How to use iCloud Keychain
Safer sign ins
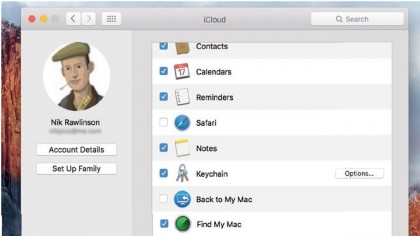
Using iCloud Keychain
Passwords, bank card numbers, email account settings… living in the modern world requires us to memorise more obscure information than ever before. No wonder so many of us pick a single, easy-to-remember password and use it across every service, from webmail to stores to online banks.
While that might make life easier for us, it certainly doesn't make it secure, as a breach of any one of those systems leaves every site you ever sign in to – as well as your Mac – potentially vulnerable.
Fortunately, iCloud Keychain can help. This feature, which is built in to OS X and iOS, syncs your account credentials between each of your Apple devices, so you can set obscure, less memorable passwords that are unique to every website you use, and then forget about having to remember them yourself.
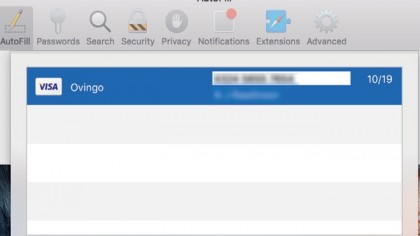
Safari is even able to fill in the details on your behalf. iCloud Keychain can even store your bank card details and the credentials for your email accounts and Wi-Fi networks, making those available on all your devices, too. Turning it on automatically moves details you've already saved to your Mac or iOS device to iCloud, and any new additions or amendments you make are added to the online keychain over time.
All in sync
Your details are encrypted before being passed through Apple's data centre on their journey between your devices, so even if they're intercepted in transit they should be uncrackable. How can we be so sure?
Because Apple's opted for the strongest variant of the same cypher used by the US government for secure communications (called 256-bit AES encryption), and further scrambles the data in transit using a complex piece of algebra, based not on numbers but on imaginary points located on a theoretical shape – an elliptic curve – drawn within an infinite space!
As a final level of protection, iCloud only shares your synced keychain with Apple devices that you've explicitly authorised to access the keychain's contents – so-called trusted devices – and it doesn't store the security code from the back of your bank card, effectively building in a firebreak against anyone making unauthorised purchases.
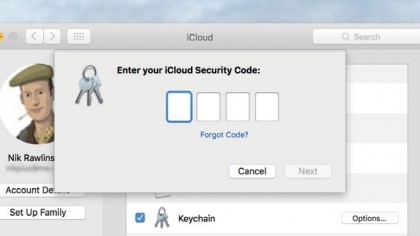
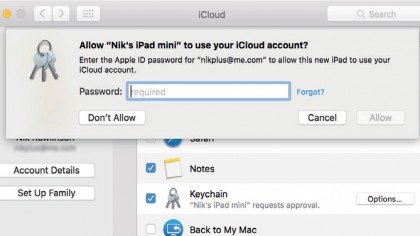
Once you've set up iCloud Keychain, you can largely forget about it, provided you keep three essential elements secure: your password, your trusted devices, and the Recovery Key for your iCloud account.
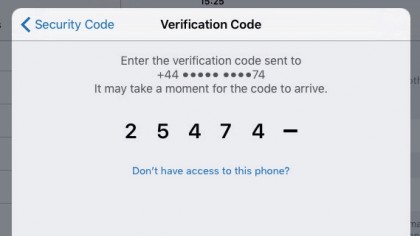
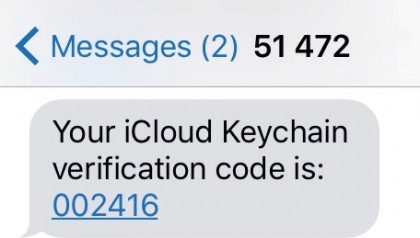
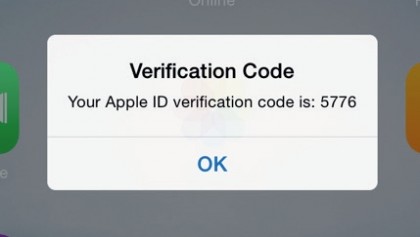
The latter of these is used to reset your account's password if you forget it after setting up two-step verification, in which Apple will send a passcode to your iPhone that you'll need to enter at the Apple ID website to prove that you have that particular trusted device.
Losing any two of these three parts of the system at once will lock you out of your account – perhaps permanently! If you can't memorise your password and Recovery Key, consider storing them in a fireproof safe along with any important legal documents, passports and so on, that you need to protect.
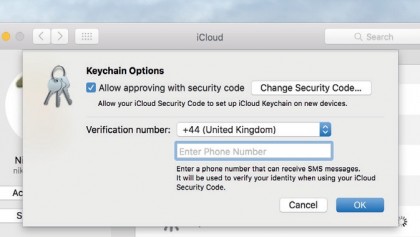
9. Remove your Keychain
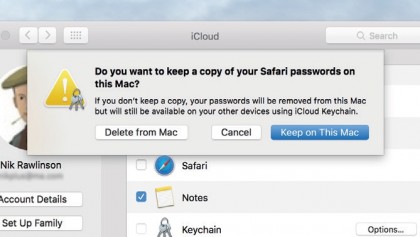
To clear your keychain data from iCloud, go to System Preferences' iCloud pane, click Options next to Keychain, then clear the box next to 'Allow approving with security code'.
Finally, on each of your devices, turn off iCloud Keychain.
- Enjoyed this article? Get more tutorials, guides, and tips on how to get the most from your Apple devices inside MacFormat. Take advantage of an exclusive offer in our sampler today.
Nik is an Esperanto-speaking, pencil-bothering, manual typewriter fan who also happens to have a soft spot for tech after sufficient years in the business to know what that disk icon on the save button actually means. Never happier than when out in his campervan, coffee in one hand, ebook in the other, listening to the rain on the roof.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful