How to use a Raspberry Pi to browse anonymously
Use Tor and a Raspberry Pi to access the internet anonymously from all your devices
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Do you use Tor to prevent Big Brother from tracking you online? Although it is pretty straightforward to use, it can be quite a hassle to configure Tor on all your Internet-enabled devices.
You can save yourself a lot of hassle by using a Raspberry Pi as an anonymous wireless access point. The Pi will dole out an IP address, and any device that's connected to it will be able to access the Internet via the Tor network.
To get this project up and running, you'll need the following:
- A Raspberry Pi along with an SD card with the Raspbian distro. If you haven't done this before, follow our walkthrough to get Raspbian up and running.
- You'll also need an Ethernet cable. Hook one end into the Pi's Ethernet port and the other into your wireless router. This is how the Pi will connect to the Internet.
- You'll also need a USB Wi-Fi adaptor that's compatible with the Raspberry Pi. If you haven't got one yet, check the list of compatible adapters that are known to work on the Pi.
Access Point Pi
Once you've set up the Pi, you can configure it from a remote machine via SSH. For the rest of the tutorial, we'll assume the IP address of your Pi is 192.168.2.100. Fire up a terminal that's connected to the same router as the Pi and enter
ssh pi@192.168.2.100
to connect to it. After authenticating yourself into the Pi, use iwconfig to make sure the wireless adaptor is recognised by the device. Now refresh its package list with
sudo apt-get update
Sign up for breaking news, reviews, opinion, top tech deals, and more.
and install the software that will make it act as an access point with:
sudo apt-get install hostapd isc-dhcp-server
When it's installed, it's time to set it up. Begin by editing the /etc/dhcp/dhcpd.conf file that controls the DHCP and automatically assigns IP addresses to all connected devices. Open it in the nano text editor with
sudo nano /etc/dhcp/dhcpd.conf
and comment out the following two lines by adding a # in front of them, so that they read:
#option domain-name "example.org";
#option domain-name-servers ns1.example.org, ns2.example.org;
In the same file, scroll down and uncomment the word authoritative; by removing the # in front.
Then scroll down to the end of the file and add the following lines:
subnet 192.168.12.0 netmask 255.255.255.0 {
range 192.168.12.5 192.168.12.50;
option broadcast-address 192.168.12.255;
option routers 192.168.12.1;
default-lease-time 600;
max-lease-time 7200;
option domain-name "local";
option domain-name-servers 8.8.8.8, 8.8.4.4;
}
In these lines we define the IP address of our Pi access point (192.168.12.1), the range of the IP addresses it'll hand out to connected devices (from 192.168.12.5 to 192.168.12.50) as well as the address of the domain name servers (8.8.8.8 and 8.8.4.4). You can change any of these values as per your preference. Save the file (Ctrl+X) once you're done.
Setting up a static IP
We'll now edit the /etc/default/isc-dhcp-server to specify the interfaces that our new DHCP server should listen to. Open the file and scroll down to the line that reads INTERFACES="". Insert wlan0 between the quotes so that it now reads INTERFACES="wlan0", and save the file.
Now we'll set up the wireless adaptor (wlan0) and give it a static IP address. First, deactivate the wireless adaptor with the command sudo ifdown wlan0 and then open the /etc/network/interfaces file. In the file, add # to comment out every existing entry associated with wlan0, such as:
# iface wlan0 inet manual
# wpa-roam /etc/wpa_supplicant/wpa_supplicant.conf
# iface default inet dhcp
Then add the following lines below the line that reads allow-hotplug wlan0 to set the static IP address for the new access point:
iface wlan0 inet static
address 192.168.12.1
netmask 255.255.255.0
Save the file and activate the interface with
sudo ifconfig wlan0 192.168.12.1
Make your point
Now that we've defined the wireless access point, it's time to configure it. Create a new file called /etc/hostapd/hostapd.conf with the following contents:
interface=wlan0
ssid=TorSpot
hw_mode=g
channel=6
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
wpa=2
wpa_passphrase=$Your_Passphrase$
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP
rsn_pairwise=CCMP
We've set up a password-protected network called TorSpot. You can specify a different name for the access point by specifying it in the ssid= string. Also change the wpa_passphrase= string to specify a custom password. You'll need to enter this password to authenticate yourself to the Pi's access point.
