Smashing up a 3D printed ghost gun won't be enough to prevent CSIs from retrieving data for forensic analysis - here's why
Destroyed 3D printed objects may still hold traceable forensic information
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- Ghost guns highlight the darker side of modern 3D printing technology
- Fingerprinting systems can embed timestamps, geolocations, and printer identification data
- SIDE offers break-resilient embedding methods for forensic data recovery
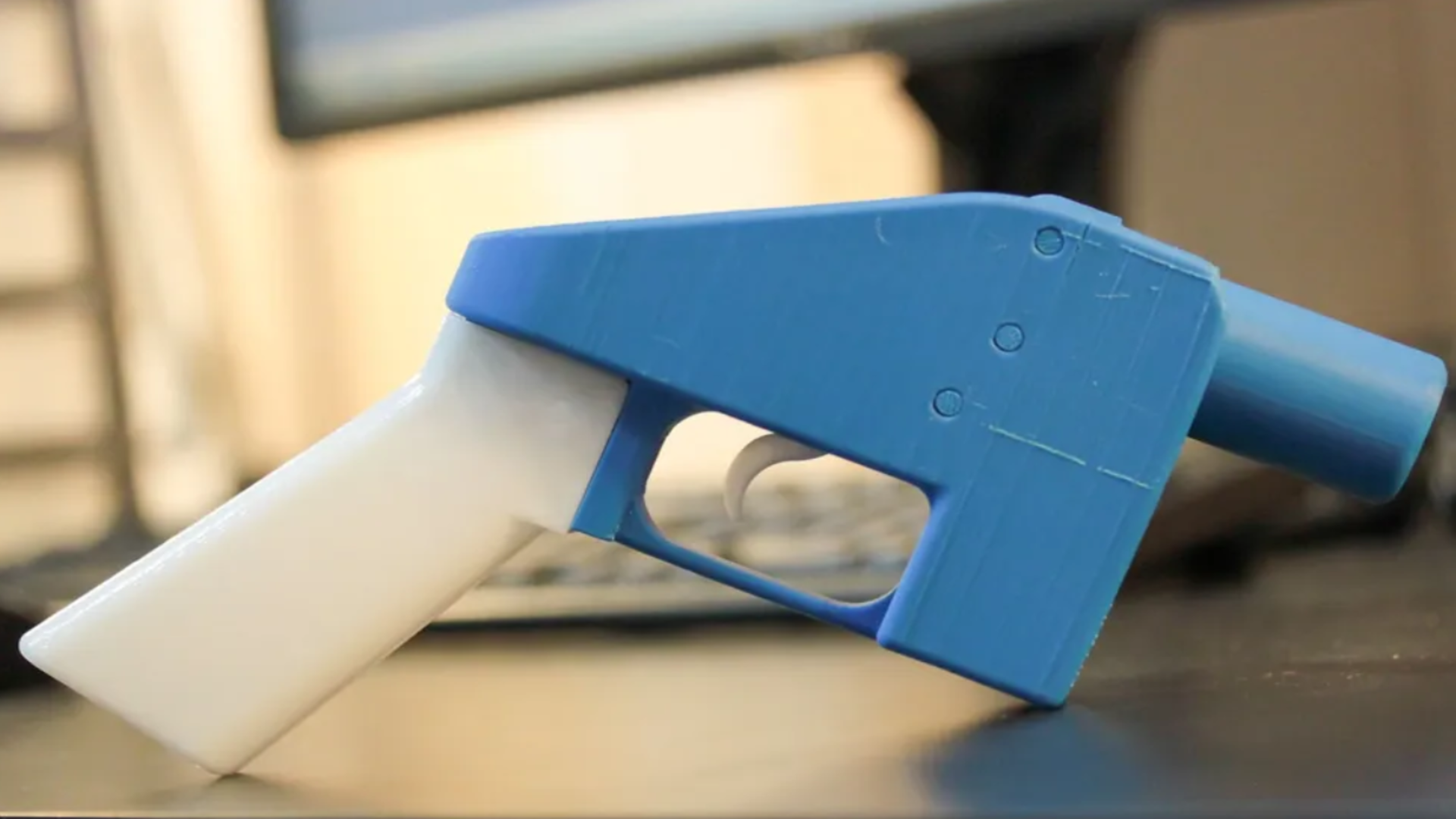
The rise of 3D printing has offered new ways to produce tools, spare parts, and even art. Yet its darker use has gained attention through “ghost guns.”
These are firearms produced outside regulatory systems, which are difficult to trace and have already been implicated in violent crime, including the 2024 killing of UnitedHealthcare CEO Brian Thompson.
Thankfully, researchers now believe that even if someone smashes such an object, investigators could still recover valuable forensic information.
Building a system of hidden fingerprints
The idea of fingerprinting in 3D printing is not entirely new. Various approaches embed unique information into printed items, often including details like timestamps, printer identification, and geolocation data.
Until now, a weakness has remained: what happens when a printed object is broken into pieces or deliberately tampered with?
A team led by Netanel Raviv at Washington University in St. Louis has developed a system designed to withstand such attempts.
Its framework, named Secure Information Embedding and Extraction (SIDE), uses mathematical methods that allow fragments to retain enough encoded detail for investigators to recover key information.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The SIDE system is built on earlier work presented at the IEEE International Symposium on Information Theory in 2024, which focused on encoding methods resilient enough to reconstruct data from partial remains.
By extending those ideas, the current study adds security mechanisms that can require 3D printers to include such fingerprints automatically.
According to the researchers, SIDE does not just add markings but uses loss-tolerant embedding techniques. This means that even a weapon deliberately broken into pieces may still yield identifiable data during forensic analysis.
On one hand, fingerprinting techniques could make it harder for illicit weapons to circulate undetected.
On the other hand, this raises questions about the scope of surveillance, control over personal manufacturing, and the balance between security and privacy.
A beginner 3D printer used for harmless home projects might soon be subject to the same requirements as industrial machines if regulators decide to mandate such systems.
While the debate will likely focus on ghost guns, SIDE has potential uses far beyond weapon tracing.
Any item produced with a 3D printer could, in theory, carry this invisible signature.
Combined with AI tools for pattern recognition and data recovery, investigators could reconstruct timelines and identities from fragments of plastic or resin.
"This work opens up new ways to protect the public from the harmful aspects of 3D printing through a combination of mathematical contributions and new security mechanisms," said Netanel Raviv, assistant professor of computer science & engineering in the McKelvey School of Engineering at Washington University in St. Louis.
"While SIDE has limitations in defending against resourceful attackers with strong expertise in 3D printing, it raises the level of sophistication, prior knowledge, and expertise required from the adversary to remain undetected after committing the crime."
Via Techxplore
You might also like
- These are the best small business printers to keep your SMB going
- Here are the best printers available
- We've also listed the best business VPNs to use now

Efosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.