Free tools to protect your PC from attack
From a neighbour stealing your Wi-Fi bandwidth to a professional hacker using your hardware to attack a high-value target, hacking comes in many forms. We're going to look at common hacking scenarios and learn how to detect and deal with unauthorised activity.
The first reaction many people have to the possibility of their computer being hacked is one of disbelief. Who would bother, they ask, to hack a home server that's of limited interest to the world? In fact, it's this very obscurity that's so attractive to serious professional hackers.
They may not be interested in you as a target at all. Instead, your system is merely a stepping-stone towards launching an attack against a target of far higher value.
A large percentage of people who consider themselves hackers, however, are simply vandals. It's a sad fact of online life that some people actually believe they're teaching you a lesson in internet security by defacing your website, locking you out of your own accounts and otherwise creating unnecessary mayhem.
Activities that can be classed as hacking come in many forms. Your new neighbours might decide to hijack your insecure Wi-Fi network rather than pay to have their own broadband installed, for example. If you share a house with other people who you don't know that well, another member of the household could have installed snooping software to steal your identity.
In this tutorial, we're going to show you how to detect and recover from these and other common hacking incidents. First, let's take a look at a very useful system tool.
Examine your PC
Sign up for breaking news, reviews, opinion, top tech deals, and more.
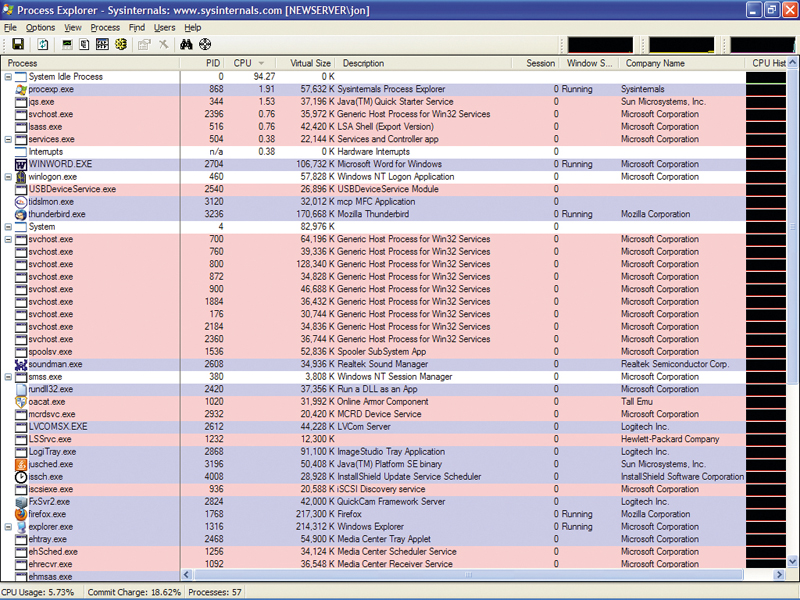
There's nothing worse than suspecting that something untoward is happening on your computer but not being able to investigate properly. If you don't already use it as a substitute for the standard Task Manager, download and install Process Explorer. This program is very useful when you need to know exactly and instantly what's running on your system.
Once you've downloaded it, unpack Process Explorer (procexp.exe) from the zip file and place it in a suitable directory. Run the program and you'll see lots of information about every process running on your machine. You can also make Process Explorer start up instead of Task Manager when you hit [Ctrl]+ [Alt]+[Delete]. To do so, simply select 'Replace Task Manager' in the Options menu.
If you click the CPU column in Process Explorer, it will sort the list of processes by the amount of CPU time they use. This is very useful when you suspect there may be a rogue process taking up too much CPU time and slowing down your system.
Clicking the Process column header a couple of times produces an indented list showing the parentage of all processes. Your applications and other desktop programs are all under the Explorer process, whereas all the system processes are children of the System process – which is a child of the System Idle process.
Process Explorer makes it easy to drill down into an individual process to see what it's doing. Pick an application and doubleclick it. A new window will open. On the Image tab, click 'Verify'. Each process has a signature that Process Explorer will verify by contacting the vendor's site. The 'Verify' button is a quick way of ensuring that an application hasn't been infected by malware.
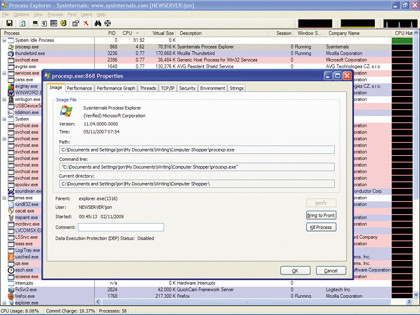
If there's a process you don't recognise, right-click on it and select 'Search Online...'. This opens a browser and searches the web for information about the process. If it's malicious, the results will soon tell you so.
Secure your Wi-Fi
Now let's examine a social problem that still catches out users of older Wi-Fi equipment. If your computer is switched off, yet the data lights on your Wi-Fi router are blinking away like mad, you should be suspicious.
If, in conjunction with this, you find that when you use the internet, your connection is slower than it used to be, you should assume the worst: someone in the vicinity is using your Wi-Fi connection.
Some people think it's OK to steal wireless bandwidth rather than buying their own. Some believe it's acceptable to do so for a few days while they wait for a provider to hook them up. The simplest way to lock out freeloaders is to access your Wi-Fi router's web interface and select 'WPA security'.
You'll have to consult the manual for your router to find out how to do this on your hardware. If your router and Wi-Fi network cards support WPA2 security, it's best to use this because it's stronger.
Some security consultants now also advise further deterring people looking to leech Wi-Fi by giving your network an unappealing name. Something like 'Unstable network' is good, but 'Infected network' may be a better option.