Nanny's little helpers
The technology used to censor content and spy on users is rarely home-grown. In 2006, Reporters Sans Frontieres (RSF) provided the US House of Representatives' Committee on International Relations with a list of US firms that either provided censorship tools to other nations or actively censored content.
According to RSF, Yahoo has censored its Chinese search results since 2002 and also helped the Chinese police identify and jail at least one journalist and one dissident who criticised human rights abuses.
MSN censors the Chinese version of MSN Spaces, Google censors its search results in China, Secure Computing has sold censorship technology to Tunisia, and Fortinet has sold the same kind of software to Burma. Most seriously of all, RSF alleges that Cisco Systems has marketed equipment "specifically designed to make it easier for the Chinese police to carry out surveillance of electronic communications".
RSF also alleges that Cisco is suspected of giving Chinese engineers training in how to use its products to censor the internet. Cisco strenuously denies the allegations, but as the US Council for Foreign Relations reported back in early 2008, "China relied on two US companies – Cisco Systems and Juniper Networks – to help carry out its network upgrade, known as CN2, in 2004. This upgrade significantly increased China's ability to monitor internet usage [although] Cisco has denied charges it adapted its equipment."
The truth is that hardware and software designed to block genuine problems – illegal pornography, viruses, worms and hacking attacks, for example – is often just as effective at blocking legitimate sites or scanning legitimate traffic. As always, technology itself is neither a force for good nor a force for evil: it all depends on who's using it.
Fighting back
Get daily insight, inspiration and deals in your inbox
Get the hottest deals available in your inbox plus news, reviews, opinion, analysis and more from the TechRadar team.
Technology can censor internet use, but it can be used to evade censorship and surveillance too. Picidae turns websites into images, enabling you to read and click links without worrying about your browsing history being recorded or pages scanned for keywords.
Another example is Freegate, which uses proxy servers to reroute traffic and bypass censorship. Then there's Tor. Tor takes your internet requests and routes them through virtual tunnels, making it impossible for traffic analysts to see what you're connecting to (or to trace you from server logs).
Through add-ons such as the Tor button plug-in for Firefox it can anonymise browsing (although for full security you should disable plug-ins such as Flash, QuickTime and so on). While doing a sterling job at hiding what you're looking at, it doesn't protect against tracking cookies and it doesn't encrypt communications – so if you send somebody an email its content can still be intercepted by third parties.
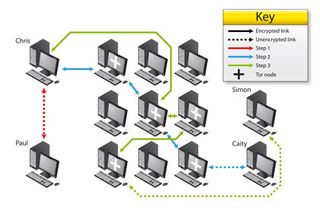
THE ONION ROUTER: Tor can help minimise your exposure by encrypting your browsing, but it isn't a silver bullet – and it can be compromised
Current page: Who is colluding with the censors?
Prev Page Blocking sites and controlling internet access Next Page Internet censorship in the UKMost Popular

