Twitter 'onmouseover' security flaw hits site
Sophos tells users to use third-party apps
UPDATE: Twitter has announced it has fixed the security flaw, explaining on its Twitter Status blog: "The exploit is fully patched."
Twitter is blaming the hack on an XSS (cross-site scripting) attack.
ORIGINAL STORY
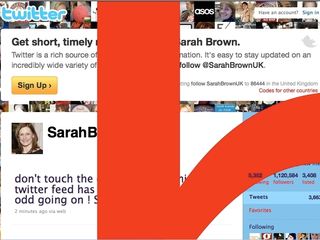
A security flaw has appeared on micro-blogging site Twitter, which allows third-party sites to open up in your browser when you simply hover your mouse pointer over a link.
The hack has targeted thousands of profiles and even redirected readers of Sarah Brown's Twitter feed to a Japanese porn site.
Mouse in the house
Security firm Sophos has outlined the potential problems with the flaw, which uses a piece of Javascript code – called onMouseOver – that allows you to be redirected to another site without even clicking on a link.
Get daily insight, inspiration and deals in your inbox
Get the hottest deals available in your inbox plus news, reviews, opinion, analysis and more from the TechRadar team.
Although Sophos believes that the flaw is "innocuous" at the moment, it is recommending all users to use a third-party client to access Twitter and not go directly to the main site until the Javascript code has been blocked.
If you are using the site, then it is recommended you don't click any link with the 'onmouseover' command, or ones which contain blocks of colour (rainbow tweets) as these can hide their true content.
Go to www.sophos.com/blogs for more details.
If you are stuck on which third-party app to use, don't worry as TechRadar has compiled two lists: six of the best Twitter web apps and the 12 best Twitter apps to help you make a decision.
Here SophosLabs has created a video to explain the situation:
Marc Chacksfield is the Editor In Chief, Shortlist.com at DC Thomson. He started out life as a movie writer for numerous (now defunct) magazines and soon found himself online - editing a gaggle of gadget sites, including TechRadar, Digital Camera World and Tom's Guide UK. At Shortlist you'll find him mostly writing about movies and tech, so no change there then.
Most Popular




