How to recover lost Windows passwords
Let us show you how to recover lost Windows passwords

Figuring out how to recover lost Windows passwords can be annoying, but that’s on purpose. If Microsoft made it easy to do, anybody could just get into your computer and access your files and vital information.
The thing is that we all forget stuff, including our passwords, which means that if you forget your Windows one, you’ll have to go through the tedious steps yourself - and even our best password managers wouldn't help. That’s why it’s crucial that you set up your security questions, create a password reset disk, and enable other authentication methods early on. So that when you do forget, you’ll have other ways to sign back in or quickly reset your password.
Whether you’re using Windows 10 or the new Windows 11, you would have chosen between a Microsoft account or a local Windows account. Resetting your lost Windows password would highly depend on the type of account you set up, but we’ll show you how to recover lost Windows passwords in both cases.
How to recover lost Windows passwords: Microsoft account
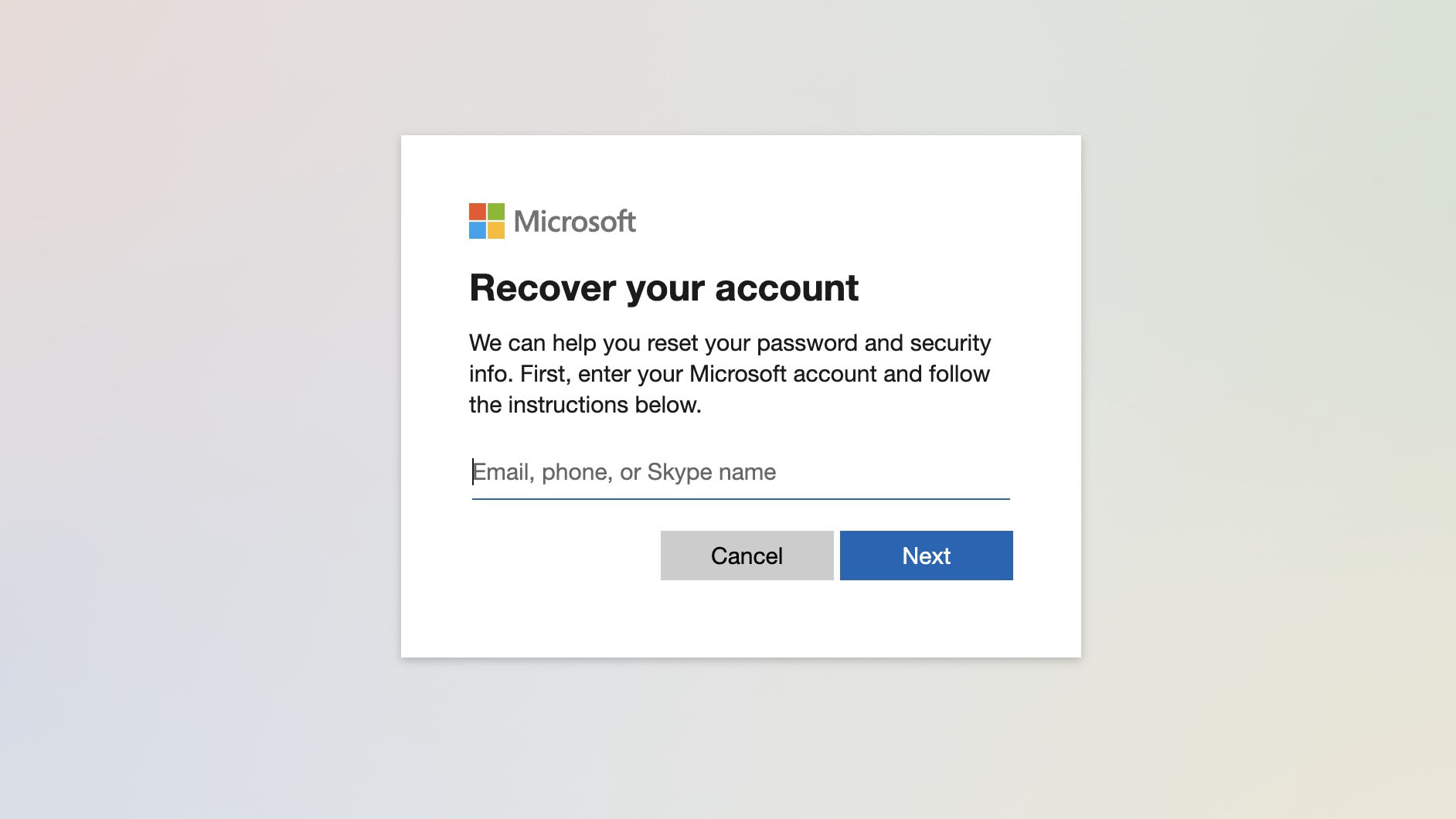
Resetting a lost Microsoft account password can be a bit more tedious than resetting a local account one. If you’re resetting it online, you’ll have to go through several steps and confirm a few details before Microsoft even starts the process of checking whether or not to give you access to the account. And, even when you’ve filled in the forms correctly, you’ll have to wait up to 24 hours to get access so you can reset your password.
