How to make yourself hack-proof
How to ensure you're always protected
How to make yourself hack-proof

That's it. You've finally heard enough hacking horror stories – even been involved in one yourself – to finally commit to actually doing something to protect yourself against them.
We're not gonna lie – you're probably going to be a little inconvenienced. And yes, you'll have to stop opening every email attachment that drops into your inbox, not download any app that takes your fancy and stop oversharing on social media.
Still, it's absolutely worth it to take the time. Just ask anyone who has ever lost their entire video and photo collection, had their credit card information jacked or been the victim of an online scam – you'll bet they wished they had taken some reasonable steps.
So, without further ado, we'll look at our top five techniques for avoiding the worst.
1. Security software
It's fair to say that Windows has become a lot better at protecting your stuff. Microsoft has made significant strides when it comes to security, and Apple has improved as well. But that's not to say the that the default tools you get are good – but it's getting close to "acceptable."
Still, if you want to be best protected, you do really need to install extra software on your system. That extra software starts with an anti-malware solution – possibly as part of a packaged suite. Check out this guide to the best anti-virus software of 2015.
Windows 7 does not come with anti-virus at all, so installation is a must. You can get Microsoft Security Essentials for free – but you're actually better off with one of the third party tools available. Anti-virus test results have shown that Security Essentials is still a ways off the best anti-virus tools available.
In Windows 8, Microsoft folded Security Essentials into the base package (it's part of Windows Defender), but it's still using the same engine, so it's still best to install a third-party tool.
2. VPNs
If you're like most people, you probably know VPNs as the services that let you spoof your internet address to foil geoblocking. And they are pretty good at that: they let you watch the US versions of Netflix, Amazon Prime and Hulu or the UK's BBC iPlayer in spite of those companies not really wanting you to.
But they have a very important security function as well. Several, in fact. With a VPN, the only site you make a connection to is the VPN provider, and that connection is protected by heavy encryption. The VPN provider then relays your connection to the end sites you want to visit. This has a number of beneficial effects:
1. Your ISP (and by extension, the government) has no way of tracking which web sites you visit, barring a subpoena of the VPN providers records – and it's likely that a) the VPN provider is outside their jurisdiction and b) doesn't keep records anyway. The only connection that your ISP and anybody else monitoring your internet link can see is the one between you and the VPN provider. All other connections are obscured.
2. Web sites you visit have no way of tracking your IP address or figuring out who you are unless you explicitly tell them. All your connections appear to come from the VPN provider and cannot be traced back to you, thus making you completely anonymous. This is how VPNs bypass geo-blocking – they make your IP address appear to be one in the authorised country. It also prevents tracking on other internet services like BitTorrent: if you download something from BitTorrent while connected to a VPN, there's no easy way that the download can be traced back to you.
3. Your data cannot be intercepted and read locally. This is an important one that people often forget. The data link ("tunnel") between you and the VPN provider is encrypted, so nobody can intercept and read your data en-route. That doesn't just defeat most government spying: it's critically important if you use public WiFi hotspots.
VPNs: WiFi

Thanks to the way that WiFi works, it's very easy for someone on the same WiFi network as you to intercept and read the data you're sending over the internet, grabbing your emails, IMs and any other unencrypted data. Normally, WiFi data is encrypted so that somebody outside the network can't listen in, but if someone is on the same WiFi network as you (as is the case in a public hotspot), they have that decryption key and can listen in. A VPN encrypts all your traffic, so that anybody listening in gets nothing but jibberish.
VPNs: Setting one up
Setting up a VPN is easier than ever. There are a host of VPN providers operating around the world: Tor, Hide My Ass, and ExpressVPN are among dozens – hundreds – of VPN services operating worldwide. Most charge between US$5 and US$10 per month, and may or may not have data volume restrictions.
Nearly all of those providers supply an app you can install and run on a PC that connects you to their VPN. Many also provide mobile apps so you can extend that security to your iOS and Android phone as well (yep, mobiles need VPN security too). More sophisticated users can potentially set up their routers to push all data on a home network through the VPN, though that is a more technical task.
3. Password managers

Do you need to have roughly a million passwords for all the sites you visit and apps you use? It's 2015: of course you do. And is each one a unique combination of random letters and numbers? Pretty unlikely – you're only human after all.
The truth is that most passwords used by regular people can be cracked in a matter of minutes using a "dictionary attack" – simply trying out a bunch of common words and phrases with an automated tool. A random alphanumeric password (something like "s7Hnd3Fa4") will fool this, but we humans are not good at remembering those. Maybe we can remember one or two, but a different one for every site? Nope.
Which is why a password manager is an absolute must. It remembers passwords for you, letting you use a unique combination of letters and numbers for each site and WiFi network. You only have to remember a master password to access all of them.
3. Password managers: LastPass

When it comes to password managers, we just love LastPass, a cloud based tool that's free for PC platforms but does require a Premium subscription for US$12 per year for access on mobiles. It's available for Windows, Mac, Linux and all the major mobile platforms. Because it's cloud-based, it lets you share your passwords across your devices.
While the company recently experienced a hacking of their servers, all encrypted information (other than possibly a users master passwords) were protected, demonstrating how secure and reliable the service truly is.
Installing LastPass will add a widget to your browsers and (optionally) import all the passwords stored in your browser password caches. From then on, any time you visit a site with a password a LastPass icon will appear in the username/password fields and you can click on it to choose which password you will use.
In addition to remembering your passwords and sharing them across multiple platforms, LastPass has several features that you really should be using. The first is the password generator.
When you create an account on a web site, a little icon will appear in the password field. Click on it to bring up the password generator (you can also access this via the LastPass widget). This will generate a secure and unique password for the site which LastPass will remember for you.
The second thing you should do is set up two-factor authentication. Click on the LastPass widget and go to My Secure Vault – this is a web page where you can view and edit all your saved passwords. Then click on Settings, then Multifactor Options.
It's here that you can add an extra level of authentication for LastPass. We really like using it with Google Authenticator for mobiles – whenever someone tries to log into LastPass, your mobile will get an authentication message that you have to confirm before proceeding.
LastPass may seem like a bit of an inconvenience at first, but you'll get used to it very quickly – and likely appreciate its capacity to share your passwords across devices.
4. Mobile security

