Is your Windows VPN connection as secure as you think?
Here's how to find out...

Operating a VPN generally looks very easy: just choose a location, click Connect, then Disconnect when you're done. But there's a lot of hard work going on under the hood.
Top of the list is how the app creates its connection to the server. You hope it does this in the most secure way, right? But this doesn't always happen, and the worst offenders make horrible mistakes - especially with standard Windows VPN protocols (IKEv2, L2TP, PPTP, SSTP.)
Connections theoretically allowed with zero encryption, for instance, leaving you entirely protected? Yes, we've seen that several times!
If you only ever connect only via other protocols (OpenVPN, WireGuard, NordLynx, Lightway), then relax, we're not talking about those this time.
But if your app uses these Windows protocols, or you might use them in future, it's worth taking a couple of minutes to check out the relevant settings.
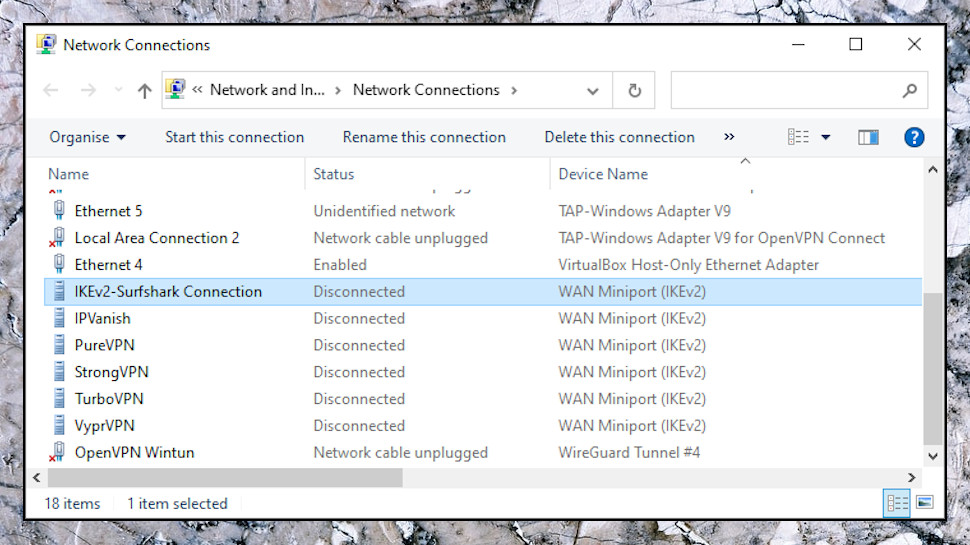
Find your VPN connection
When you need to know more about your Windows VPN setup, the Network Connections window is the place to be. Type network connections in the Search box and click View Network Connections, or press Win+R, type NCPA.CPL and press Enter.
The default icon view doesn't give you much information. To switch, click the View button on the toolbar, or right-click an empty part of the window and select View, then choose Details,
Scan down the Name and Device Name columns, and you might spot the names of VPNs you're using now, or have used in the past. Surfshark, IPVanish, PureVPN, StrongVPN, VyprVPN, TurboVPN and others normally add new Windows VPN connections when they're installed (though in our experience, none of them make any dumb settings mistakes.)
Other VPNs only create the connection as required, when you click Connect. If you don't see anything right now, open your VPN, click Connect, and see if a new item appears in the Network Connections.
Keep in mind that we're looking only for connections using standard Windows protocols. If a connection has the device name 'WAN Miniport (IKEv2)', for instance, it's using IKEv2 and we need to check it. If it says something like 'TAP-Windows Adapter V9' then it's OpenVPN, and we don't.