If you’re on your computer and you already have either a phone number or a backup email address attached to your Microsoft account, you should try resetting it there first.
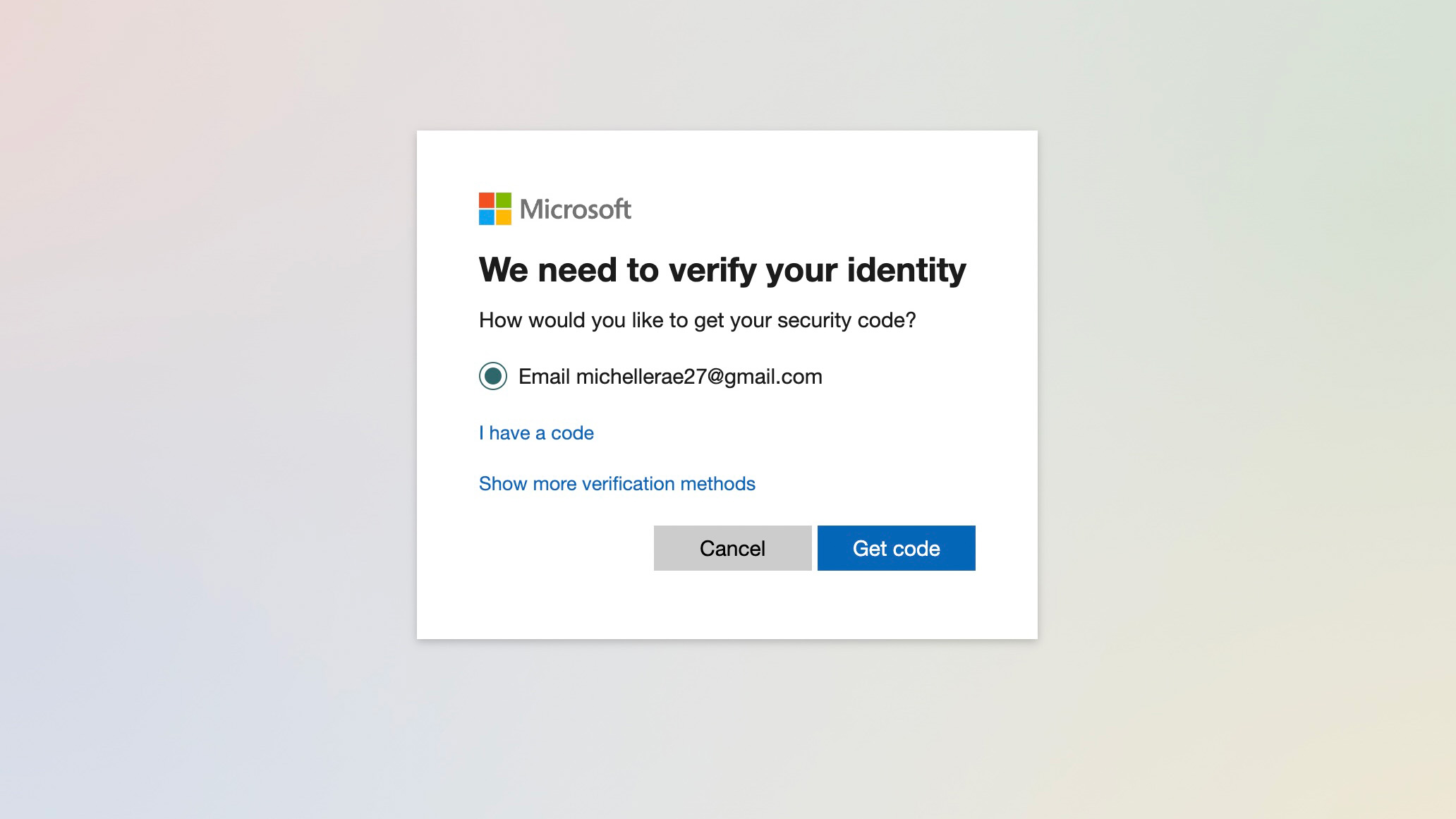
2. If you already have a phone number and/or a backup email attached to your account, Microsoft will try and verify your identity by sending a code to either one. Simply select whether you want it sent to your backup email or the phone number on file, then click 'Get code.'
