The biggest cyber-attacks in gaming history
CD Projekt Red isn't the only victim

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Tuesday February 9, 2021, brought some surprising and disappointing news for CD Projekt Red; it announced it was the victim of a targeted cyber-attack and was being held for ransom. It is not yet clear who hacked the company or why.
Cyber-attacks are nothing new, though. The effects are devastating for games companies, costing them thousands, and causing major disruptions to their services.
We’re going to look at some of the most notorious cyber-attacks in online gaming history and discuss some of the notorious black hat hacking groups behind them.
A little history tour
The first ever recorded cyber-attack took place on November 2 1988. It was called the Morris Worm and carried out by American computer scientist, now professor at MIT, Robert Tapan Morris. He created the worm because he was “just trying to gauge how big the internet was”. Well, that curiosity landed him in prison, after he became the first person ever to be convicted under the US 1986 Computer Fraud and Abuse Act.
You could say the attack was a comedy of errors, because Morris never intended the worm to go as far as it did. He did not have malicious intent; he was just trying to highlight security weaknesses. The worm was meant to go undetected but instead it grew at an alarming rate and caused serious damage – it cost between $100,000 and $10 million to remove it. Morris was fined $10,050, received 3 years’ probation and had to do 400 hours of community service, a pretty light sentence considering.
The worm was meant to go undetected but instead it grew at an alarming rate and caused serious damage
There have since been many cyber-attacks since, targeting different companies, governments and other platforms. But when it comes to video games, the most common attack is DDOSing or Distributed Denial of Service. While DDOSing is a type of cyber-attack, it’s not hacking.

