Think you only need a VPN if you're accessing sensitive websites? Think again...
It might be time to use a traffic monitoring tool

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
One of the most popular reasons for buying a VPN is to protect yourself on online banking apps and other sensitive websites. Get set up and the service encrypts your connection, ensuring no-one can snoop on your most confidential online activities.
And on that basis - and unless you also use your VPN for streaming and other activities - it's tempting to think: "I don't need to use one, really, because I don't do online banking (or anything similar) over public Wi-Fi."
Seems to make sense... but there's one problem with that rationale. Your device isn't just accessing the internet via your browser - there's actually a whole lot more going on that you normally never see.
- Protect your PC with our Windows 10 VPN buying guide
- Make sure that you're running the very best antivirus
- Stop logging of your PC activities with our Windows 10 privacy guide
What else is your PC up to?
Apps, background processes, Windows services (Windows itself even), all that junk in your system tray, any of these might be logging into websites, exchanging usernames and passwords, uploading data, downloading files and generally doing who-knows-what.
Does this matter? Maybe. If you're connected to public Wi-Fi and have decided you don't need a secure VPN, then these hidden internet actions might be visible to any passing snoopers. Best hope all your background apps are communicating securely, right?
To get a better idea of the problem, it's a good idea to run a traffic monitoring tool on your system, see just how much background internet activity you've got going on. This can be complicated, but don't panic... there are other options so simple that anyone can use them, right now.
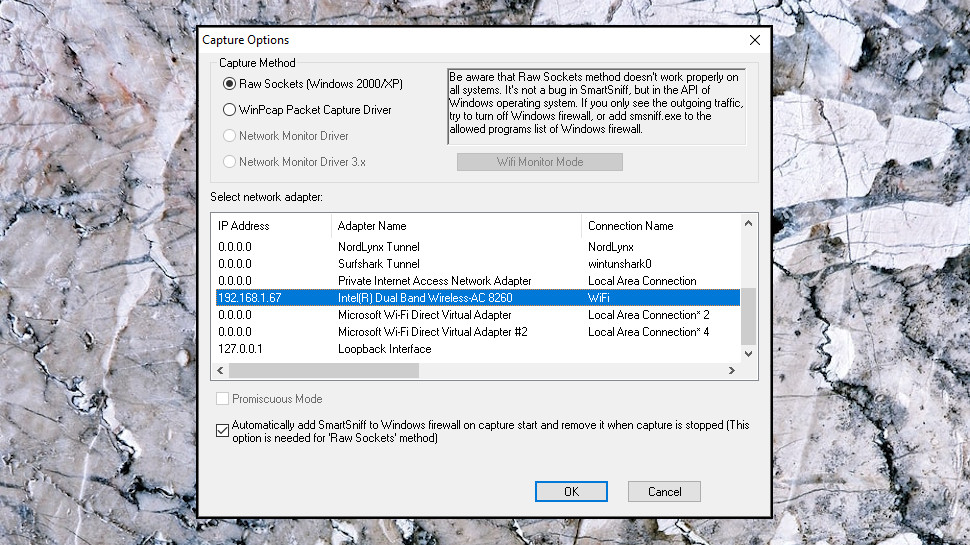
Traffic capture basics
A traffic capture tool is an application which keeps an eye on a network adapter (wired, wireless, whatever you have), and displays details on any traffic as it leaves or arrives.
This might be browser traffic, for instance, listing the URLs you're accessing. But it'll also show you email clients picking up messages, apps checking for updates, Windows 10 sending piles of data to Microsoft, and everything else you've got going on right now.
Most network tools are targeted at experts, and getting them working can seem a tricky process. The reports usually include a lot of technical details, too, so expect a lot of talk about packets, ports and protocols.
You can often get started with just a little background information on your network setup, though. The most important detail to know in advance is which network adapter you'd like the tool to monitor, and you can generally find that in a few seconds.