It's not just your PC that needs some security lovin'. Mobiles are often just as vulnerable as PCs. In addition to being subject to viruses the same way PCs are, mobiles can have dodgy tracking and identity stealing apps installed, and can be easily lost or stolen, giving whoever gets them access to all your stuff.
4. Mobile security: Android
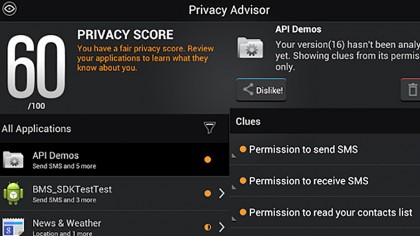
An anti-virus security app for your Android mobile is a good start. There are a bunch of them available for free, including solutions from Trend Micro, AVG, BitDefender, Avast, McAfee, Norton (Symantec), Kaspersky, Lookout and ESET. All of those offer good solutions, including anti-virus and anti-theft.
For Android at the moment we're rather partial to BitDefender Mobile Security & Antivirus thanks to its cloud-based app analyser. Like most Android security tools it comes with a virus scanner and anti-theft device locater/locker that allows you to locate and/or lock your device through a Web service should you ever lose it.
But it also comes with an app locker that will require your phone pin before selected apps will start, and an app permission analyser that checks your existing installed apps for shaky privacy practices.
It doesn't just rely on Google permissions (you know, that list of access permissions that pops up when you install a new app, which you never actually check and just approve automatically) – it checks the app against a cloud database.
Avast is another favourite if you're not a fan of BitDefender. In addition to the anti-malware and theft and recovery tools, it includes a backup solution as well as a firewall – though the latter is available only on rooted phones.
Installing an anti-virus solution is a good start, but it's not the final solution for Android. Some other things you should look at include:
- Lock your lock screen. Head to Settings->Security and tap on Screen Lock. Choose the Pin, Pattern or Password lock options (or Fingerprint if you have it). We particularly like Pattern for the convenience.
- Encrypt your mobile. In the security settings, tap on the Encryption option and follow the prompts. It will take a while, but when it's done nobody will be able to access data on the device without going through the unlock process.
- Use secure messaging apps. TextSecure and RedPhone (both from Open Whisper Systems, and available on Google Play) are phenomenal tools for secure text and voice communications between Android users. They provide end-to-end encryption of your communications, with nobody but you and the recipient being able to read or listen in – unlike regular SMS and voice, which are easily intercepted. WhatsApp recently began using the TextSecure protocol on Android, so that's pretty great for private conversations as well (it doesn't offer it for iOS devices, however).
4. Mobile security: iOS

iOS users have fewer security tools available to them, but it's fair to say that they have less to worry about. The closed nature of the Apple ecosystem has been pretty effective at keeping viruses out.
Still, there are some things worth looking at. While Apple provides its own backup and location tools with iCloud, you're better off using Lookout, available on the iTunes App store. It provides lost and stolen phone tracking and locking, local backup and a system advisor and process scanner that checks currently running apps for anything malicious.
One other important thing to do is enable the Passcode lock screen. If you have an iPhone 5s, you can also enable Touch ID, a fingerprint scanner. Head to Settings->Passcode and Touch ID and enable them.
5. Downloads

If you've been using computers for more than, say, five minutes, you've probably downloaded some shady stuff – and paid for it with a nasty virus infection or rootkit. Any executable file you download can potentially be bundled with a virus. So you need to be a little vigilant about what you download.
5. Downloads: App stores

One of the great things about mobiles is that they come by default with curated app stores. Apps on Google Play and iTunes App Store are pre-checked for viruses and are generally safe to download.
There have been a few nasties that have slipped through on Google Play in the past, but nothing for some time. Sure, some apps with awful privacy may be on there, but they're not actually viruses.
If you're on a mobile, you should pretty much stick to always downloading from the App Store and Google Play. On iOS devices you have no choice (sans jailbreaking), but even on Android it's generally a good idea to have the "unknown sources" option in the security settings unchecked.
On Windows, unfortunately, we generally don't have that option. There is the Windows Store, but right now it only provides a very limited array of Modern UI (Windows 8) apps. When Windows 10 comes out, that policy is set to change and hopefully we'll be able to get a full array of Desktop apps as well – but we'll have to wait and see. For games, there's also Steam.
5. Downloads: Get apps from the source
When downloading PC apps, you should always endeavour to get them from the software maker's own web site, and not from a third party download site. Some third party download sites do make an effort to scan for viruses, but not all sites can be trusted.
5. Downloads: Scan before opening
When you download an app, you should give it a quick virus scan before opening it. Most anti-virus solutions add a right click context menu item to Windows Explorer/File Explorer with an option to scan a file for viruses. While in theory the AV tool should automatically scan any downloaded files, give it a run anyway.
5. Downloads: Read the comments
Okay, you're committed to getting an app from a peer to peer network. We can't stop you. But at least read the user comments on the BitTorrent site you're grabbing it from before downloading. If there's a virus embedded in the file, it's possible that someone may have spotted it and left a comment to that effect.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!