Watch out, iPhone owners: this dangerous phishing attack could lock you out of your Apple devices
Don’t be fooled
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
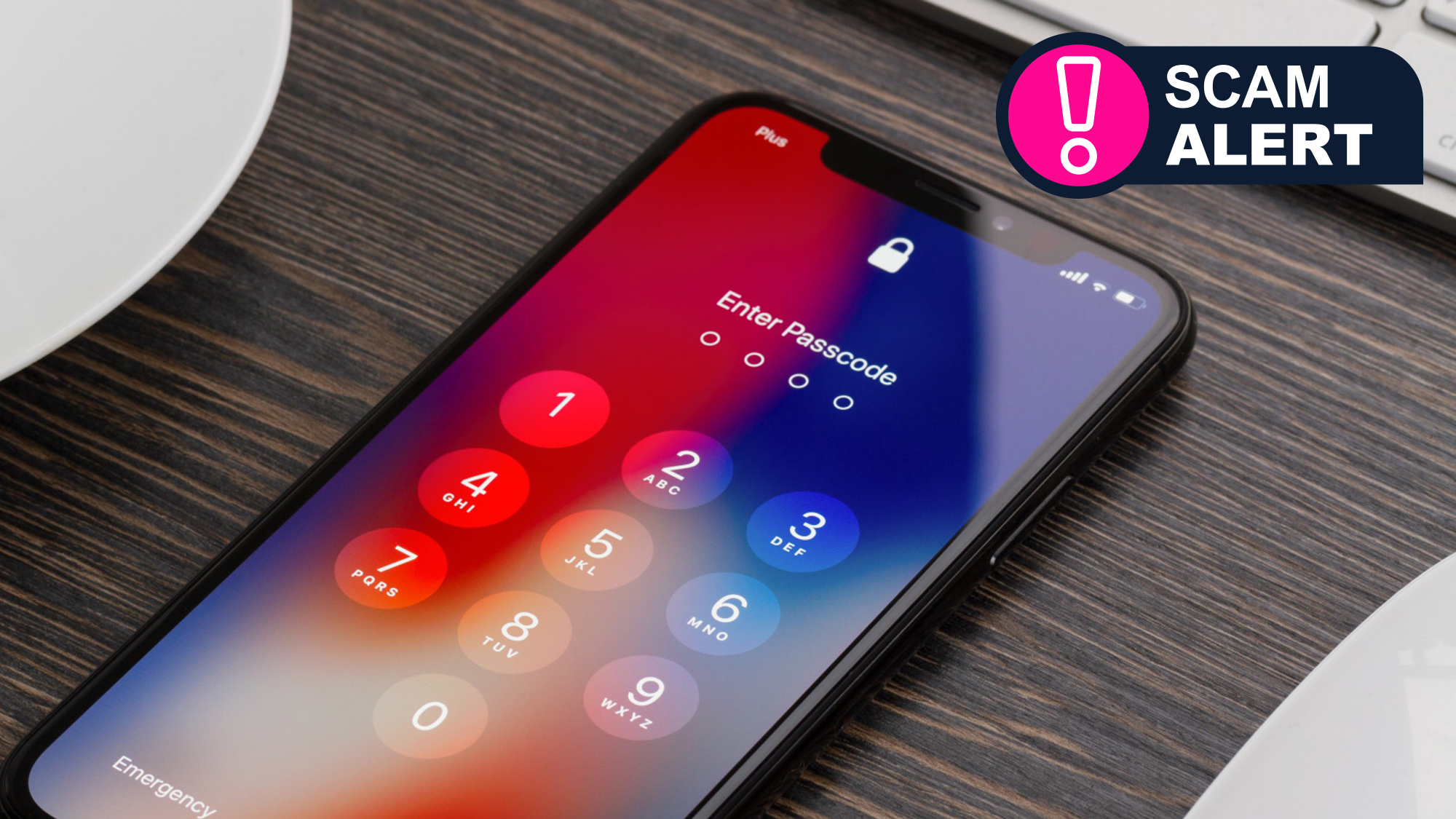
A new phishing attack has been targeting Apple users, bombarding them with notifications and attempting to trick them into allowing hackers access to their account. If the attackers get their way, you can be locked out of every single Apple device you own.
Documented by the Krebs on Security blog (via MacRumors), the exploit involves “MFA bombing,” or sending a constant stream of multi-factor authentication (MFA) requests to a user. These usually display the text “Use this iPhone to reset your Apple ID password,” with options for “Don’t Allow” and “Allow.”
If you select Allow, the hacker is able to change your Apple ID password and lock you out of your own account. Because this method affects your Apple ID (rather than, say, your Lock Screen passcode), it can be used to take over all of your Apple devices that use that same ID.
That makes it a particularly powerful attack. But if you experience it, it’s unlikely you’ll just see one pop-up – the bad actors seem to be exploiting a bug that displays the request over and over again, with a new one appearing each time you select Don’t Allow.
According to Parth Patel on X (formerly Twitter), you might have to dismiss over 100 messages, with the attackers apparently hoping that you’ll slip up or get tired and mistakenly choose Allow.
A professional and sophisticated attack

And it doesn’t stop there. If you get through all of that and the phishers still have not been able to take over your account, they apparently call you while pretending to be Apple.
Patel detailed how the impersonators spoofed the official Apple number and asked him for a one-time password (OTP) that had just been texted to him. Handing this over would have been an error as it would have given them another way into Patel’s account, and the text accompanying the OTP explicitly stated it should not be shared with anyone.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Fortunately, Patel did not hand it over. He asked the caller “to validate a ton of information” about himself, much of which they got correct – yet they managed to get his first name wrong. It turns out that they were using a leaked database of personal information from People Data Labs that had incorrectly logged his data.
Krebs on Security determined that the attackers are likely using a page on Apple’s website for users who have forgotten their Apple ID password. This page lets you enter an Apple ID or phone number, pass a CAPTCHA check and send a reset request to the account. It’s not known how the phishers are getting the system to send multiple requests, but it’s likely to be a bug that they are exploiting.
This professional and sophisticated attack shows the lengths some hackers are going to in order to take over targeted Apple accounts, and it is clearly not the work of amateurs. If you get bombarded with password reset requests, make sure you always select Don’t Allow (no matter how many pop-ups appear) and always refuse to hand over OTP details, even if the request appears to be official.
Apple will never ask for these details (and nor will any other reputable company). It’s your device account that’s on the line, and you need to protect it at all costs.
You might also like

Alex Blake has been fooling around with computers since the early 1990s, and since that time he's learned a thing or two about tech. No more than two things, though. That's all his brain can hold. As well as TechRadar, Alex writes for iMore, Digital Trends and Creative Bloq, among others. He was previously commissioning editor at MacFormat magazine. That means he mostly covers the world of Apple and its latest products, but also Windows, computer peripherals, mobile apps, and much more beyond. When not writing, you can find him hiking the English countryside and gaming on his PC.