How Windows protects your PC
Your Windows computer should, if you're sensible, already have formidable defences in the form of advanced anti-malware.
However, we're now entering an age of cloud computing, filled with downloadable applets, at a time when we're also fighting an intense arms race against ever more ingenious malware writers.
Because of this, your PC's defences have to handle code from many sources and still protect you from outside threats.
How is this possible, and what ways have the bad guys already found to thwart these efforts? Most importantly, how can you be sure your computer only runs what you think it's running?
Signing in
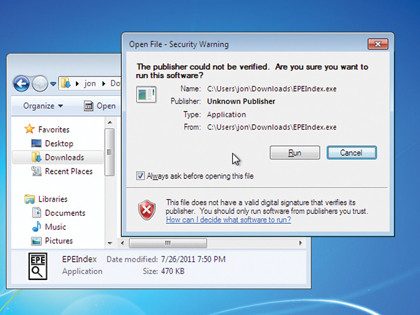
Unlike applications purchased from trusted vendors, when you download applets or freeware made by individuals, there's no way the average user (or even the security professional) can be sure that the software they think is running isn't actually something else entirely.
With the arms race between developers and hackers now gathering pace, it could take more than just advanced antivirus software to match the state of the art in malicious programming. Luckily, Windows has an ingenious way to protect itself. This is Microsoft's Authenticode system.
You'll have seen evidence of Authenticode in action when you try to install software that hasn't been through a process known as signing. A warning popup appears, explaining that the installation program's publisher could not be verified and offering you a chance to stop it running.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Unique signature
Programs are signed using an encryption algorithm like RSA. This uses a publicly available encryption key to create a globally unique signature code that describes the program being verified. Being public, anyone can get the key used to sign the code.
The operating system obtains it, generates its own copy of the signature and compares it with the one supplied with the program. If they match, the code is what the supplier says it is, and it can be allowed to run.
These encryption keys are held by several large and trusted security companies (certificate authorities) in the form of publicly accessible digital certificates that contain the details of the company that issued the program your operating system is trying to verify, as well as the unique signature of the program itself.
If you're a developer, having a certification authority generate a digital certificate to show that you and your code can be trusted is usually a costly and involved process. Obtaining a commercial certificate for your company means proving beyond any doubt that you are who you claim to be.
According to Microsoft, your physical presence may be requested as a representative of your business to verify your identity against photo ID. The business itself must also have a suitable Dun and Bradstreet rating. This rating is a measure of your company's financial stability and indicates that among other things that the company is still in business. This prevents hackers from simply posing as a company that has quietly stopped trading in order to gain a false certificate for malicious purposes.
Finally, applicants must also pledge not to distribute malware. Whether this final measure is any more than lip service is up for debate.
Individual developers can also obtain a personal certificate to sign their products. In this case, no Dun and Bradstreet rating is required, but your credentials will be checked against consumer databases to make sure you are who you say you are. In both cases, obtaining a certificate will usually cost you a fair amount of money.
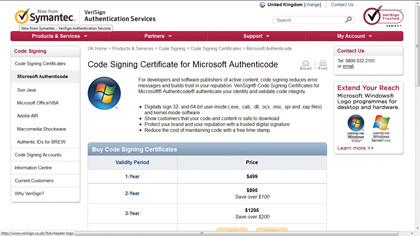
With so many certificate authorities, it pays to shop around for the best deal. A one-year Microsoft Authenticode certificate from VeriSign, for example, will cost you $499 (about £250). If you expect people to download and install your software beyond one year, you'll have to renew the certificate or your code will become unsigned again.
Public keys
Eagle-eyed readers might have spotted that the use of public keys is the same general mechanism used in encrypting email and SSH, where it's used to prove that the server to which you're trying to make a secure, encrypted connection is the real thing and not a dummy that's been set up to skim usernames and passwords.
The main problem with signing code is that the average user has no idea what the associated popup means when the code's publisher cannot be verified. There's a tendency to take a chance on becoming infected and to leave everything to the antivirus software, but what if this fails to spot malicious code?