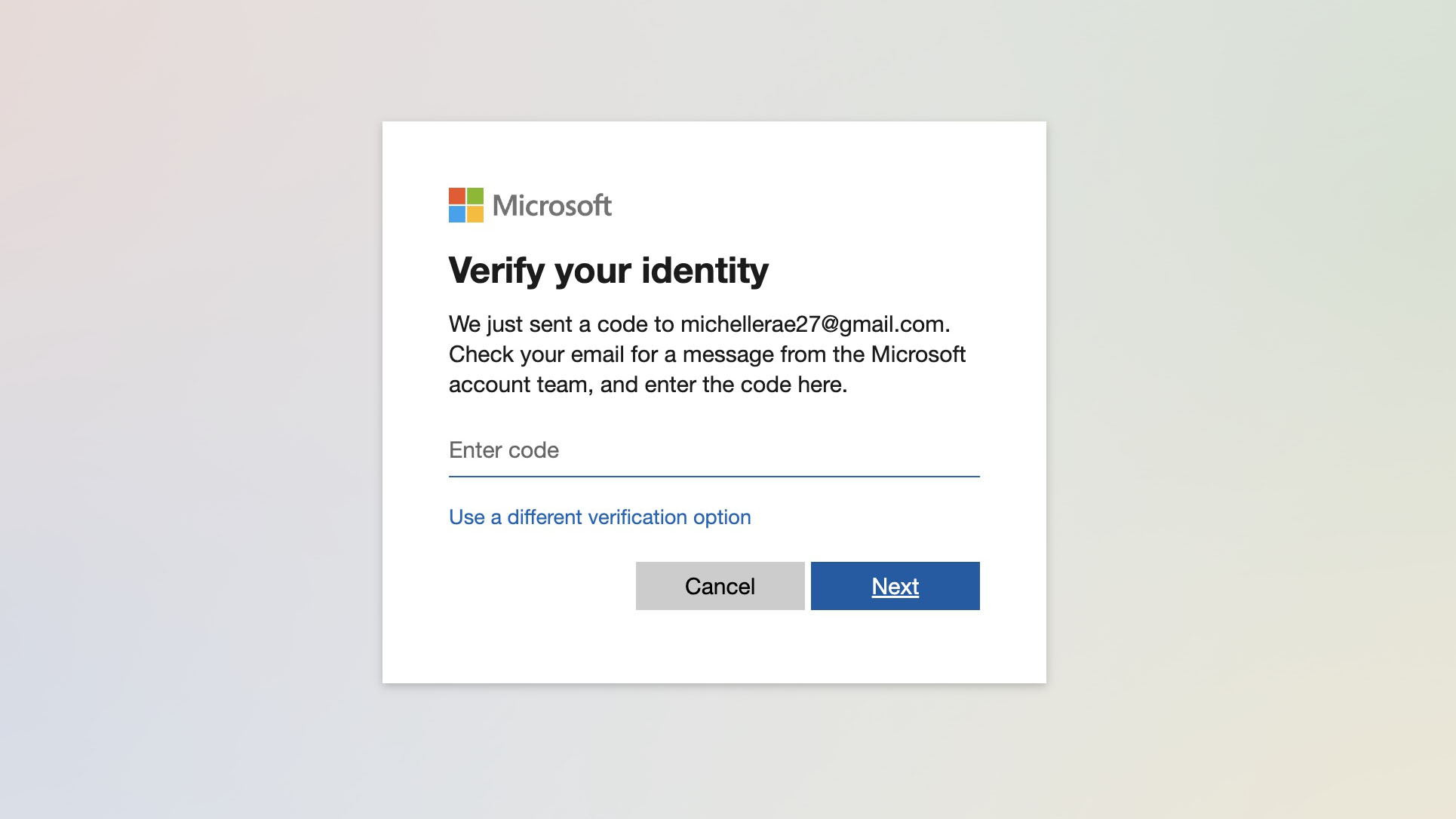
3. You will then be prompted to enter the code. Once you have it, type it in and click 'Next.'
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
4. You can now create a new password.
If you’re doing a password reset online, especially if you no longer have access to your backup email or phone number, you’ll need to use a different PC or laptop.
