
The TCP/IP protocol, which underlies everything that we do on the internet, was designed when robustness rather than security was the priority.
But while it means that traffic always arrives at the right destination, assumptions and bugs in the way TCP/IP has been implemented and in the application software to which it delivers data mean that we all have to be prepared for attack when going online.
Hackers are constantly trying to discover new ways to connect to machines so that they can install backdoors for later re-entry, trojans to collect financial details and the inevitable botnet clients. Whatever their goal, the starting point is the same: the port.
This guide will help you to understand how they work, how they can be used maliciously and how to close unwanted ports to keep you safer.
In the beginning
What we now think of as the internet began in the late 1960s with the US Defense Advanced Research Agency's ARPANET. Central to its design was the idea of 'packets' of data that could be sent at will between networked computers.
These packets were sent by being passed (or 'switched') from machine to machine along a network of connections, gradually getting nearer their destination. Computers known as Interface Message Processors (IMPs) decided how to switch the packets at each network junction. Today, we call these devices routers.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Unlike telephone systems, which at the time used a single physical line to host a single conversation at a time, packet switching networks sent multiple packets of information destined for different destinations down the same line, one after the other, making them vastly more efficient.
If one part of the network was unreachable, the IMPs could decide to route a packet around the damage so that it could still reach its proper destination.
As the benefits of networking computers became apparent in the early 1970s, the number of different networking protocols in use started to become a serious bottleneck.
The big breakthrough for the internet as we now know it came in 1973, when researchers Vint Cerf and Robert E Kahn realised that by having each host computer use a common protocol, any machine could send and receive packets of data to and from any other, regardless of the physical network used.
Suddenly, any network using Cerf and Kahn's TCP/IP (which stands for Transmission Control Protocol/Internet working Protocol) system could talk to any other network easily and reliably. All each manufacturer needed to do was program the protocol into its operating system.
How TCP/IP works
Depending on the data being carried, packets are sent not only to a destination computer, but also to a specific software 'port'. Each port handles different application traffic.
Port 80, for example, handles normal HTTP web traffic, while port 443 handles HTTPS encrypted web traffic. Sending email is always done over port 25, while receiving it is completed over port 110.
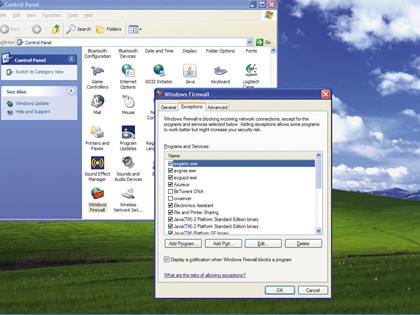
CLOSE THEM OFF: Closing the ports you don't need is a good place to start on the road to a secure PC
The TCP/IP system running on the internet today uses a series of handshakes to ensure that data always gets through to the correct machine, and that when it doesn't, the loss can be easily rectified. When your computer sends a packet, the following happens.
First, your computer sends the destination computer a packet containing its address, the address of the machine that it's connecting to and the number of the port to which it wants to connect. This is called a SYN packet, which is short for synchronisation. The packet also contains a random number that's known as the sequence number.
If the software on the receiving port accepts the connection, it sends back a packet called a SYN-ACK packet, short for synchronisation acknowledgement. This packet also contains a random sequence number. Your PC then sends an ACK (which is short for acknowledgement) packet back to the server. This technique is called the 'handshake'.
Once a connection is established, data transmission can begin. The packets sent by your computer are tagged with the sequence number it used when it began contacting the destination machine. Your computer includes and increments this number in each packet sent.
The combination of the source and destination IP address, the port number and the incrementing sequence ensures that all packets are uniquely identifiable.
For each packet you send, the destination computer returns a receipt packet to say that it got there safely. If a receipt doesn't arrive after a timeout, that's the cue to resend.