How Linux can help you protect your privacy online
The Web is the greatest system for sharing information but how do you stop it sharing too much?
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Using SSL will keep your data safe from eavesdroppers, but what if the companies that you're communicating with are spying on you?
Google, Facebook, Twitter and others have built business models out of providing users with a free service in return for information about you. This information can then be used to target advertisements at you.
Twitter has even gone a step further and sold users' tweets to market researchers. Some people may consider this a fair trade, but privacy campaigners are becoming increasingly concerned about the shear quantity of data these companies are holding about us. And this data goes way beyond what we voluntarily hand over to them.
Both Google and Facebook have established relationships with literally millions of other websites to help them track your movements around the web using cookies. These may sound like tasty treats, but are actually pieces of information stored on your computer to help sites identify you when your browser reaches them.
To find out just how much these companies are tracking us, we can use Wireshark to monitor our network connection and watch for the cookie data being sent back.
Start Wireshark and capture on your main network interface. In the filter box enter http.cookie
This will now show only packets that relate to cookies that are being sent to web servers. To display a little more of the information that is being acquired, go to the middle pane and click on the arrow next to Hypertext Transfer Protocol.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
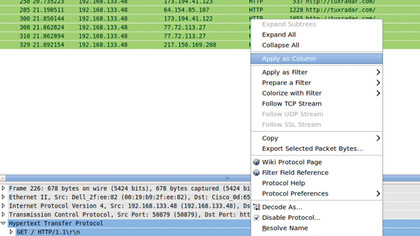
There are two sections in here that allow the web company to track us: the host and the referrer. Right-click on each of these and select Apply As Column. This will then add these fields to the main view.
Each of these two domains allows the host (the organisation receiving the cookie) to monitor your activity on the referrer. In addition to this, the host uses a unique ID to track your activity between sessions. Google uses its advertising services to monitor what we do, whereas Facebook uses its Like buttons.
There's no way of knowing exactly what these companies are doing with the data they collect - we can see only what they're receiving.
Fortunately, most browsers allow you to control cookies. Depending on your personal feelings, you may choose to limit cookies to certain websites (where they can be useful to remember preferences), or block them completely.
If you use Firefox, go to Edit > Preferences > Privacy, and change Firefox Will to Use Custom Settings for History. If you untick Accept Cookies From Sites, Firefox will not store any cookies.
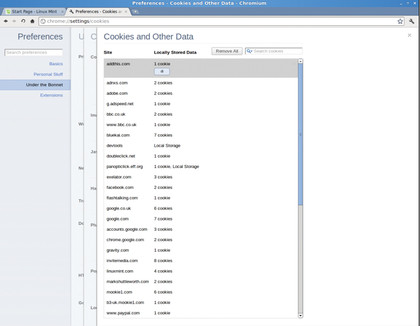
To do the same in Chromium go to Preferences (the spanner by the address bar) > Under the Bonnet and change Cookies to Block Sites From Setting Any Data. In Konqueror, this can be done through Settings > Configure Konqueror > Cookies and unchecking Enable Cookies. For lightweight KDE users, it can be done in Rekonq by going to Settings (the spanner by the address bar) > Network > Cookies and unchecking Enable Cookies.
As well as allowing you to completely block cookies, both Firefox and Chromium give you the option of blocking third-party cookies (In Konqueror and Rekonq, this is Only Accept Cookies From Originating Server). This means they block cookies from domains other than that of the current website. If you do this, websites can store data about you, such as your preferences, and can track your movements within the site, but other sites won't be able to follow your movements once you leave the domain. This will stop companies from tracking your movements across the web.
If you set this up, then run cookie tracking in Wireshark, as was done above, you will see that the referrer and the host are always the same domain. For many users, this will be a happy medium of letting cookies do their original purpose - letting sites use them to recognise returning viewers - but blocking organisations from following their online movements.
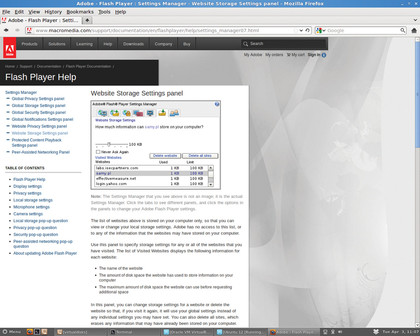
Cookies aren't the only way that websites can track you. Even if you have browser cookies disabled, sites can still store tracking information on your computer using Locally Shared Objects (LSOs). These function exactly like cookies, except that they're accessed through Flash rather than directly through your browser.
To view and control what websites are using these, go to Macromedia's Website Storage Settings Panel.
Webmasters intent on tracking you can use a combination of techniques to create zombie cookies. These store the same information in more than one place so that when you destroy one, they regenerate using the others. For example, if you delete all browser cookies, the website can recreate the cookie from an LSO, and visa versa. As long as one of these remains, all the others can regenerate.
Samy Kamkar has taken this to the extreme at samy.pl/evercookie, where he uses 12 different methods to resurrect the data! We think running the NoScript extension for Firefox should prevent this type of cookie from working, but it also disables the method of testing it! We found that neither Private mode in Firefox, nor Incognito mode in Chromium were able to prevent this.
If you need to be sure that your web browsing isn't being tracked across sessions, the best solution is to use a non-persistent system. That is, a system that doesn't carry any information over from one session to the next. You can still be tracked during a browsing session, but not between them.
For Linux users, the most obvious option is a live DVD. This doesn't have to be a physical disc running live - an ISO running in a virtual machine will do the job. This means that all data that the websites can use to track you is reset each time you restart the virtual machine. You can also run more than one virtual machine simultaneously to prevent anyone linking two sessions.
If it ever comes into being, a live version of Boot To Gecko would be a particularly convenient way to do this, but this is still in development.
Current page: How to stop companies tracking you
Prev Page How to use Wireshark Next Page Beating digital fingerprinting