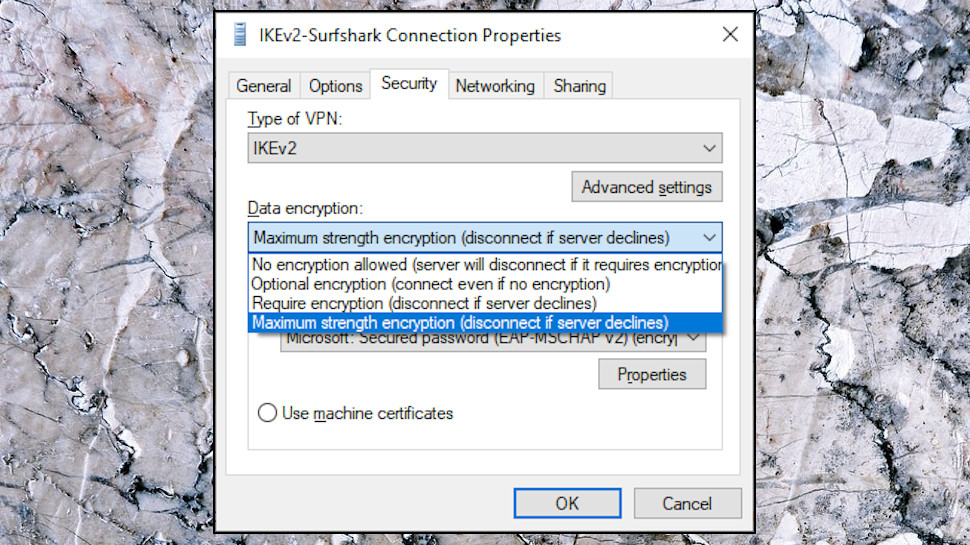
Data Encryption
Right-click an interesting connection and choose Properties to look at the settings.
Click the Security tab. (If you don't have one, this isn't a standard Windows connection. Try another.)
Ideally, the Data Encryption option should be set to 'Maximum strength encryption (disconnect if server declines).' It's not a total disaster if the connection is set to 'Require encryption', but we'd be more worried if it's set to 'Optional encryption (connect even if no encryption)' or 'No encryption allowed.'
How worried? Well, the 'Optional encryption' setting doesn't automatically leave you with no protection. If your app and the server correctly negotiate an encrypted connection, that's what you'll get. But even if it's only theoretically possible that you'd be left encryption-free, we think that's a big deal, especially as it's so easy to fix by just setting up the connection correctly in the first place.
Maybe your VPN provider has a good reason, but we'd recommend you at least ask. Fire off a message to Support. If you get a positive message plausibly explaining why having 'Optional Encryption' improves your security, great; if you get excuses or 'this doesn't really matter', maybe it's time to switch to another provider on our best VPN list.
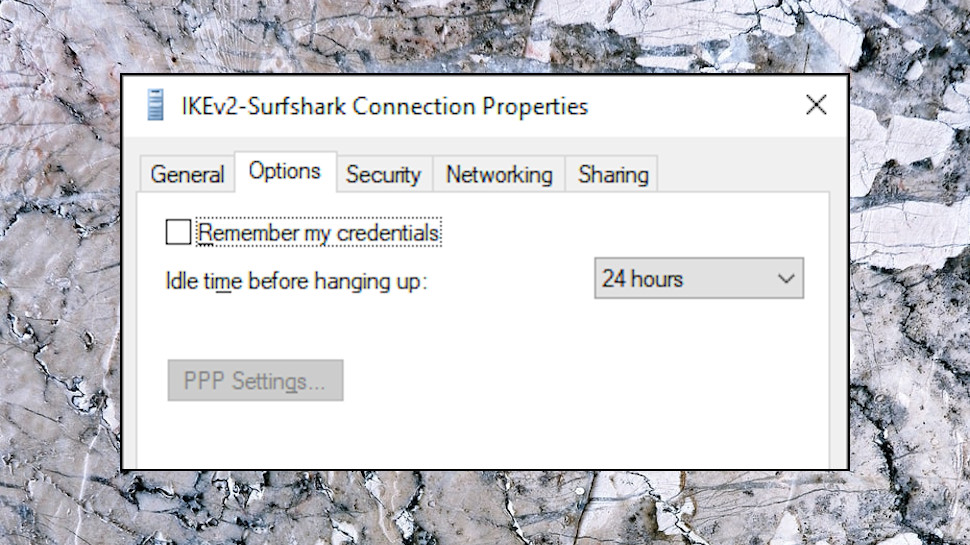
Remember My Credentials
Click the Options tab. If the 'Remember my credentials' option is checked, and the Windows connection is persistent (it was visible when you opened the Network Connections window), that means your server login username and password is saved along with the other connection details.
