Apple two-step verification uncovers dicey password reset flaw
Apple says it knows about the issue and is working on a fix
Update: Apple said that it's working to correct the Apple ID password reset exploit that was discovered earlier today and forced the company to suspend its iForgot tool.
"Apple takes customer privacy very seriously," the company told The Verge. "We are aware of this issue, and working on a fix."
No timeframe for when Apple will restore the ability to reset account passwords was attached to the succinct statement.
Original story continues...
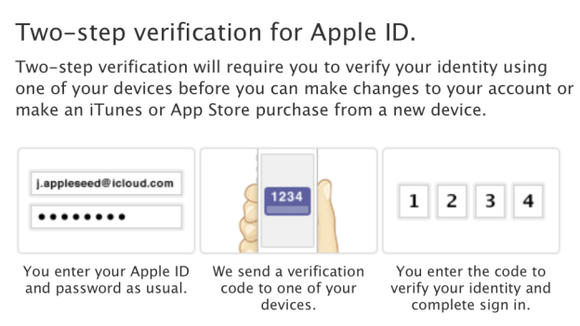
Apple's new two-step verification measure is more like one step forward, two steps back, as an exploit has been uncovered for people who haven't signed up for the new feature.
The only information required to reset a person's password is the email account associated with their Apple ID and their date of birth.
The password reset also requires pasting a modified URL into the address bar, according to The Verge, but this is a simple trick to figure out.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
This relatively easy password reset method works whether someone has unauthorized access to Apple ID email account or not, and would allow them to hijack your Apple ID, iTunes or iCloud accounts.
Apple password reset page down
Apple's two-step verification method incorporates a pin that's sent to a "trusted device" like an iPhone using the Find My iPhone app or another device using an SMS text message.
Upgrading to this extra layer of security, required for account changes and making purchases from a new Apple device, is one way to avoid having your Apple account hacked.
However, it's not that straightforward, as there's a mandatory three-day waiting period before the new two-step verification feature is enabled on an account.
In response to this, Apple took down its iForgot password reset page, while some users have gone to lengths such as randomly picking a new birth date.
Obviously, none of these are acceptable measures going forward. TechRadar has asked to Apple for a comment about the security flaw and will update this story when the company responds.
