VPN vocabulary: key terms and jargon explained
Encryption, ciphers, protocols; VPN jargon can get complicated pretty fast.

- Advanced Encryption Standard (AES)
- Catapult Hydra
- Cipher
- Dark web
- Deep Web
- DD-WRT
- Deep Packet Inspection (DPI)
- Domain Name System (DNS)
- DNS Leak
- Eavesdropping Attack
- Encryption
- End-to-End Encryption (E2E)
- Encryption Key
- Five Eyes Alliance
- Geo-blocking
- I2P (Invisible Internet Project)
- IP address
- IPv4
- IPv6
- IP leak
- Jurisdiction
- Key Exchange
- Kill switch
- Latency
- Lightway
- Logging
- Man-in-the-middle attacks
- No Logs Policy
- Obfuscation
- OpenVPN
- Perfect Forward Secrecy
- Ping
- Point-to-Point Tunneling Protocol (PPTP)
- Protocol
- Proxy
- Public Wi-Fi
- Simultaneous Connections
- SmartDNS
- Split tunneling
- strongSwan
- Surface Web
- Throttling
- Tor
- Tunnel
- VPN Client
- VPN Server
- Warrant canary
- WebRTC
- White box
- WireGuard
The internet can be a confusing place—especially when you start looking into online security and privacy which is a minefield of strange terms like AES-Encryption, IP leaks, throttling, and geo-blocking.
You might have heard about these things called VPNs (Virtual Private Networks), but not be clear on what they are. Even if you're more familiar with the best VPNs out there, the litany of terms used by service providers isn't always straightforward.
I've put together an easy-to-read list of definitions for all this technical gobbledygook that'll help you get to grips with it—and don't worry, I promise it's not as scary as it sounds.
Advanced Encryption Standard (AES)
Advanced Encryption Standard (AES) is an industrial-strength encryption cipher used to encrypt and decrypt data. As there are different versions, they are differentiated by using the "length" or number of bits used in the encryption. AES-128 encrypts using a 128-bit key while AES-256 uses 256 bits. More bits equals stronger encryption, and AES-256 is currently the strongest around.
Catapult Hydra
A proprietary VPN protocol devised and used by Hotspot Shield. The company hasn't published full details on how it works, but the Hotspot Shield website has published some technical details, and cites that the protocol uses TLS 1.2-based security.
Cipher
A cipher is a set of rules used in data encryption and decryption, and there are lots of different ciphers in use today.
Blowfish, for example, is a free cipher created way back in 1993 that remains popular today. Advanced Encryption Standard (AES) is stronger, however, and is the current industry standard for most secure VPNs.
Dark web
A term used to describe web content that exists on darknets—networks that use the internet but require specific software to access them. The best-known and most used of these are Tor and I2P.
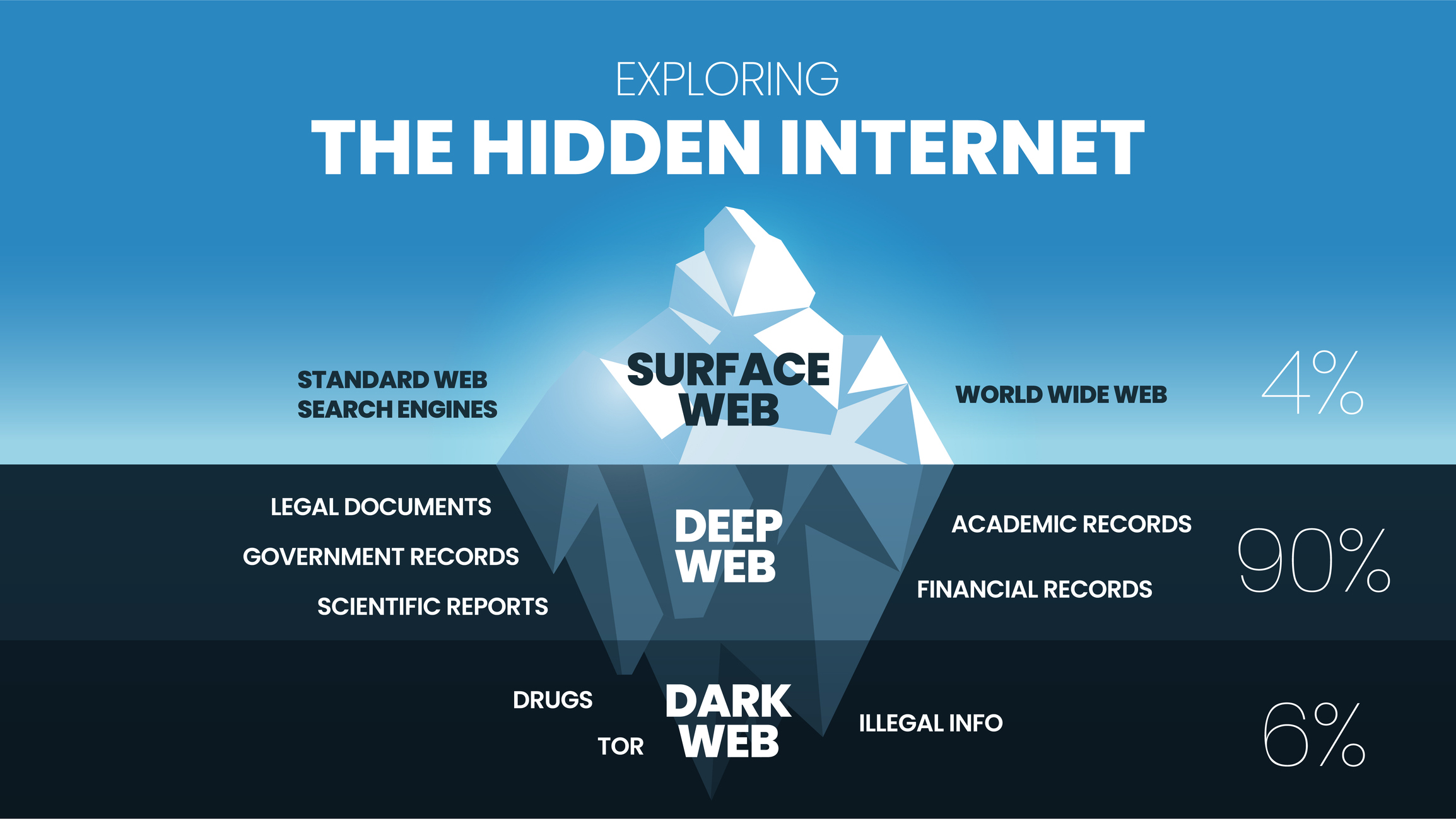
Deep Web
Not to be confused with the dark web, the deep web describes any website that is not indexed by search engines like Google. Sites on the deep web can be accessed by a direct URL or IP address but might also require a password.