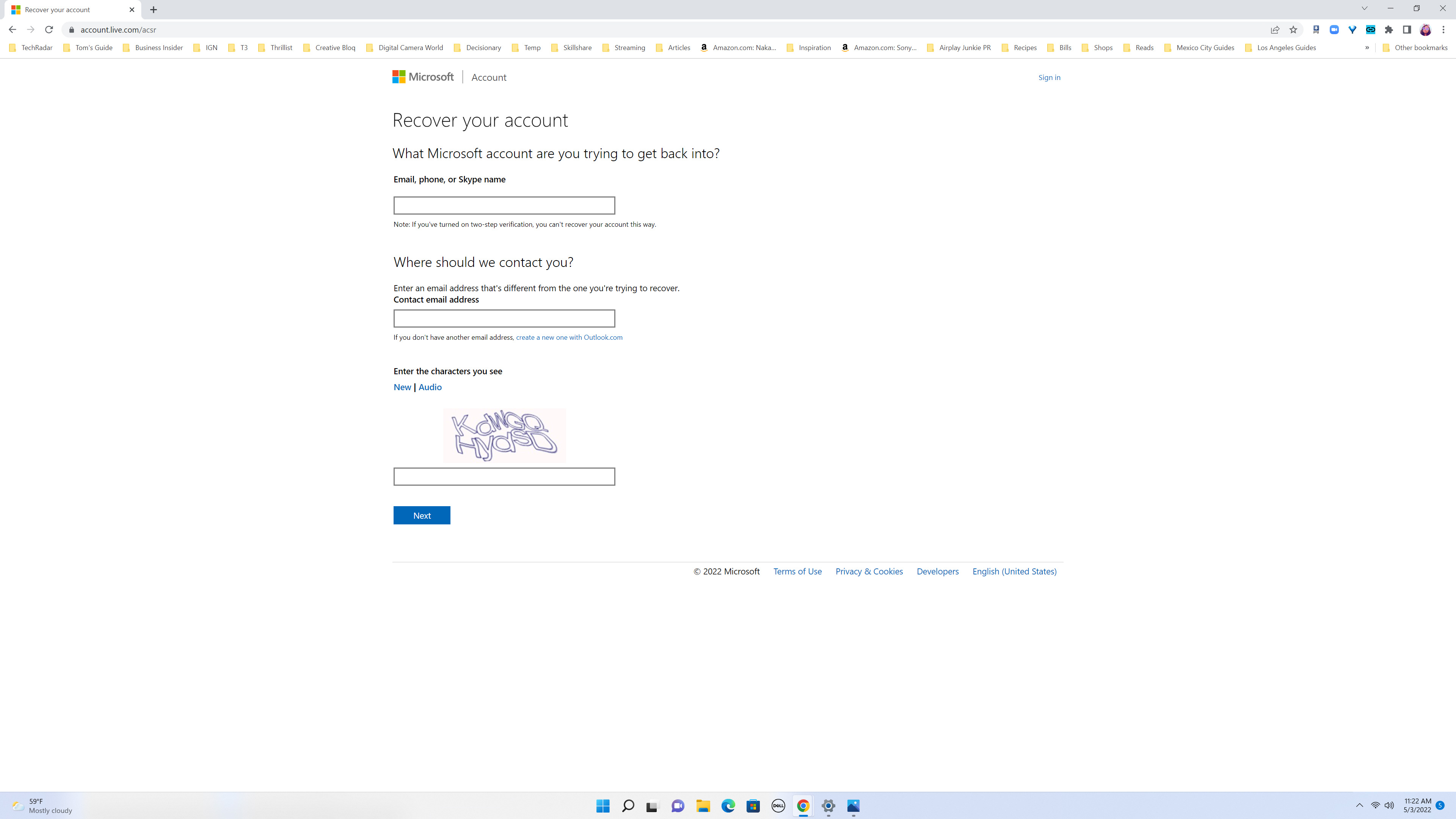
1. Open account.live.com/acsr in a browser. Enter the email address attached to the Microsoft Account whose password you’re trying to recover, a second email address that you have access to and the CAPTCHA characters that you see. Click ‘Next.‘
