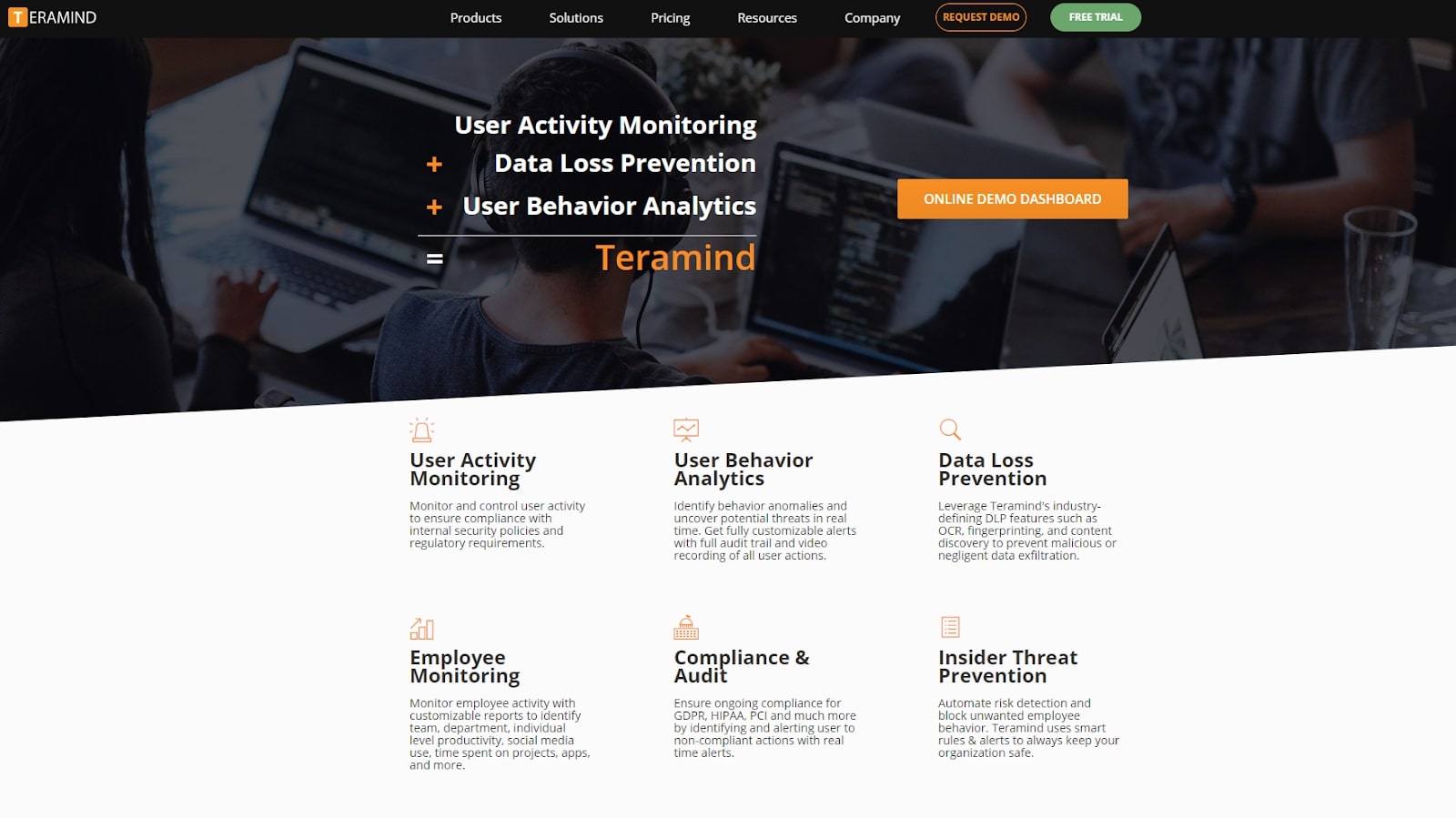
Teramind employee monitoring software
A comprehensive employee monitoring tool with automated policy rules
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Teramind is a comprehensive employee monitoring tool with user behavior analytics. After installing the agent software on all computers, everything your team does is monitored, from sending emails to posting on social media. Through the tools available in the customizable dashboard, you can identify threats to data compliance, productivity, and the security of sensitive data as they happen.