Uses of deep web sites include webmail, online banking, cloud storage, and forums that require you to sign up to view content.
DD-WRT
Open-source firmware (the software embedded in a device that tells it how to work) for routers that gives you a great deal of control and customization—and boost your router's overall performance. You can set up DD-WRT so that all connected devices are routed through a VPN, extend your Wi-Fi range, set it up as a NAS hub, print server, and more.
DD-WRT can be manually installed onto your current router or, if you prefer, you can pick up a pre-configured router.
Deep Packet Inspection (DPI)
A set of technologies used to analyze network traffic and understand its purpose. Deep packet inspection can be used for good (to detect and block malware or hackers), but your ISP might also use it to keep tabs on you when you're torrenting or streaming. It can also be used by repressive governments to monitor citizen internet usage.
Domain Name System (DNS)
DNS lies at the heart of the internet as we know it today. At its core, DNS is a database used to translate the easy-to-understand and remember web addresses (URLs) that we are familiar with to their "true" numerical IP addresses that our computers use
For most of us, our default DNS provider is our ISP. When you use a VPN, however, your DNS is then provided by the VPN service.
DNS Leak
A DNS leak occurs when your traffic requests are routed to your ISP's DNS servers—even though you're using a VPN. Certain VPN features, like split tunneling, can cause DNS leaks, where traffic is still sent over the local network despite the active VPN connection.
Eavesdropping Attack
This is when a hacker intercepts, deletes, or modifies data being transmitted over an unencrypted, wireless internet connection—like the free Wi-Fi hotspots you can connect to without a password. Eavesdropping attacks are also known as "sniffing" or "spoofing" attacks.
Encryption
The process of converting information into another form using a mathematical algorithm (known as a cipher) to prevent unauthorized access. Encryption is the one thing that prevents just about anyone from being able to read (or track you with) your digital data—it's the cornerstone of all internet security.
Strong encryption is very difficult to crack without the correct "keys", so who holds or can access these keys is a vital security issue.
End-to-End Encryption (E2E)
End-to-end encryption is a phrase you'll see in lots of different places. E2E applies encryption to messages on one device and ensures that they can only be decrypted and opened by the intended recipient.
A lot of services don't use E2E encryption, and encrypt your data (and hold your keys) for you. This can come in handy, especially if you're trying to recover a lost password or sync them across devices, but it means that the services could be legally compelled to hand over your encryption keys.
