Business on the move: how to secure 4G and public Wi-Fi connections
Wi-Fi hotspots continue to have security issues…
Working on the move is now commonplace, and being able to connect to the internet anywhere and at any time has become an essential business service.
The plethora of Wi-Fi hotspots offer fast and cheap access. However, for business users, security must at all times be of paramount importance, which is why many mobile business users have moved away from using Wi-Fi to 4G access services.
Cyber security company F-Secure says: "Public Wi-Fi simply wasn't built with 21st century security demands in mind. When you use public Wi-Fi without any added security measures, you leak data about yourself from your device."
So if public Wi-Fi is simply too insecure for business users, what's the solution?
As mobile phone networks have improved, speeds have moved past what can be expected with an average Wi-Fi connection, making 4G the connection channel of choice for fast and secure internet access on the move.
Advances in mobile connectivity offer solid speeds depending on the carrier and the location, often better than can be expected with the average Wi-Fi connection, especially if you're trying to use a congested Wi-Fi hotspot.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The speed and convenience that 4G connections have delivered to business users in particular has meant their popularity has rocketed – so using 4G securely is now a priority. There are a number of simple steps you can take to ensure your 4G connection is always safe and secure.
1. Install mobile security applications
When using mobile devices with 4G always ensure you have adequate protection installed. McAfee Mobile Security is a good example and is available for Android and iOS devices.
2. Take care with automatic updates
If you are in the habit of simply downloading each new update you are offered for your 4G devices, start to assess where these updates are actually coming from. Ensure each update is legitimate and from your 4G service provider, and isn't malware disguised as an update. Automatic updates can be disabled on Android, so they can be individually approved.
3. Use a mobile VPN (Virtual Private Network)
If you want to ensure that sensitive data is protected as it moves to and from your mobile devices, setting up a VPN is an ideal solution. Both Android and iOS support the use of VPNs. Windows and Mac OS X also have a range of VPNs to choose from.
4. Use strong passwords
The password may be the bane of many users' lives, but they're still the main way that Wi-Fi login is enabled. Develop a strong password regime, and don't use the same password for all your logins. There are lots of password managers to choose from – we've rounded up the best of them in this article.
5. Forget the Wi-Fi network
Try and get into the habit of connecting to a public Wi-Fi hotspot for the shortest possible time, and when you've finished ensure your device forgets the network – this prevents your device becoming vulnerable when you're not using it yourself.
It's a commercial imperative to ensure that all the devices you use over a 4G network are protected by the latest anti-malware applications, and that every live connection you make to the internet is done over a secure channel encrypted to combat any eavesdropping. When working on the move, security should be your top priority.
If you have no option but to use a public Wi-Fi hotspot, follow these steps to ensure that your connection is secure:
1. Connect using a reputable Wi-Fi provider
Think about where the Wi-Fi hotspots you use are located. Are these connections legitimate? Check the credentials of the service provider before you connect and transmit or receive sensitive information.
2. Use a VPN
As we've already mentioned, one of the easiest ways to ensure your data is safe and secure is to always use a VPN. Today these are efficient and straightforward to use. Some good examples are Avast SecureLine, proXPN and Hotspot Shield.
3. Only connect with secure websites
When you're working try and resist the temptation to check your Facebook profile or do some online banking – these are the kinds of websites cybercriminals target to gain personal information they can exploit. If you need to connect to these sites, use a service such as HTTPS Everywhere to encrypt your connection.
4. Install antivirus and anti-malware applications
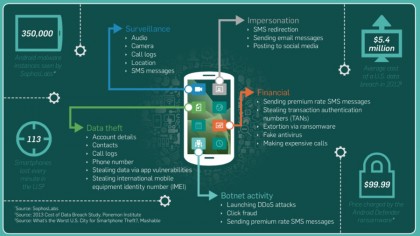
The connection you choose is only half of the security issue you face. Often, malware will infiltrate your notebook or phone and begin to crack your passwords.
SophosLabs, which has studied the issue of malware on mobile devices for a decade, warns that mobile malware is on the rise. Its startling observation is that Android malware increased for every month of 2017, with a startling 30% of this malware in the category of particularly malignant ransomware.
Keep your security applications – such as one of our recommended applications – up to date at all times.
5. Turn off all sharing options
At home you probably share your computer with a printer or maybe even an external hard drive. When you're using a Wi-Fi hotspot turn off the sharing options, as these can give cybercriminals an open door to penetrate your computer.
6. Monitor the apps you use
Cybercriminals can use installed apps as a doorway into your phone or tablet. If one of your apps begins to behave strangely delete it immediately, as it may have been hacked.
7. Never jailbreak your phone
Jailbreaking a device will instantly disable the built-in security. Only use apps that have come from a legitimate source on a phone or tablet that has not been modified in any way.
8. Turn off Bluetooth
Switching off Bluetooth when you're not using it is a sensible option as it closes another channel that could be used to hack your device – it also saves battery life.
9. Encrypt your sensitive data
All the data that moves over a VPN will be encrypted, but if you don't have a VPN available then encrypting your emails is a sensible precaution to take if they contain attachments with sensitive information.
- For further wireless security advice, check out: How to keep your Wi-Fi network secure