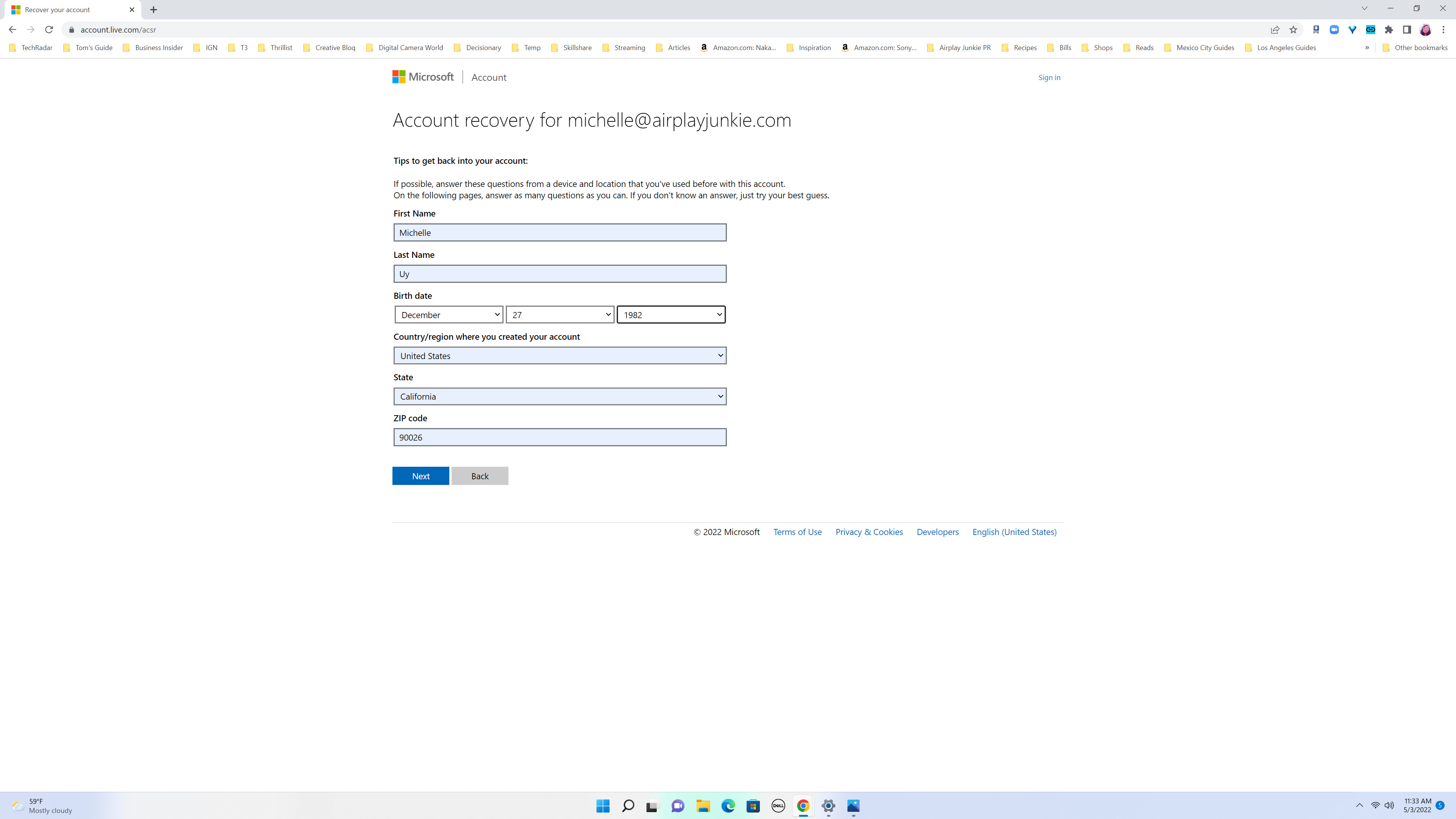
2. From there, Microsoft will ask you to verify a few details to ensure that it’s really you who is accessing the account. The first form will ask you to fill in all your basic information: name, birthday, country, state/region and zip code. Click ‘Next‘ when you’re done.