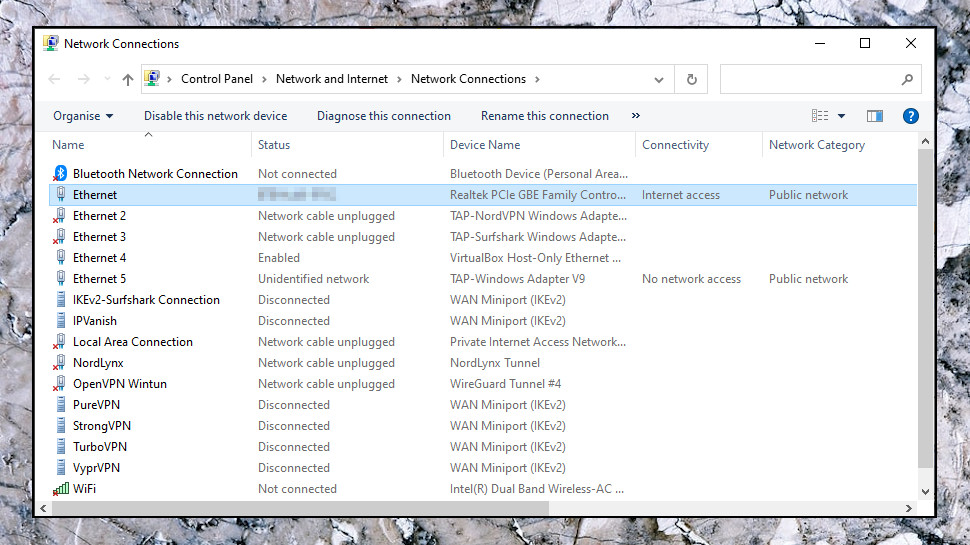
Find your active network adapter
In Windows 10, click Start, type Network, and click View Network Connections.
If you're not using Windows 10, or that doesn't work, click Start, type ncpa.cpl and press Enter, and you should see the Network Connections page.
This might have a lot of entries, especially if you've used several VPN services in the past. They'll usually create a virtual network adapter when you install them but then 'forget' to remove it when you uninstall, so the adapter list grows over time.
To find your main network adapter, though, you can usually just scan down the Connectivity column and look for the adapter labelled as having 'Internet access.' Check the name column, too. Our test laptop's Ethernet adapter is called 'Ethernet', for instance, and our Wi-Fi adapter is 'WiFi', so it was easy to find what we needed.
Repeat our steps, and make a note of the adapter your system is using. When you install and run a networking monitoring tool later, it'll display a similar list of network connections, and you'll now know exactly which to choose.
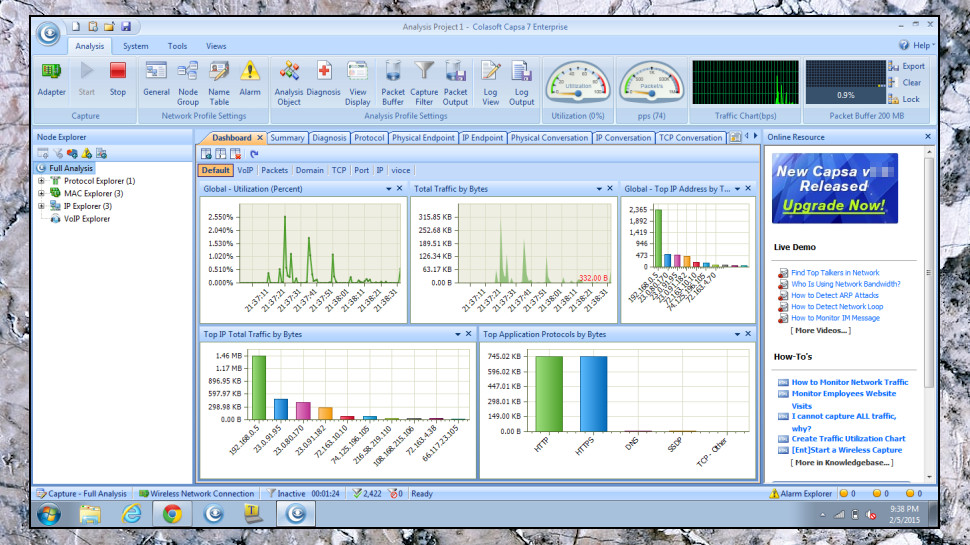
Try a capture tool
NirSoft's SmartSniff is one example of a simple traffic capture tool. Tiny (under 1MB), nothing to install, just download, unzip and run. Yet it'll still show you the sites your PC is accessing, email servers, apps looking for updates and whatever else is going on.
The open-source Wireshark is far more powerful, but it's still usable by more technical types. It's also entirely free and there are versions for Windows and Mac.
Colasoft Capsa is an enterprise-level capturing tool, with enterprise-level features and, normally, an enterprise-level price tag of $995. Fortunately, there's an excellent free version available, which is more powerful than many of the competition all on its own.
Real experts should also take a look at PRTG Password Manager. It has great traffic capturing tools, but is also a full-scale network management suite, so not for newbies.
Next steps
Our advice is if you're just interested in checking what your PC is doing in the background, and why you might want to use a VPN more often, then start with SmartSniff. It more than covers the traffic capturing basics and it's so easy you can get started within seconds.
ExpressVPN is our #1 top rated VPN
If you're still on the look out for a VPN to keep yourself protected online and for all your geo-unblocking needs, then ExpressVPN is the best of the hundreds we've tested. It's speedy, secure and simple to use. Plus, you can try ExpressVPN 100% risk free by using its 30-day money back guarantee.
- Get more internet monitoring power with the best network monitoring tools
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.