In our Teramind evaluation, we put the monitoring tool to the test to help you decide if it’s the best employee monitoring software for your business.
- Read our guide to our best employee monitoring software
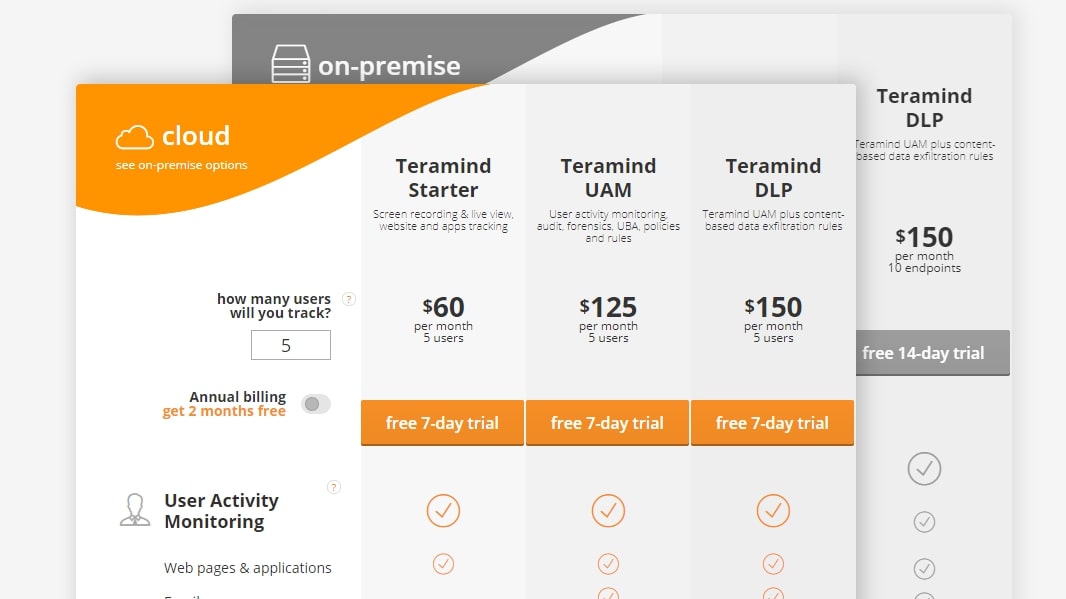
Plans and pricing
Teramind is available as either a cloud-based solution or an on-premise installation. For cloud-based Teramind, pricing is on a per-user basis, and there’s a minimum of five users. For an on-premise installation, pricing is based on the number of endpoints (computer workstations) you track and there’s a 10-endpoint minimum. All plans get two months for free when you pay annually instead of monthly.
The Teramind Starter plan costs $12/user/month (cloud-based) or $6/endpoint/month (on-premise). This includes monitoring of web pages and applications, instant messaging, social media activity, and web searches. You can control users’ computers remotely, block activities, analyze user activities for malicious or abusive behavior, and record video of all user activities. Productivity reports are available for each user.
The Teramind UAM plan costs $25/user/month (cloud-based) or $12.50/endpoint/month (on-premise). It adds monitoring of email, console commands, file transfers, keystrokes, and printing. You can use OCR to scan the images on users’ screens automatically, and view reports on the relative risk of each user’s activities.
Finally, the Teramind DLP plan costs $30/user/month (cloud-based) or $15/endpoint/month (on-premise). With this plan, you can set up content-based rules and file operation rules to prevent the malicious or negligent exfiltration of data. This ensures regulatory compliance with PII, PHI/HIPAA, and GDPR.
How it works
Teramind requires you to install monitoring software on all computers that you plan to monitor. You’ll be asked whether you want users to know that they are being monitored, as different software is installed if you want Teramind to be hidden completely. The hidden agent may require you to set exclusions in your antivirus program because some antivirus software can flag it as potentially malicious. Uninstalling the monitoring software requires the download of a removal tool from Teramind.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Teramind offers a free trial (seven days for the cloud-based solution, 14 days for an on-premise installation). There’s also an online demo where you can try out the administration dashboard of the software, with a 10-minute guided tour that takes you through its most interesting features. It’s a great way to familiarize yourself with Teramind’s extensive feature set.
