Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Over the past decade, hacking tools have undergone a huge transformation. For the most part, they used to be command line affairs with myriad options, dumping results into files that then had to be pored over for clues or manipulated using complex Perl scripts.
Those days are now largely gone for all but the most advanced hackers, because today's hacking tools are finally catching up with the fictional interfaces seen in films during the 1990s.
The term 'script kiddie' used to be a term of abuse aimed squarely at neophyte hackers who didn't really know what they were doing, but advances in professional quality hacking applications have now put advanced attack tools in the hands of newbies.
The combination of easily used tools and advanced interfaces is dangerous in the wild, as hacking your own private network will demonstrate.
Back tracking
Thanks to its developers' extensive work to pull together techniques for exploiting vulnerable operating systems and delivering malicious payloads via those exploits, the Metasploit Framework hacking tool has done more to make hacking accessible to the masses than any other.
The free edition is no exception. It's so important that network security professionals rely on a special Linux distribution called BackTrack, in which everything needed has already been assembled, compiled and tested.
What's more, BackTrack even contains a very good third-party graphical user interface to the Metasploit Framework that takes care of all the tedious details of setting flags and system variables, and allows us to concentrate on the job in hand.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
This interface is called Armitage. To demonstrate the power of Armitage, we'll set up a target Windows XP PC and another running BackTrack using our old friend VirtualBox.
Download the VirtualBox installation executable from the official website at www.virtualbox.org/wiki/Downloads. Double-click the executable to install and accept all the defaults.
During installation, several sub-windows will appear asking to install various modules from Oracle. These are to do with support for USB devices and so on. Agree to install them.
When you run VirtualBox, the VirtualBox Manager appears. This lists all the virtual machines you create and allows you to modify their virtual hardware and to take snapshots of their states.
When you first run the VirtualBox Manager, you'll have no OSes installed. In the language of virtualisation, the operating systems you install into virtual machines are called guests. The actual OS running on the real hardware is called the host. We're assuming that your host is Windows 7.
The BackTrack ISO can be downloaded from the official website. Select Backtrack 5 R1 and the ISO version to directly download.
To install BackTrack as a guest, create a new virtual PC and select 'Ubuntu Linux' as the type. Accept the defaults and once the virtual PC has been created, select it in the VirtualBox Manager and click on 'Storage' in the right-hand panel.
In the window that appears, click the 'Empty' CD symbol. The drives attributes are in the right-hand panel. Click the CD symbol and select 'Choose a virtual CD/DVD disk file'. A file selector appears. Go to the BackTrack ISO file and click 'OK'. Dismiss the window by clicking 'OK' and start the guest.
You'll be greeted by a Boot: prompt. Press [Enter], and also press [Enter] when the graphical boot screen appears. The OS boots into live CD mode.
When the terminal appears, enter the command startx to boot the graphical desktop. When this appears, double-click the 'Install BackTrack' icon to install it on the guest's virtual hard disk. You can select all the defaults during installation by clicking 'Forward' on each screen.
Finally, click 'Install' and the process begins. The installation takes around 20 minutes to complete.
For our target computer, we'll install an old copy of Windows XP Home. Shut down both virtual machines and select one in VirtualBox Manager. Click the 'Network' section in the right-hand pane and a sub-window pops up. Click the 'Attach to' pull-down menu and select 'Bridged', then click 'OK'. Set both guests to bridged networking in this way. It will ensure that when they boot their operating systems, they request their own IP addresses from the DHCP server in your broadband router.
Boot the guests and in Windows open a command line and enter the command ipconfig to make a note of this address.
The front end
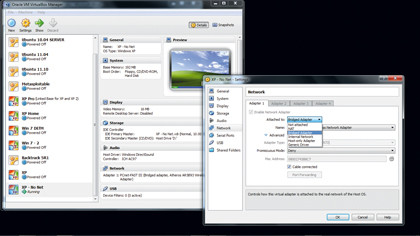
BURNING BRIDGES: Setting both virtual machines to use bridged networking gives them IP addresses on your home network
Before we begin hacking from BackTrack, we need to make sure we have the latest updates for the underlying Metasploit Framework. We then need to start the Armitage interface.
We can achieve both tasks by opening a terminal (which is on the launcher bar at the top of the desktop) and entering the command msfupdate ; armitage. This updates the exploit and payload libraries the starts Armitage.
After a few minutes of verbiage, you'll be greeted by a popup box. Click 'Connect' and accept the offer to start the Metasploit server. Armitage will then keep trying to connect for a few seconds as the server starts up.
The Armitage user interface consists of three panes. To the top left is the exploit library. The top right will list the discovered targets, and the lower pane shows the Metasploit terminal. More tabs will be added to this lower pane as we fire off commands.
Let's first scan the target guest using the port scanner, Nmap. Click 'Hosts > NMAP scans > Intense scan, all TCP ports'. Enter the IP addresses of the computer on your network that you wish to scan. You can enter multiple IP addresses using a range (192.168.1.3-5) or individually, (192.168.1.3,5).
Nmap takes several minutes to do its stuff, and its tab in the lower pane fills with information about its progress and what it discovers about the targets, including the operating system. Once complete, the target will be added to the top right panel.
The Nmap session will end with a pop-up inviting you to scan for possible attacks against the scanned computers. This is where the real fun really begins.
Click 'Attacks > Find attacks'. A moment or two later, you're rewarded with another popup wishing you happy hunting.