That's a potential risk, as your credentials can be harvested by malware or anyone else with access to your system. NirSoft's Dialupass is a tiny tool which does this with ease.
(If you download Dialupass, don't be surprised if your antivirus warns that it's a threat. Some hackers embed the program in their own malware, so antivirus apps can raise the alarm if they spot it. But Dialupass itself has been around for 20 years, and is entirely safe.)
Don't panic if your 'Remember...' option is turned on. The risk is small, and your credentials probably haven't been exposed. But why should you have to worry, at all? All the top VPNs leave this option set to Off, and if yours does something differently, ask them why.
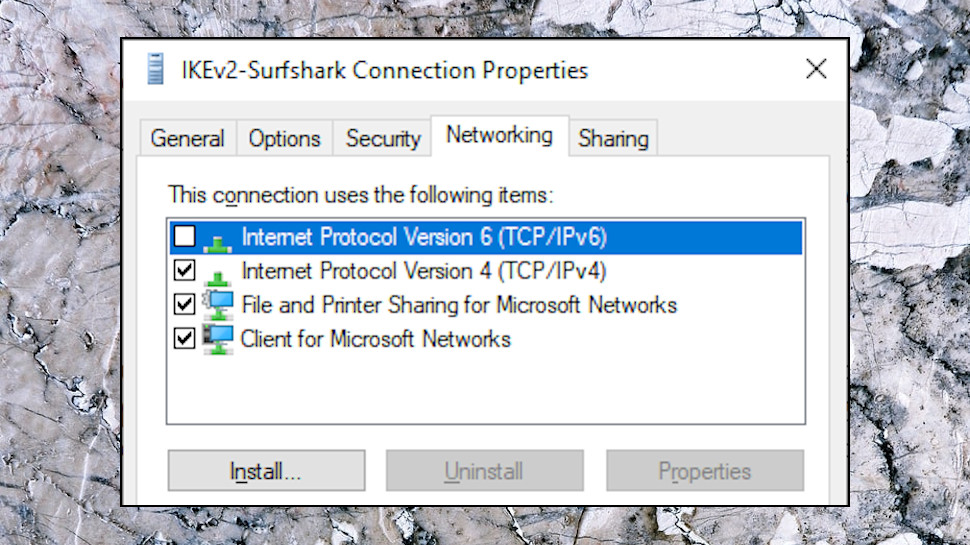
Internet Protocol Version 6 (TCP/IPv6)
There are one or two other interesting options in the Properties box. Click the Networking tab, for instance, and look at the 'Internet Protocol Version 6 (TCP/IPv6)' item. If that's unchecked, it probably means your VPN app is trying to apply IPv6 leak protection... and that's a good thing!
There are other ways to block IPv6, though, so although we prefer to see the setting disabled, having it turned on doesn't necessarily mean you're exposed. Try the IPv6 leak test at IPV6Leak.com to find out more.
Click the General tab, too, and you'll find the name of the server your VPN is trying to access. Is it a host name you expect? Search Google for the name and sometimes you'll find it belongs to another VPN provider, maybe because your current provider is reselling their services.
What next?
A poorly set up Windows VPN connection doesn't automatically mean your details have been exposed to the world, but for us, it creates a really bad impression of the provider.
It's not even faintly difficult to set up the connection correctly, so we're left wondering, why is this provider not following best practice? Have they just not noticed? Aren't they concerned about risks if they're 'too small'? What else might they have 'forgotten' to do?
You could try to fix some of these issues with a few manual tweaks. Changing the Data Encryption from Optional to 'Maximum strength encryption (disconnect if server declines)', for instance, and it might stick.
There's a chance you'll cause other problems, though, if the connection isn't set up the way the VPN expects, so generally we'd recommend you don't bother. It's not your job to make a VPN safer, that's up to the provider, and if you don't think they're delivering, switch to someone else.
Read more:
- Get protected online for less with a great cheap VPN...
- ...and with market-leading antivirus software
- Stop logging of your PC activities with our Windows 10 privacy guide
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.