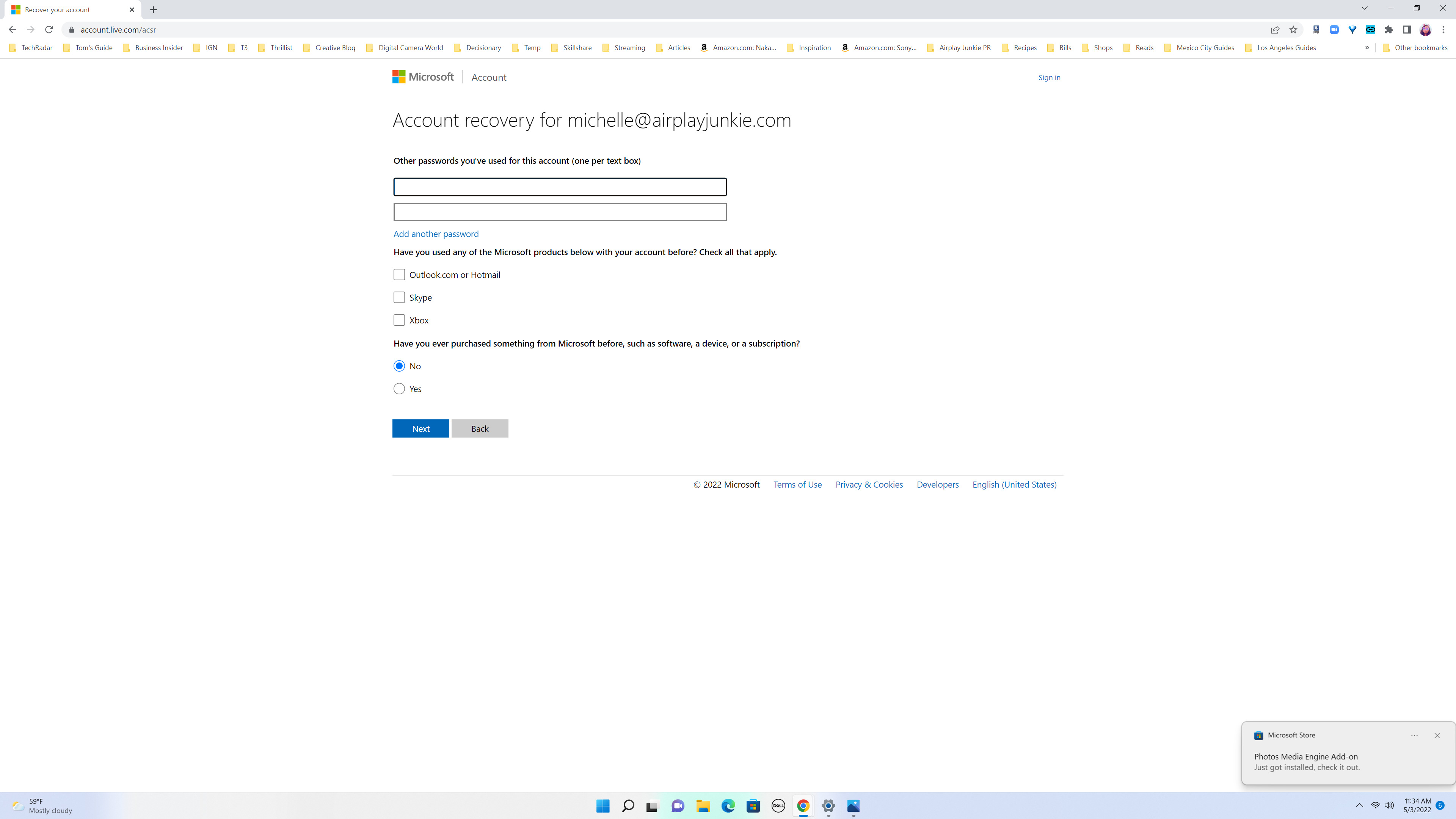
3. The next page will ask you to provide previous passwords you’ve used on the account, verify other Microsoft products you’ve used with the account and whether or not you’ve purchased anything with Microsoft before. Answer these the best you could, then click ‘Next‘.
4. Depending on whether or not you’ve provided enough correct information, you might be taken to another page asking for more details.