Encryption Key
An encryption key is a random set of information used by a cipher to encrypt and decrypt data. Ciphers used by VPN providers are typically between 128-bits to 256-bits in key length—a bigger number means more variations in the encryption process, which makes it more difficult for bad actors to force access.
Five Eyes Alliance
A surveillance alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. Intelligence is freely shared between security organizations of member countries, and the true extent of these practices was uncovered by Edward Snowden back in 2013.
Other alliances exist, too, including the Nine Eyes and Fourteen Eyes—and, as a rule, I recommend avoiding VPN services with headquarters in these countries.
Geo-blocking
Geo-blocking limits access to online services based on geographic location. For example, Hulu is only accessible to viewers in the US and, likewise, BBC iPlayer is restricted to UK residents.
Usually, geo-restrictions are enforced by streaming platforms to comply with licensing agreements that dictate where certain shows and movies can and can't be broadcast. A streaming VPN bypasses these obstacles, however, and can fool these sites into thinking you're elsewhere, so you can check out content from around the world.
I2P (Invisible Internet Project)
A decentralized network similar to the Tor network, designed from the ground up to be a self-contained darknet. As with Tor, users connect to each other using peer-to-peer encrypted tunnels, but there are some key differences, including the use of a distributed peer-to-peer directory model which makes I2P faster and more secure than Tor, and more robust. It is, however, not particularly user-friendly.
IP address
Every internet-connected device is assigned a unique numerical identifier—and this is your IP address.
One of the most important functions of a VPN is its ability to hide your real IP (Internet Protocol) address from third parties and disguise your approximate location. This is particularly handy for folks who want to unblock streaming content and websites from overseas.

IPv4
Internet Protocol version 4 (IPv4) is the method used to send data from one device to another.
The protocol also assigns unique IP addresses to devices that consist of four numbers separated by periods, such as: 76.221.13.101. The number of available IPv4 addresses is rapidly dwindling, however, and the internet as a whole is now moving on to IPv6.
IPv6
IPv6 is the successor to IPv4, and the newer way to assign IP addresses to internet-enabled devices and determine how they communicate.
Currently, IPv6 isn't as popular as its predecessor, but things are changing quickly. IPv6 is simpler, faster, and supports more than 1028 IP addresses than IPv4—which means we shouldn't run out of them for a good long while.
IP leak
An IP leak occurs when a user's real IP address is visible to the outside world, even when using a VPN.
IPLeak.net, IPLeak.org, and BrowserLeaks.com use various techniques to detect IP and DNS leaks. Many VPNs have their very own leak test pages, too, and ExpressVPN's DNS leak test is a great example.
Jurisdiction
When we talk about VPN jurisdictions, we're talking about where they're based and what country they're incorporated in. This is critical information, as the country's legal system will dictate which laws and privacy regulations the VPN service is subject to.
Key Exchange
A process where two parties swap a shared key which they can use to create an encrypted communications channel. Key exchange lies at the heart of secure file transfers and communication, enabling two parties to share symmetric keys over an insecure network like the Internet.
Common key exchange methods include Diffie-Hellman and Internet Key Exchange (the IKE in IKEv2.)
Kill switch
A kill switch is a feature built into most VPNs that'll prevent you from accessing the internet if your VPN connection drops. This is important, as even the most stable VPN connection can occasionally flub and, if you aren't using a kill switch, your internet activity will be visible to anyone watching.
Your kill switch will stop you from heading back online until the VPN connection is back up and running, keeping your digital privacy under lock and key.
Latency
The time it takes for data to travel across a network from the source to the destination—which especially important to online gamers.
Connecting to a VPN routes your traffic through the VPN server before it reaches its final destination. Ultimately, this extends its journey and can create latency, but this encryption prevents third-party snooping.
Lightway
A VPN protocol created by ExpressVPN. True to its name, Lightway is more lightweight than OpenVPN, with fewer CPU requirements that aren't as taxing to the battery life of mobile devices. It connects faster than OpenVPN, too, with a performance comparable to WireGuard.
Unlike most proprietary VPN protocols, Lightway is open source, meaning anyone can examine the source code for themselves to check for vulnerabilities.
The Lightway experts: ExpressVPN
Lightway is the brainchild of the folks over at ExpressVPN—a service with speeds that live up to its name. It's a speedy provider that doesn't pull punches when it comes to security, either, making it a great pick for day-to-day browsing. You can try ExpressVPN for yourself with a 30-day money-back guarantee.
Logging
In VPN terms, logging refers to any records a provider makes of users accessing its service. Most VPNs claim not to log the sites you visit, the files you download, or any details of what you get up to online, but they're not all telling the truth.