Next up, we'll tell the Pi where to find this configuration file by pointing to it in the /etc/default/hostapd file. Open the file, find the commented-out line that reads #DAEMON_CONF="" and uncomment and edit it to read DAEMON_CONF="/etc/hostapd/hostapd.conf".
NAT setup
We now need to set up NAT to allow multiple clients to connect to the Pi's access point and route all their traffic through the single Ethernet IP. Edit the /etc/sysctl.conf file and at the bottom add the following line:
net.ipv4.ip_forward=1
Save the file and then enter
sudo sh -c "echo 1 > /proc/sys/net/ipv4/ip_forward"
to activate the forwarding. You'll now have to specify the routing rules that will connect the Ethernet port (eth0) that's connected to the internet and the Wi-Fi access point (wlan0) which is exposed to the devices within your network:
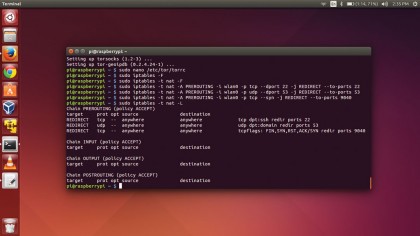
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
sudo iptables -A FORWARD -i eth0 -o wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo iptables -A FORWARD -i wlan0 -o eth0 -j ACCEPT
By default, these rules will be flushed when you restart the Pi. To make them permanent, first run:
sudo sh -c "iptables-save > /etc/iptables.ipv4.nat"
Then edit the /etc/network/interfaces file, scroll down to the very end and add
up iptables-restore < /etc/iptables.ipv4.nat
What this does is loads the rules when the devices are activated on boot.
Your Pi access point is now all set. To test it, restart the DHCP server with
sudo service isc-dhcp-server restart
and manually enable the access point with our configuration with the following command:
sudo /usr/sbin/hostapd /etc/hostapd/hostapd.conf
If you get an 'unknown driver' error, read our section on 'Your own hostapd'. If everything goes well, the wireless access point (TorSpot) is listed in the list of available Wi-Fi hotspots.
You can connect to it from another computer or a smartphone and authenticate using the password you specified in the hostapd.conf file. When connected, you should be able to browse the Internet normally.
Once you have tested the new access point, let's cement the settings so that they are activated as soon as the Pi boots up. Start the hostapd and DHCP services with the following commands:
sudo service hostapd start
sudo service isc-dhcp-server start
Now update the init scripts with:
sudo update-rc.d hostapd enable
sudo update-rc.d isc-dhcp-server enable
Now restart the Raspberry Pi with the following command:
sudo shutdown -r now
When the Raspberry Pi is back up again, you'll be able to connect to the new access point and browse normally.
Torify access
Your Raspberry Pi is now fully functional as a wireless hotspot. However, the data is still not anonymised. So let's add Tor to the mix. SSH back into the Pi and install Tor with:
sudo apt-get install tor
When it's installed, edit Tor's config file /etc/tor/torrc and add the following at the top:
Log notice file /var/log/tor/notices.log
VirtualAddrNetwork 10.192.0.0/10
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
TransPort 9040
TransListenAddress 192.168.12.1
DNSPort 53
DNSListenAddress 192.168.12.1
These settings inform Tor about the IP address of our access point and ask it to anonymise any traffic that flows over it.
Next up, we'll change the routing tables so that connections via the Wi-Fi adaptor (wlan0) are routed through Tor. First, flush the existing redirection and NAT rules with the following commands:
sudo iptables -F
sudo iptables -t nat -F
Since we'll still want to be able to SSH into the Pi, we'll add an exception for SSH's Port 22 with:
sudo iptables -t nat -A PREROUTING -i wlan0 -p tcp --dport 22 -j REDIRECT --to-ports 22
We'll now add two rules. The first is a passthrough rule for DNS lookups and the second directs all TCP traffic to Tor's port 9040:
sudo iptables -t nat -A PREROUTING -i wlan0 -p udp --dport 53 -j REDIRECT --to-ports 53
sudo iptables -t nat -A PREROUTING -i wlan0 -p tcp --syn -j REDIRECT --to-ports 9040
As before, these rules will not be carried on to the next session. To load them on reboot, all you have to do is save them to the NAT save file as before with the following:
sudo sh -c "iptables-save > /etc/iptables.ipv4.nat"
In the previous section, we've already configured the /etc/network/interfaces file to load the contents of this file when the interfaces are activated.
