How to secure your Linux system
Out of the box, a Linux installation is much more secure than other operating systems. That is, until you connect to the internet. Once online, a desktop Linux installation, in its bid to be of use to as many users as possible, leaves enough room to be exposed to attacks and intrusions. Don't sweat though. Help is only a terminal away.
All Linux distros ship with Iptables, which is a part of the kernel that enables sysadmins to filter network packets. Configuring it manually is impossible for all but the elite, but in the true spirit of open source the community offers a number of graphical front-ends that make setting up a firewall a walk in the park. One such graphical firewall is Firestarter.
We didn't start the fire
Firestarter simplifies the process of configuring the settings for a firewall. It can limit access on ports that are running services that might be prone to outside attacks, and you can also use it to glance at the network traffic passing across the machine you're running it on.
Most distros bundle Firestarter in their repos, so installing it shouldn't be a problem. When you start it for the first time, the firewall launches a simple configuration wizard that prompts you to select the network interface on which it will be active.
If you have multiple devices with one connecting to the internal network, Firestarter can act as gateway and share the internet connection with the rest of the network. By default, Firestarter only filters through connections that are in response to connection requests from the firewall host. The advantage of doing things this way is that it blocks access to services like Telnet, which can be exploited to gain access to your machine without your knowledge.
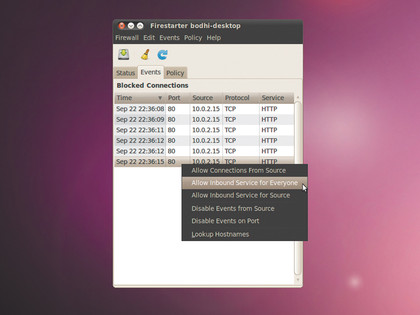
Tweaking the firewall doesn't take much effort either. If you have an app that requires access on certain ports, such as a Torrent client, you need to punch holes in your firewall to allow incoming connections. That's easily done from under the Policy tab.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Right-click inside the space under Allow Service and select Add Rule. From the pull-down menu, select the service you want to allow, say Samba, select the source IP (anyone opens the port to all) and you're done.
To restrict outgoing traffic, select Outbound Traffic Policy from the drop-down list. Now you can select either the Permissive or the Restrictive option. If you select the Permissive option, you'll have to add the hosts you want to block in a blacklist. Restrictive is the opposite, and only allows connections from the listed hosts, denying the rest.
When running in restrictive mode, Firestarter will log all connection refusals under the Events tab. As you spot a connection you want to allow for your users, right-click on the entry and select the option to either allow the connection for everyone or just when it originates from a particular source.
You can also monitor active connections to the firewall from Firestarter's main interface. It shows you the status of the service, gives you a summary of inbound and outbound connections, and the amount of data that has passed through an interface. In addition to listing the source and destination of the traffic, it'll also tell you the port the data is travelling through, the service running on that port and the program that's calling the shots.
Encrypt your filesystem
If you really want to keep others from reading your files, user passwords won't cut it. For instance, there's very little to stop a user with higher access permissions, like the root user, from gawking at stuff under your home directory. What you need is to encrypt your data so that it's unintelligible to people without the means to decrypt it.
The smart way to do this is to encrypt the whole filesystem, which would automatically encrypt any data kept on it. This is where TrueCrypt shines.
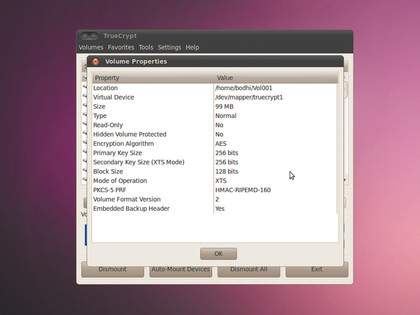
It lets you carve a virtual slice out of your Linux partition that will act as a standalone encrypted filesystem. You then mount it, use it to store and read files as you would from a normal partition, then unmount it, and Bob's your uncle. When it isn't mounted, the encrypted filesystem appears to be a random jumble of bits.
TrueCrypt isn't available in any distribution's repository due to licensing issues, but installing it is a trivial affair. Grab it from its website, extract the Tar archive, and install it via the graphical setup. Just make sure your distro has the Fuse library, and the device mapper tools.
Create an encrypted volume
Before you can use TrueCrypt you'll have to create an encrypted volume to store files on, so launch the app and click on the Create Volume button. This will launch the Volume Creation Wizard, which lets you either create a virtual encrypted disk within a file or an encrypted volume within an entire partition, or even a disk such as a removable USB drive.
If you select the first option to create a virtual disk, TrueCrypt will ask you to point it to a file on the disk that'll be the encrypted volume. If the file exists, TrueCrypt will recreate it, using one of the eight encryption algorithms.
Next, specify the size of the encrypted volume and format it as an FAT filesystem, which makes it accessible from other operating systems as well as Linux. Finally, choose a password to mount the encrypted volume.
To store files on the volume you'll have to mount it. Select the file that's your encrypted volume from the TrueCrypt main interface, and press the Mount button. The app will prompt for the password of the volume before it can be mounted. You also get the option to mount the volume as read-only, if all you have to do is read files from it.
By default, TrueCrypt chooses not to remember the name of the file that's your encrypted volume. This is a security feature, and adds another roadblock in the path of an intruder. If you ask the app to remember the name of the file, anyone with physical access to the computer can select the file from a pull-down menu and mount the encrypted volume. They'll still have to get past your password though.
Once the encrypted volume is mounted you can save files to it just like you do with a normal volume. TrueCrypt uses your modern hardware at its disposal to encrypt and decrypt files on the fly; which is to say it minimises the lag due to the overhead of converting unreadable bitstream into meaningful data that can be read by your text editor or played by your media player.
When you're through, unmount the volume with the Dismount button within the program.
Current page: Software firewalls and encryption
Prev Page Linux security basics Next Page Securely delete files and browse anonymously
With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.