Connection logs tend to be anonymized and tell the provider about which server you're using and for how long. These logs are used for general maintenance and troubleshooting. Usage logs are the ones to worry about—they can contain your IP address, your browsing history, and more, which is a major blow to digital privacy, and why I recommend sticking to reputable no-log VPNs.
Man-in-the-middle attacks
A cybersecurity attack where an attacker eavesdrops on communications between targets. For example, a hacker might use a fake or hijacked router to capture passwords or redirect you to a dodgy phishing site.
Using a VPN protects you from man-in-the-middle attacks by encrypting your activity, making it more difficult for anyone to see what you're doing.
No Logs Policy
A policy that states that the VPN provider will not keep records of what users do whilst connected to a server. The most trustworthy VPNs have a clear, transparent no-logs policy displayed on their homepages and, ideally, will invite independent auditors to verify their claims.
Obfuscation
Obfuscation refers to any technology that makes it more difficult for websites, ISPs, or nosy third parties monitoring the network to detect that you're using a VPN.
If you're on the hunt for a China VPN, obfuscation is doubly important, as the country goes to great pains to censor internet content and block VPN use.
The best VPN with obfuscation: NordVPN
If obfuscation is at the top of your shopping list when it comes to VPNs, you'll want to check out NordVPN. The provider has its very own obfuscated servers you can use to evade VPN bans (and other obstacles)—which is why it's my #1 China VPN, too. Take NordVPN for a spin with a 30-day money-back guarantee.
OpenVPN
A highly configurable VPN encryption protocol. While not as fast as WireGuard (or other provider-specific protocols like Lightway or NordLynx), its flexibility and battle-tested security make it an enduringly popular choice.
OpenVPN is open source, too, meaning anyone with an interest can check out the source code for themselves to check for bugs, vulnerabilities, or backdoors.
Perfect Forward Secrecy
An encryption type that secures communications between clients and servers by using unique keys generated automatically every time a connection is made.
The ever-changing nature of Perfect Forward Secrecy prevents hackers from decrypting data, even if the most recent keys used in a session are stolen by an attacker, and is used by VOIP and messaging clients.
Ping
A measure of latency describing the time it takes for data to travel across a network from one device to another.
Connecting to a VPN means the data must be routed through the VPN server before traveling to its destination. It's an extra step that can impact your internet speed and increase your ping time. However, the fastest VPNs ensure that any influence on your performance is as minute as possible.
Point-to-Point Tunneling Protocol (PPTP)
PPTP is an old VPN protocol available on just about every VPN capable platform and device.
While PPTP is slowly being phased out, it's still used by businesses and supported by companies like Microsoft in its server products. It is, however, widely known to be insecure and should never be used if rock-solid security is your main priority.
Protocol
A set of instructions that VPN apps use to connect to, and communicate with, servers.
The VPN protocol defines how an app logs into the VPN server; how the server will prove its identity to the app; the methods used to send data, what kind of encryption is used, and all other aspects of VPN connections. Today's most popular protocols include OpenVPN, WireGuard, and IKEv2.
Proxy
A proxy is a server that acts as an intermediary between your computer and the internet. Any traffic routed through a proxy server will appear to come from its IP address, not yours.
Unlike a VPN, proxy servers typically lack encryption, making them better suited to unblocking geo-restricted content than safeguarding your browsing sessions.
Public Wi-Fi
Wi-Fi hotspots, the sort you'll find in cafes, hotels, and airports, are designed for anyone and everyone to connect to them. You won't need a password to access these hotspots—and that means they're not very good at protecting your data.
Hackers tend to see Wi-Fi hotspots as easy pickings, which is why I recommend picking up a VPN for traveling if you plan on making use of these free connections.
Simultaneous Connections
The more simultaneous connections a VPN offers, the more devices you can connect at the same time. With two simultaneous connections, for example, you could connect both a laptop and a smart phone to your VPN service without needing to disconnect one of them.
The number of connections of offer varies widely depending on the provider. Some premium services give users unlimited connections to play with, though you'll usually get anywhere from seven to ten.
SmartDNS
SmartDNS refers to services that help you evade geo-blocking restrictions by connecting to DNS servers in different counties. Different services have servers in different locations, but almost all providers have coverage in the United States and United Kingdom due to the overwhelming popularity of platforms like Netflix and BBC iPlayer.
Because no encryption is involved, SmartDNS is faster than connecting to a VPN, but it provides none of the privacy and security benefits.
Split tunneling
A VPN feature that allows you to determine which apps use the VPN connection and which use your regular internet connection.