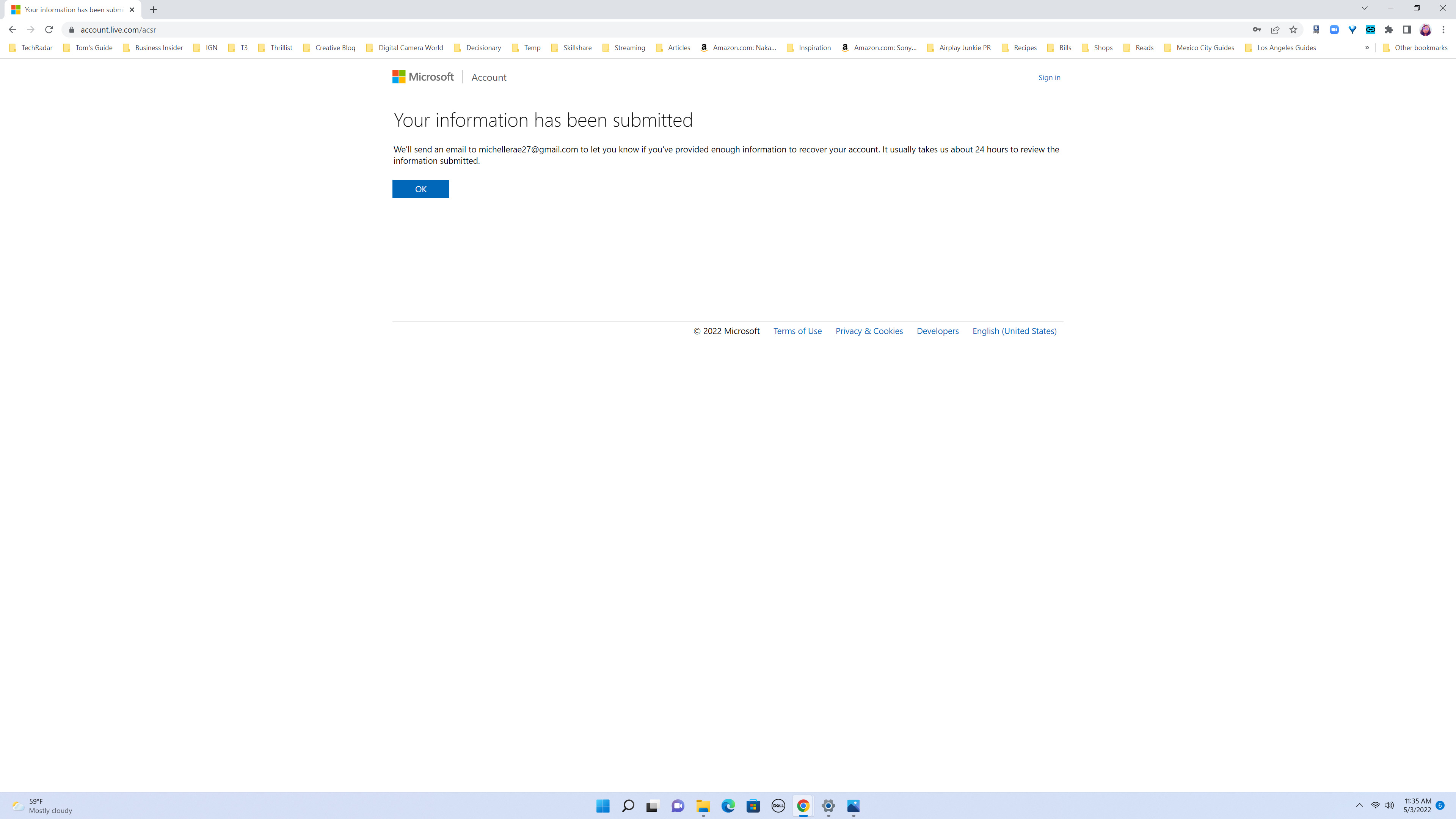
5. Otherwise, you will get a confirmation saying that you will receive an email from Microsoft at that second email address you provided within 24 hours. That email will either give you a link for a password reset page or notify you that Microsoft didn’t get enough information to verify that you are the owner of the account.
6. If you do get the link, simply follow the steps for resetting your password.
How to recover lost Windows passwords: local account
Luckily, Microsoft requires you to create your security questions when you’re setting up a local Windows account. So, as long as you know the answers to those security questions, resetting your local account passwords should be a breeze.
