Secure your VPN in a few steps
Check out these ways to make your VPN connection more secure
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
VPN services, by default, provide excellent security and anonymity, but that doesn't mean they're uncrackable. If you want to be truly secure, there's more you can do. Here we've listed some ways to better ensure your privacy and protection.
Changing the VPN protocol
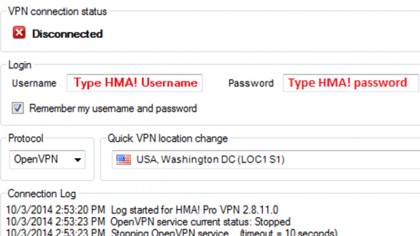
There isn't just one type of VPN - there are actually a variety of different VPN protocols in common use, and many VPN providers actually give you a choice. Sometimes that choice is available in the connection app; sometimes it's simply a configuration option for third-party VPN tools.
Most commonly, your options are PPTP (point to point tunneling protocol), L2TP/IPSec (layer 2 tunneling protocol) and OpenVPN.
Particularly if you're setting it up yourself on a mobile device or flashed VPN router, PPTP and L2TP are usually better options, since they're much easier to configure. In many cases, you only really need a server name, username and password.
It's absolutely worth using OpenVPN, however. PPTP has essentially been cracked – it uses weak 128-bit encryption, and the initial connection and authentication process can be intercepted and the data decrypted and compromised. On the upside, it's actually the fastest of the protocols because it has the lowest encryption overhead.
L2TP is more secure. But it also adds a lot of overhead, and is the slowest of the protocols.
OpenVPN is the best of both worlds: it's fast, recovers quickly from a lost connection and is completely secure as far as we know. If you have the option, it's the way to go.
Utilizing your kill switch
One of the issues with a VPN connection is that if the VPN connection fails – if the VPN server goes down or the connection is lost – your computer will immediately drop back to your regular internet address, potentially making you vulnerable; this is known as an IP leak. You probably won't even know it's happened.
That's where the kill switch comes in. It ensures that if you lose the VPN then either your internet connection is shut down or the apps that use it are. Essentially, if you're not connecting over the VPN, you're not connecting at all.
Some VPN connection apps actually have an integrated kill switch. We recommend that you use it, so be sure to enable it in the settings if you haven’t already.
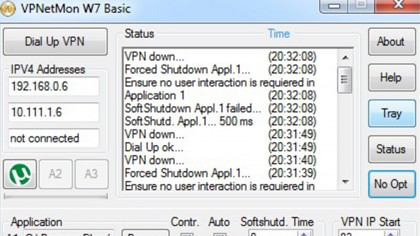
The alternative is a software kill switch, which can be added to any VPN. These apps, such as VPN Watcher and VPNetMon, are configured in Windows to instantly close selected apps if the VPN dies and restart them if it goes up again.
To set up VPNetMon, follow these steps:
1. Connect to your VPN.
2. Start the app and click on Opt.
3. On the left, it should show two IP addresses: your local IP address (on top), and your VPN IP address (second). In the field where it says VPN IP Start, enter the first number of your VPN IP address; for example, if it's 10.1.1.68, then type in 10. This is how it detects if you're connected.
4. Next to A1, click Browse and find an app you'd like it to control, for example utorrent.exe. If you check the Control box it will automatically shut it down if your VPN goes offline. If you check Auto, it will restart it when the VPN comes back on.
Enabling a network lock
In the same vein as a kill switch, enabling your network lock is another quick and easy way to help ensure your connection is secure in case your WiFi gets interrupted.
In the event of VPN interference, the network lock will automatically prevent your device from accessing the internet. That means your information is able to remain protected while your VPN reconfigures itself.
By keeping your network – whether it be your mobile or desktop – under lock and key, you won’t have to worry about your IP being exposed. It’s a useful feature to have. That said, not every VPN provider offers it.
Preventing DNS leaks

DNS, which stands for Domain Net Server, is the service that your computer uses to translate URLs such as techradar.com into an IP address, 185.113.25.59.
When you're connected to a VPN you should automatically be using the secure DNS server provided by the VPN service. Except sometimes you don't; sometimes your computer might use its regular DNS connection, bypassing the VPN. That's called a DNS leak, and it could be monitored by outside forces.
Some VPN clients have DNS leak protection built in, but if yours doesn't you can run a test here. The location it tells you should be your 'apparent' VPN location, not your actual one. If it fails, then there are suggestions on the site that provide a fix.
Blocking IPv6 leaks
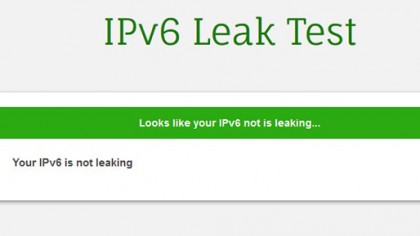
For most internet activity, we use the good old version 4 of the internet protocol; you know, the one with the four-number IP addresses. The thing is, there's actually a version 6 of the protocol as well, which is designed to provide a lot more internet addresses than IPv4. Internet providers are still transitioning from IPv4 to IPv6, although your computer supports both.
IPv6 operates outside of the VPN, and an attacker might use it to figure out who you are. It's not something that's done often, but it is possible, and the only real fix is to disable IPv6. Some VPN clients have the ability to do this built in, but if you want to do it manually there's a quick guide here. There's also an official Microsoft guide (with apps).
Some VPN companies have started rolling out their own applications to give users more control over their privacy. ExpressVPN, for instance, offers free-to-use leak testing tools to help keep your connection secure. Alternatively, if you just want to check if your system is leaking, you can also visit this website and run a test while you're connected to the VPN.
Stopping WebRTC leaks
And on the topic of leaks, it’s also important to make sure your network isn’t unwittingly exposing your address. WebRTC (Web Real-Time Communication) is a common protocol that allows two devices to quickly communicate with each other by broadcasting each other’s IP address.
Unfortunately, by doing so it also sometimes shares a user’s location unknowingly. Because WebRTC leaks are related to your browser and not specific applications, the flaw can actually detect and broadcast your real IP address even when you’re using a VPN.
An easy way to test for WebRTC leaks is to check your IP address before and after you connect to a VPN. You can use a simple IP tester like this one to note your address before you connect to a VPN server and after. Your address should change depending on which VPN connection you’re using. If it doesn’t, then it might be a sign that your browser is leaking your location.
Many VPNs have started offering their own dedicated WebRTC leak protection, but you can also use free ad blockers like uBlock Origin to manually block any and all local WebRTC leaks.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!