Split tunneling Is useful when an app doesn't play well with your VPN. For example, if you can't access local streaming platforms because your VPN is spoofing your location, you can set up split tunneling to direct the traffic from the streaming app through your normal internet connection.
strongSwan
A popular open-source VPN app for Windows, Mac, Android, and iOS.
StrongSwan doesn't have many features on its own, but it can be configured to work alongside most VPNs, which is handy if you're having issues with a provider app. You'll need to be comfortable with concepts like encryption and networking to get the most out of strongSwan, however, so I generally don't recommend it to beginners.
Surface Web
The surface web is also known as the visible, open, or indexed web. It describes any site readily available to the general public that can be found using a standard search engine like Google or Bing.
Throttling
A tactic used by ISPs to control your connection speed if you're doing a lot of streaming (via platforms like Netflix and YouTube) or downloading torrents.
With a VPN, you can avoid throttling, as it'll cloak your original IP address and prevent your ISP from seeing everything you get up to online and subsequently deciding to hit the breaks.
Tor
The Onion Router (Tor) is an open-source project network that provides free software designed to help users access the internet with improved anonymity. Unlike VPNs, where the VPN providers are privy to your real IP address and internet traffic, Tor routes your signal through multiple nodes. Each of these nodes is only aware of the IP addresses of the node in front and behind it, meaning that, at no point, can anyone learn the entire route linking your computer and the websites you access.
Tunnel
When VPN providers talk about a tunnel, they're describing the secure, encrypted connection between your computer and another network. For example from your mobile phone to the VPN server.
VPN Client
A VPN client is the software you use to connect your device to a VPN service. On computers, it's usually referred to as a VPN client or VPN program and, for mobile devices, it'll be a VPN app.
VPN Server
VPN servers are offered and maintained by the VPN provider. You can connect your device to a VPN server using the encrypted tunnel, and take your pick of hundreds of servers dotted around the globe, though some VPN services have massive fleets of thousands of servers.
Warrant canary
A strategy used by VPNs to alert users that the provider has been served with a gag order. A warrant canary typically takes the form of a regularly updated statement that no gag order has been served. If the statement does not receive its regular update, then the warrant canary has been "tripped", and readers should assume the worst. Warrants often forbid a provider from telling users that an investigation is underway, but viewing the Warrant Canary allows us to see if anything has changed.
If you want to see real-life examples, then check out Surfshark's Warrant Canary and NordVPN's Security Efforts page.
WebRTC
Web Real-Time Communications (WebRTC) is an open-source technology that allows web browsers and other apps to support audio, video, and other communications. It was developed by Google and is built into many modern browsers, including Edge, Firefox, Chrome, Safari, and Opera.
WebRTC can help websites detect the real IP address of a visitor, however, sometimes even if they're using a VPN. This problem is also known as a WebRTC leak.
The BrowserLeaks site detects WebRTC leaks, the ExpressVPN site has a WebRTC Leak Test page, and NordVPN has more detailed WebRTC advice.
White box
A type of software testing where auditors have access to both the VPN apps and their source code.
White box VPN audits provide more detailed results than black box tests, where the auditors only see the same information as end users and don't have access to the underlying source code of the apps.
WireGuard
WireGuard is the most up-to-date VPN protocol used by VPN providers. Compared to OpenVPN, it is easier to set up, offers faster connection speeds, and is more secure. Some VPN providers, like NordVPN and ExpressVPN, offer their own custom versions of WireGuard, too.
Super-fast WireGuard speeds: Surfshark
Want to take WireGuard for a whirl yourself? Surfshark implements the protocol seamlessly, making it a fantastic Netflix VPN capable of keeping up with your movie marathons and HD streaming. Plus, it's a budget-friendly service that packs a lot of value into bargain prices. Make sure you take advantage of its 30-day money-back guarantee.

River helps take care of cybersecurity content on TechRadar—ranging from breaking news pieces, reviews, and buying guides.
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

After graduating from Stirling University with a qualification in Education, Shaun accidentally fell into the technology sector in the late 1990's and has stayed there ever since, working for companies such as PSINet, IBM and ProPrivacy in a variety of roles from Systems Administration to Technical Writer. Being around since the birth of the modern internet, he's seen the way that technology has expanded to become an integral part of everyday life, and how people's understanding and ability to retain any kind of privacy has lagged behind.
Shaun is a strong believer in the rights of the individual to have their personal data protected and their privacy respected – a belief made all the stronger in an age of surveillance from both governmental bodies and private companies all around the world.
He spends his spare time cooking, riding his motorbike and spending far too many hours in Star Trek Online hunting Klingons and Borg.
- Mike WilliamsLead security reviewer
- River HartTech Software Editor