1. At the sign-in screen, click the arrow icon in the password field without typing anything.
2. You’ll then get a notice saying that the password you entered is incorrect. Don’t panic! Just click ‘OK,‘ then click on the link that says ‘Reset password.‘
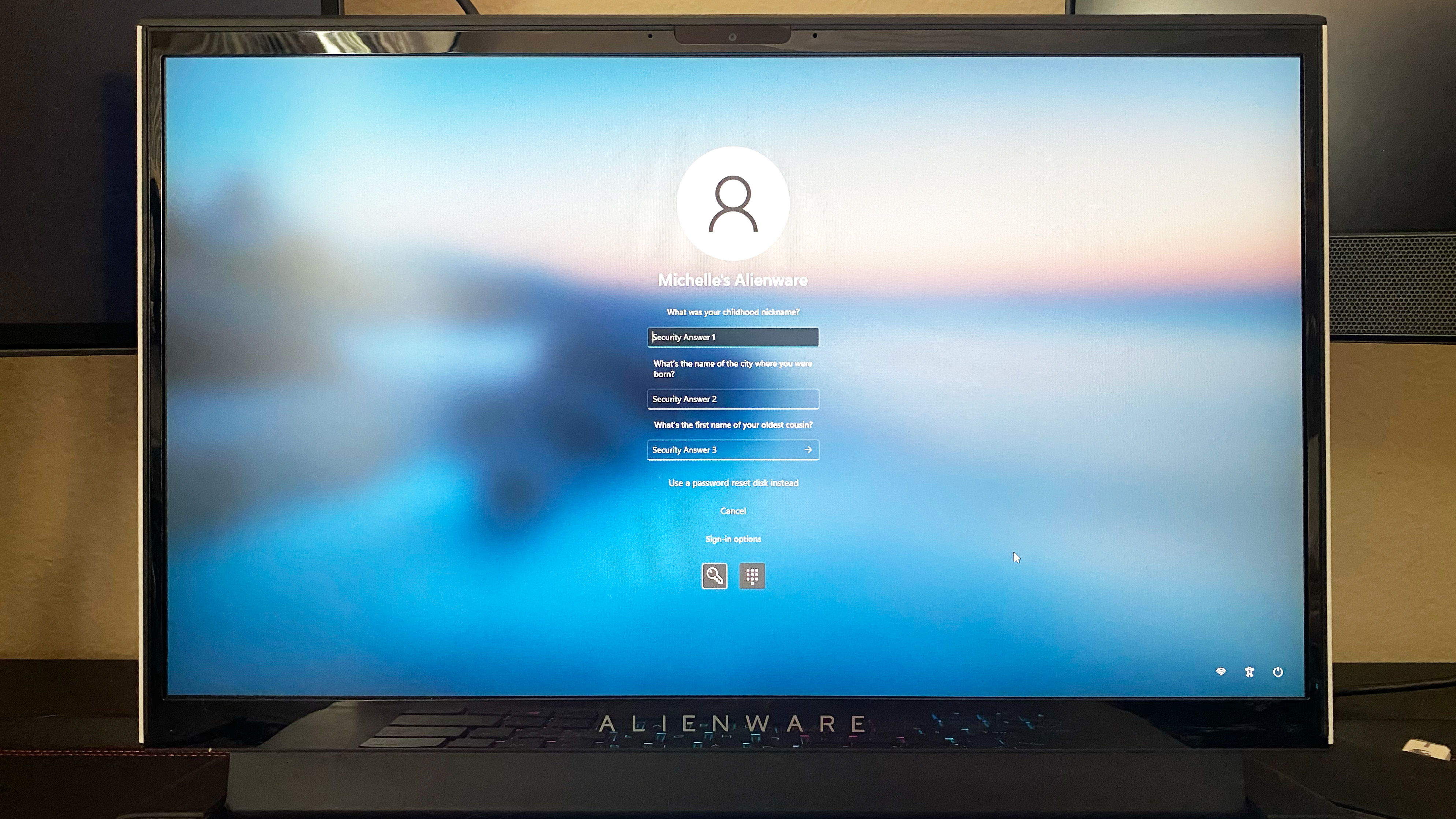
3. You will then be prompted to answer your security questions, typically three of them. Simply type in your answers and click the arrow in the third security answer field.
4. If your answers are correct, you will be prompted to create a new password.
5. Otherwise, Microsoft will tell you that one or more of those answers are incorrect and prompt you to try again.
Don’t worry if you can’t figure out the answers to your security questions. It happens to the best of us. If you created a password reset disk when you initially set up your local account, you’re in luck! You can use that to reset your forgotten Windows password.

1. Make sure that your reset disk drive is plugged in.
2. While in the security questions section, you’ll find a link that says ‘Use a password reset disk instead.’ Click on it.
3. The Password Reset Wizard will pop up to start the password recovery process. Click ‘Next.‘
4. Select the correct drive where your password reset disk is stored. Click ‘Next.‘
5. You can now create a new password for your account.

Michelle Rae Uy is the former Computing Reviews and Buying Guides Editor at TechRadar. She's a Los Angeles-based tech, travel and lifestyle writer covering a wide range of topics, from computing to the latest in green commutes to the best hiking trails. She's an ambivert who enjoys communing with nature and traveling for months at a time just as much as watching movies and playing sim games at home. That also means that she has a lot more avenues to explore in terms of understanding how tech can improve the different aspects of our lives.