How to strengthen and secure your Windows 10 log-in
Double authentication is key
Introduction
Double Authentication adds a second layer of security on your computer, device or account. By adding a primary layer of security, your password, you can log into your computer normally. Double Authentication requires you to input a 6-digit code that is randomly generated after 30 seconds on an app that you install on your phone. If you forget your original password, then Google can send it to a backup email or your phone (via SMS).
So, even if someone steals your password, they would need to have a Google Authentication App to generate a random key.
How to set it up
Download the Google Authenticator app - iOS here and Android here - and download that to your mobile phone.
The next step is harder, I promise.
Getting Windows 10 with Double Authentication
Once all the prerequisites are done, open settings in the taskbar and click on Accounts. Note - if you are using a local account on your computer following through with these steps will link your computer with your Microsoft account. To setup your "Microsoft Account" click here.
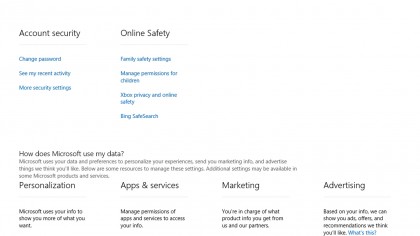
Click on "Manage my Microsoft Account" and Edge will open to your Microsoft Account page. Once opened, click on "Security and Privacy."
On this page, click on a link for "More security sessions," which is the third link on the left-hand column which is the third one under the "Account security" header. Log in with your Microsoft credentials.
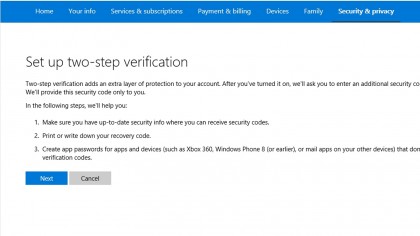
Scroll down and under "Two-step verification" make sure you click on "activate two-step authentication."
Setting up the app
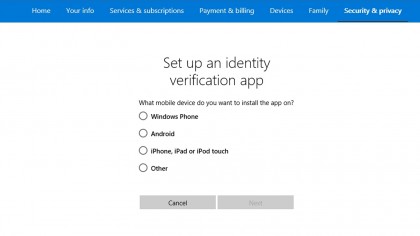
Click on the "Set up identity verification app" and follow the steps to add Microsoft to your Google Authenticator app. Make sure the app is open and click the '+' button and choose "Scan Barcode." The app is really easy to use. You just point your phone's camera toward the screen and scan the barcode and everything is already setup for you.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