There’s a difference between DDoSing and hacking. A DDoS hits a server, website or network, overrunning it with fake traffic, leaving the server unable to operate as normal; causing latency issues or forcing it to shut down altogether.
Some Denial of Service attacks include, UDP flooding, SYN flooding, DNS amplification, or Network Time Protocol (NTP).
Hacking requires a certain level of skill and computer know-how. It can involve worms or ransomware, for example, and can have much more devastating effects on privacy, security and delivery of service.
Notable victims of cyber-attacks
Some of the biggest online gaming platforms have been victim to these attacks; let’s check them out.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Riot Games
Riot Games, the company behind popular online titles such as League of Legends and Valorant, has been hacked and DDoS’d several times over the years.
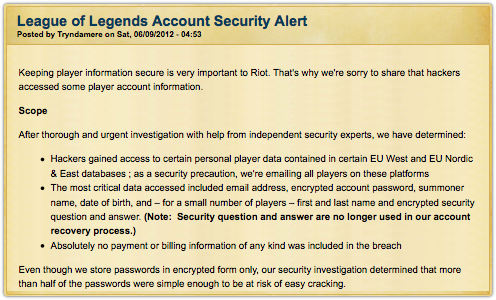
The first major League of Legends hack was carried out in 2012 by Lulzsec, a black hat hacking group responsible for several cyber-attacks on many online services, including those of government organisations.
A black hat hacking group is one that breaches computer security for selfish and malicious reasons, unlike white hat hacking groups who are motivated by ethical ones, and often aim to counter black hat groups.
The League community found out their personal information had been compromised following a statement from Marc “Tryndamere” Merril, Co-Founder and Co-Chairman of Riot Games via the LoL forum on June 9 2012.
To this day Riot has never confirmed when the attacks were carried out. This would see the beginning of a number of cyber-attacks on the gaming company.
DerpTrolling was a hacking group responsible for a number of DDoS attacks on online gaming servers, websites and services between December 19, 2013 and January 6, 2014.
Something special planned for League of Legends :DDecember 30, 2013
In December 2013 they carried out a DDoS attack on League of Legends servers, causing it to go down for days.
BOMBS AWAY! DESTINATION: Eastern EU League of Legends login server! (ON SCHEDULE THIS TIME)December 30, 2013
They were not the only hacking group that attacked League servers. The following year, August 18 2014, another group, Lizard Squad, also carried out a DDoS attack on LoL servers.
The most recent attack on Riot was on January 16 and 17 just this year. The attack targeted Riot’s LoL team-based competitive tournament mode, Clash.
📢 [LoL-TR] Due to unresolved network issues across all queues, the remainder of Clash games for the day will be cancelled and tickets refunded.January 17, 2021
This prompted an official statement in the form of a Twitter thread released by Riot Games’ Tech Lead, Brian Bossé.
Hey everyone, long time no tweet. I’m tech lead for League, and I’d like to shed a little light on League's instability in Europe of late. (1/7)January 21, 2021
This will likely not be the last attack Riot will have to deal with but this just gives you an idea of some of those it has dealt with thus far.
Capcom
Late last year Capcom was victim of a targeted ransomware cyber-attack. The creators of Street Fighter were slow to reveals its extent, announcing on November 4, 2020, only that an attack had taken place. On November 12, it announced that the stolen data belonged to nine past and current employees and that corporate data was stolen, too.
It wasn’t until November 16 2020 that Capcom revealed the attack had been much worse than was previously believed, with the personal information of 350,000 “(customers, business partners etc.)” being compromised.
During the statement it detailed the possible data breaches that took place, with a timeline of events and what plans they had to address them. The company also disclosed that a ransom was demanded, and shared the name of the group behind the attack.
"The company discovered a message from a criminal organization that calls itself Ragnar Locker, and after ascertaining that ransom money was being demanded, contacted the Osaka Prefectural Police."
Capcom explained why it took so long to understand the scope of the attack saying, "Investigation and analysis, etc., of this incident took additional time due to issues such as the information saved on servers being encrypted and access logs being deleted in the attack."
In March 2020 alone Blizzard was victim to four DDoS attacks in less than a week
Activision Blizzard
Activision Blizzard has suffered a number of DDoS attacks against its Battle.net client and game servers.
From February through September 2010, Blizzard’s World of Warcraft European server was targeted by Calin Mateias, 38, from Romania for several DDoS attacks. He was subsequently jailed for a year on May 7, 2018.
Blizzard was also one of the many online gaming platforms targeted by Derp Trolling in 2014 and Lizard Squad on April 13 2016. Attacked Battle.net denying players access to its popular titles like Starcraft 2, World of Warcraft, Diablo 3 and Hearthstone.
TARGET ACQUIRED! http://t.co/Y39Zvq0C4s (US) #offlineDecember 30, 2013
But more recently, Blizzard has been dealing with a slew of DDoS attacks, with UK Drillas claiming responsibility for an attack on WoW Classic servers in September 2019.
In March 2020 alone Blizzard was victim to four DDoS attacks in less than a week, although some players believed the outage was due to the higher-than-usual number of players accessing its servers after government lockdowns were imposed due to Covid-19.
On January 7, 2021 Blizzard were hit by another DDoS attack on its Warcraft servers.
[#Warcraft] We are currently experiencing a DDoS attack, which may result in high latency and disconnections for some players. We are actively working to mitigate this issue.January 7, 2021
CD Projekt Red
This brings us to CD Projekt Red. On February 9, 2021 it announced that a cyber-attack had been carried out on its internal network. The hacker responsible claimed they had stolen the source code to “Cyberpunk 2077, Witcher3, Gwent and the unreleased version of Witcher 3”.
They went on to claim “we have dumped all of [CDPR’s] documents relating to accounting, administration, legal, HR, investor relations and more!”, saying they had encrypted all CD Projekt Red servers, but admitting they were aware that the servers could easily be recovered via backups.
The company that has been experiencing immense pressure due to the reported issues with its Cyberpunk 2077 release did not need any more bad news.
Important Update pic.twitter.com/PCEuhAJosRFebruary 9, 2021
The hacker held the stolen data for ransom giving CDPR 48 hours to agree to their demands.
CDPR refused and, as promised, the hacker auctioned off the data on the dark web. It is unknown who the buyer is or what they plan to do with the data, which went for $7 million with an agreement that no further sale or distribution was permitted.
Just in: #CDProjektRed AUCTION IS CLOSED. #Hackers auctioned off stolen source code for the #RedEngine and #CDPR game releases, and have just announced that a satisfying offer from outside the forum was received, with the condition of no further distribution or selling. pic.twitter.com/4Z2zoZlkV6February 11, 2021
As of yet, no group or individual has taken credit for the attack.
Consequences
Several individuals involved in the black hat hacking groups, as well as individual hackers mentioned in this article have been arrested and charged.
On July 2, 2019 leader of DerpTrolling, Austin Thompson from Salt Lake City, Utah was sentenced to 27 months in prison after pleading guilty to DDoS attacks against several online gaming companies, services and websites from December 2013 to January 2014, which caused “at least $95,000 in damages”.
On October 5, 2016 Zachary Buchta, from Fallston, Maryland and accomplice Bradley Willem Van Rooy, both of Lizard Squad and Poodle Corp were arrested for “operating cyber-attack-for-hire websites”. On March 27, 2018 Buchta was sentenced to 3 months in prison and ordered to pay $350,000 in restitution to two online gambling companies that they attacked.
Hacking group Lulzsec were sentenced on May 18, 2013 following the arrests of their members in summer 2011: Ryan Cleary (32 months), Jake Davis (2 years), Mustafa al-Bassam (30 months) and Ryan Ackroyd (20 months).
Many other online gaming platforms, including Twitch, Steam, Sony’s PlayStation network and Microsoft’s Xbox Live have been targeted over the years.
Unfortunately, it’s more than likely that these kinds of cyber-attacks will continue to take place, but hopefully with much more effective anti-DDoSing and hacking software available, the amount of time lost and the impact of the attacks will continue to reduce considerably.

Rosario Blue is a writer, playwright, and freelance journalist.
She is a Global Goodwill Ambassador for Postcards for Peace.