing. A little typo can lead you to a clone designed to trick users into handing over sensitive data.
Avoid downloading files or clicking suspicious links. Visiting or downloading illegal content can bring serious consequences, so avoid venturing into a rabbit hole on the Tor network.
Other built-in Tor features you should know
We’ve explained how Tor protects your privacy by routing traffic through multiple servers. You should also know other Tor features that keep you safe online, including:
No plugins or extensions
Tor doesn’t support external plugins and extensions, unlike standard browsers. It comes only with one pre-installed addon called NoScript. This addon allows you to control which sites can executive JavaScript and which ones can’t. Tor blocks JavaScript by default, but this addon lets you permit it for trusted sites.
Tor doesn’t support plugins because they introduce security risks. Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether.
HTTPS-only
Tor lets you turn on HTTPS-only to enhance security. This setting forces all website connections to use the secure HTTPS protocol rather than HTTP, an insecure version that leaves you vulnerable to eavesdropping.
To make things simpler, HTTP stands for Hyper Text Transfer Protocol, and this protocol governs communication on the world wide web. It's what enables web browsers and servers to share information, including web pages and media files.
Whenever you enter any domain into the address bar, your browser uses HTTP to find and request the data from the relevant server. However, HTTP on its own isn’t secure– it doesn’t encrypt data during transmission, which leaves an opening for third parties to spy on your online activities.
HTTPS is the secure version of HTTP. It encrypts data during transmission to avoid the risk of being eavesdropped. With HTTPS, only you and the website you’ve requested can see the information being exchanged on your browser.
Most websites have HTTP and HTTPS versions, but connecting to the former introduces a security vulnerability. With HTTPS-only enabled, Tor automatically upgrades all HTTP requests to HTTPS to prevent this vulnerability.
Tracker blocking
Websites often install trackers to monitor your activities, including those on other websites. Tor prevents this by isolating each website visit, meaning third-party trackers can't follow you around. For added security, cookies are automatically cleared each time you close Tor.
Should I use a VPN with Tor?
A common inquiry from Tor users is if they should use a VPN to add an extra layer of protection. The answer is nuanced.
On its own, Tor obscures your IP address by bouncing online requests through multiple servers, similar to how a VPN routes your traffic through an external server. Websites you visit via Tor will see the IP address of the exit node, not your actual IP, just like websites see the IP address of your remote server when using a VPN.
You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. You can also use it if you don’t want your network administrator or ISP to be aware of your Tor usage. However, if you don’t fall into these categories, or are a high-risk internet user (e.g., an investigative journalist or whistleblower), combining a VPN with Tor might be unnecessary.
A VPN app opens another potential vulnerability, as it can log the sites you visit via Tor. If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy.
Limitations of using Tor
Tor is a powerful tool that enhances your privacy. But, it’s not perfect. You should be aware of its limitations, including:
1. Slower browsing speeds
Tor is slower than standard browsers because it routes your traffic through multiple servers. This routing, through at least three nodes distributed worldwide, introduces latency, especially when there’s congestion on specific nodes.
The performance of entry, middle, and exit nodes can vary, and some are slower than others. Several seconds of delay, compared to using a standard browser, isn’t out of the ordinary on Tor.
2. Limited compatibility
As mentioned earlier, many websites consider Tor suspicious and block users entirely. Sometimes, you can access a website but won’t be able to login on your Tor browser. Likewise, some websites allow Tor, but with frequent Captchas that can be annoying.
3. Exit node vulnerabilities
The last node (exit node), through which Tor routes your traffic, is delicate. In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts.
Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic. Hence, it’s advisable not to download files via Tor, especially from unknown sources.
4. Attracts attention
Tor usage attracts attention in some countries. Some governments actively monitor or block Tor traffic, and Tor use can raise suspicion even when not used for illegal activities. Confirm local circumstances before accessing the web via Tor.
5. Vulnerability to advanced actors
Though secure against everyday threats, Tor is vulnerable to targeted attacks from state-level actors.
For example, state-level actors can execute traffic correlation attacks, wherein they monitor both incoming traffic at the entry nodes and outgoing traffic at the exit nodes. By observing these patterns, they can link a Tor user's request to a server and reveal their intended destination.
A traffic correlation attack takes serious resources, but it’s doable for advanced actors with sufficient motivation. Tor is not 100% secure, so be careful when using it.
6. No protection against malware
Tor doesn’t protect against potential malware infections. Downloading tainted files or clicking suspicious links can install malware on your device, so be cautious when surfing the web.
If any link looks weird, it likely is and may be a phishing link. Don’t open attachments from untrusted sources, as they are a common vector for spreading malware.
Additional security measures
Maintain digital hygiene
Practice safe, smart digital habits if you must use Tor to log into personal accounts. For instance, always use strong passwords that mix letters and symbols, making them hard to guess. Use different passwords for each account so that a single compromised account doesn’t affect others.
Enable two-factor authentication to avoid malicious actors accessing your accounts even if they get the correct username and password. Ensure your Tor browser is always up-to-date– automatic updates are enabled by default, but if turned off, you should manually update it regularly.
Use encrypted communication apps
Use encrypted communication platforms instead of the standard ones with less robust security features. For example, you can use Signal as your daily messaging app– it has end-to-end encryption and collects minimal data unlike many other messaging apps.
You can use a secure email platform like ProtonMail or Tuta. These secure communication platforms improve your security when using Tor.
- Here is how you can browse the web anonymously
Stefan has always been a lover of tech. He graduated with an MSc in geological engineering but soon discovered he had a knack for writing instead. So he decided to combine his newfound and life-long passions to become a technology writer. As a freelance content writer, Stefan can break down complex technological topics, making them easily digestible for the lay audience.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.