Access management systems: what you need to know
Why price tags and marketing shouldn't impact your decision
Whether spending on a completely new or upgraded system, access authentication system costs are brutal. Despite the amped up "sophisticated" security and clock-in systems enterprises currently spend too much money on, many organizations remain vulnerable to security threats, including human error and hackers.
In addition to the intrinsic vulnerabilities of most technologies, potential integration compatibility issues between new and pre-existing in-house technologies and software programs may arise. Worst-case scenario: Some authentication access systems may malfunction or "cloud-over" and cease functioning when the weather turns.
Needless to say, there is a high demand from for access authentication systems that offer more for less without all the technological baggage and financial drain of typical systems. As a result, measuring the qualitative user friendliness and the compatibility capabilities of an access authentication system are essential to quantifying its purchase.
Let me hand you a bandage while I explain.
Enterprises have a hard time finding transparent authentication access products that deliver practicality. Most vendors sell the intelligence and capabilities of their system. However, the most common issues tend to be the lack of know-how and understanding of product functionality by an organization's employees. To aid employee learning curves, training sessions should be included in a bundle product price package. But training hours are also costly, as they take time away from employee productivity.
I've studied biometrics systems. I've compared access authorization devices that safely store and memorize employee and restricted information. The ridiculous price tag on these systems is incredibly frustrating. The reason these systems are priced so high is that intelligent competitors don't exist, and also because enterprises are easily swayed by intelligent marketing.
According to a 2010 report from the National Research Council, certain biological features are easy to copy. In other words, biometrics systems are not fundamentally valuable investments for enterprises. Consequently, these vulnerabilities opened a floodgate of experimental possibilities for the tech sector to tackle and improve.
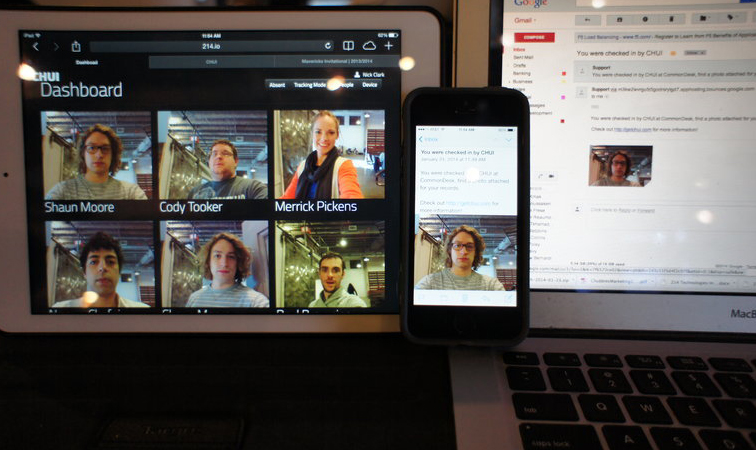
One increasingly popular experiment techies are working on integrating into authentication access systems is intelligent facial recognition capabilities with supportive external encryptions. Simply put, the idea makes sense because a person's face is unique and hard to copy. Since enterprises have already upgraded their cost-effective analyses to include user-friendliness, facial recognition devices should ultimately trump biometrics systems as the leading authentication access platform.
Sign up for breaking news, reviews, opinion, top tech deals, and more.