You can now enable the Tor service with
sudo service tor start
and update the relevant boot scripts with
sudo update-rc.d tor enable
That's it. Now restart the Pi. When it's back up again, you'll be able to connect to the Pi hotspot, TorSpot, as before. However, unlike as before, all your traffic will now be routed through the anonymous Tor network.
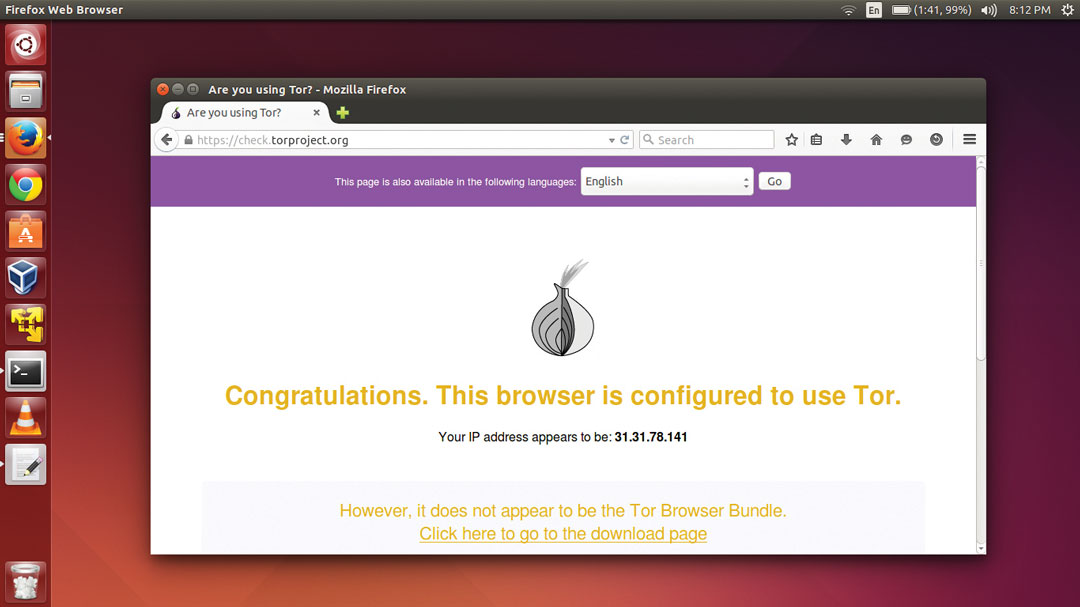
You can verify that this is happening by heading to check https://torproject.org from any device that's connected to TorSpot. The page will also list your IP address, which will not be that of your ISP. Visit this page from another device connected to TorSpot and it'll show a different address. Congratulations, you can now anonymously browse the web on all your devices!
QUICK TIPS
- If you get Locale errors when connected to the Pi remotely, make sure you don't forward your locale by editing /etc/ssh/ssh_config and commenting out the SendEnv LANG LC_* line.
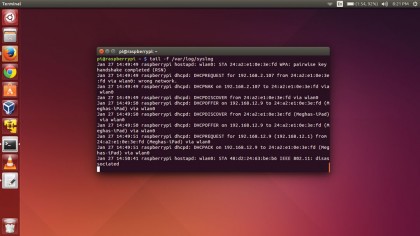
- Use the tail -f /var/log/syslog command to keep an eye on all system messages. This might come handy if you are unable to connect to the Pi hotspot.
- We've used Google's DNS service in this tutorial, but you can use another service like OpenDNS or your ISP's DNS servers by pointing to them in the /etc/dhcp/dhcpd.conf file.