Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
The First Hack
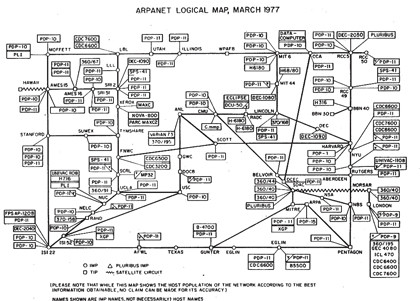
ARPANET: A diagram of the ARPAnet as it stood in 1977. By the mid-1980s it had tens of thousands of hosts. Things were so much simpler back then
Enter the command run porthack.exe. A banner appears and you're asked if you want to continue. Press y and enter.
Porthack scans a remote host for ports that can be exploited. If you know the name of the host you want to scan, enter it, otherwise enter ? to view the output. Enter a name and porthack gets to work.
First, it scans the remote host for open ports and returns a numbered list, just like a modern portscanner scanner Nmap. Enter a port number and porthack attempts to run an exploit called a buffer overrun against the service listening for connections on that port.
Porthack installs and runs a program on the remote host that creates a user account with your Telehack username and password. If it fails, run it again and choose another port until you find one that works.
All you have to do to log into the compromised system is to enter the command rlogin tandem. This will send your username and password to the remote host and log you in.
Once logged into a new computer, you should enter the help /all command to see what commands are on offer. The /all argument means that help will display a full list of all command options.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Among the commands is rootkit. This has the same meaning as a modern rootkit, giving you admin level access to the operating system. Once the rootkit command is completed, your command line prompt changes to a , showing that you're now logged in as a user called root, which is the Unix administrator account.
In tandem's root account the help command is no longer available, but a shorter form is. Type ? and hit [Enter].
One of the commands is 'setmotd'. This is our chance to leave our mark by changing the MOTD in a process called 'capturing the flag'. Enter the setmotd command then type in a suitably pithy victory message. Enter a blank line to finish.
If you now enter the motd command, you'll see what others will see. That is, until someone else works out how to do it. When this happens, you'll be sent a message to say that you've lost the flag.
Going to war
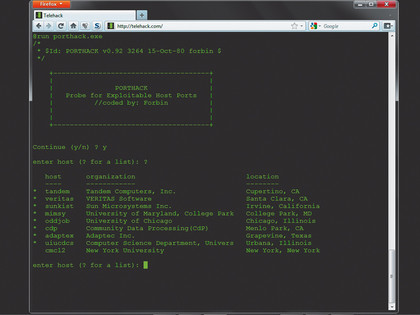
PORTHACK: Running porthack against a host will set up an unauthorised account for
you to log into. It's just like the old days
War dialling is an often-misused term. It simply means calling all the numbers in an area code to see which are answered by a modem. Although many will be fax machines, some will be computers we can then dial into.
In the directory on the Telehack server is another executable called wardial.exe. Run this by entering the command run wardial.exe and either enter an area code or ? for a list. Enter a likely code (a California area code is a good one) and wardial.exe begins calling a random block of numbers in that area. If you're lucky, it'll find a modem that is connected to a computer accepting logins.
As hackers develop their skills, they also collect a toolkit of utilities to help them. Porthack and Wardial are two such programs, but Telehack has many more spread across its hosts. Whenever you run an EXE file, it's loaded into your static core, making it available wherever you are. To run it again, type list to get its number, then type run where is its number.
Note, however, that you're initially limited to just five programs, thereby making mapping the Telehack universe a vital skill. To load a sixth program, you must use the unload command to unload a previous one.
Hackers' quest
Moving between machines can be dull, but there's more to Telehack than that. On the Telehack server, enter the command quest. You're given the task of finding a host out of the 24,000 that exist within the Telehack universe.
The target host will contain a file giving you further instructions. These include entering secret commands and system calls that will increase your status and control over the Telehack universe.
Along the way, you'll pass through computers with more executables to map, files full of information and other stuff you can use. Completing quests also gives you bragging rights over other users.