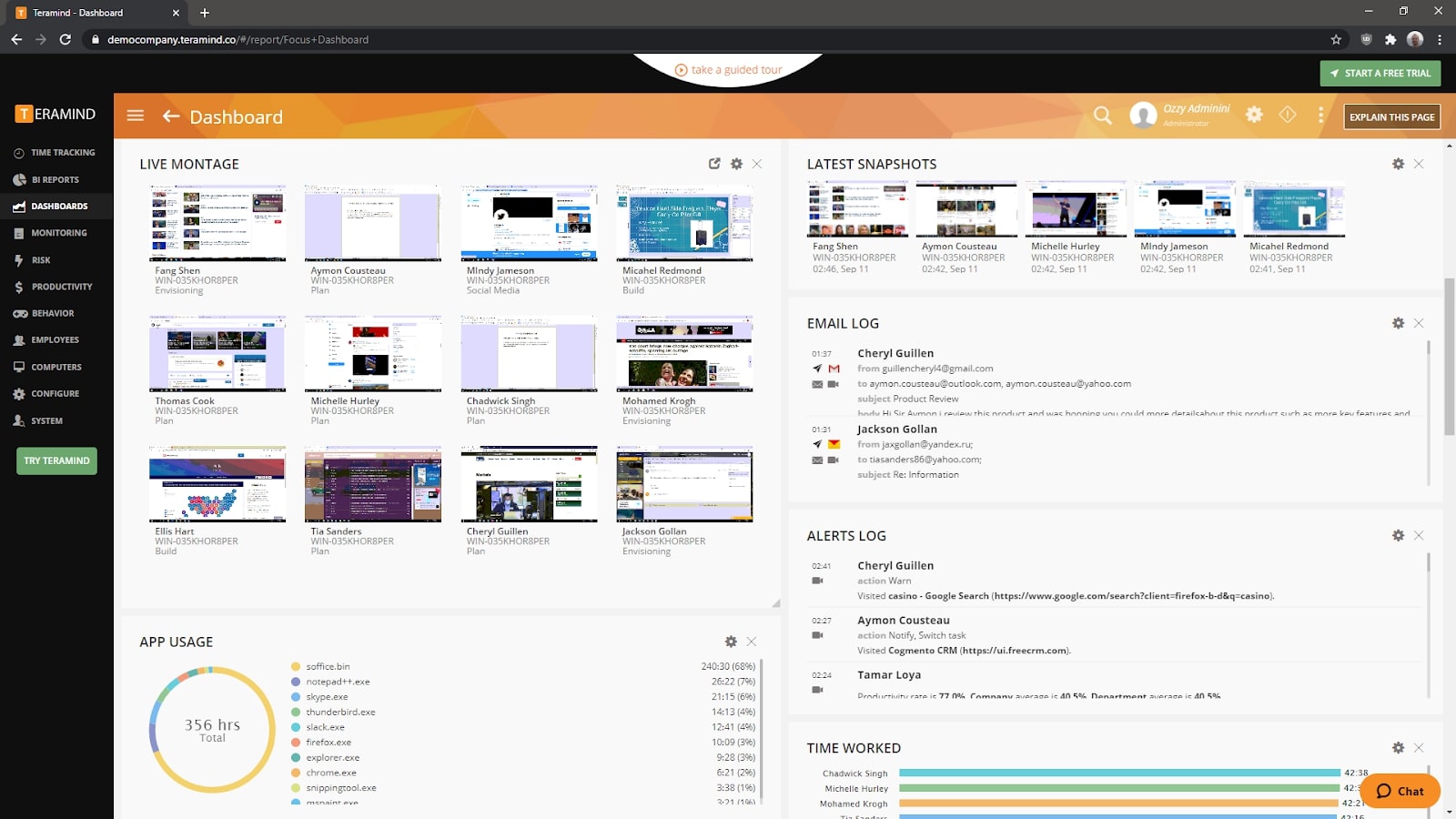
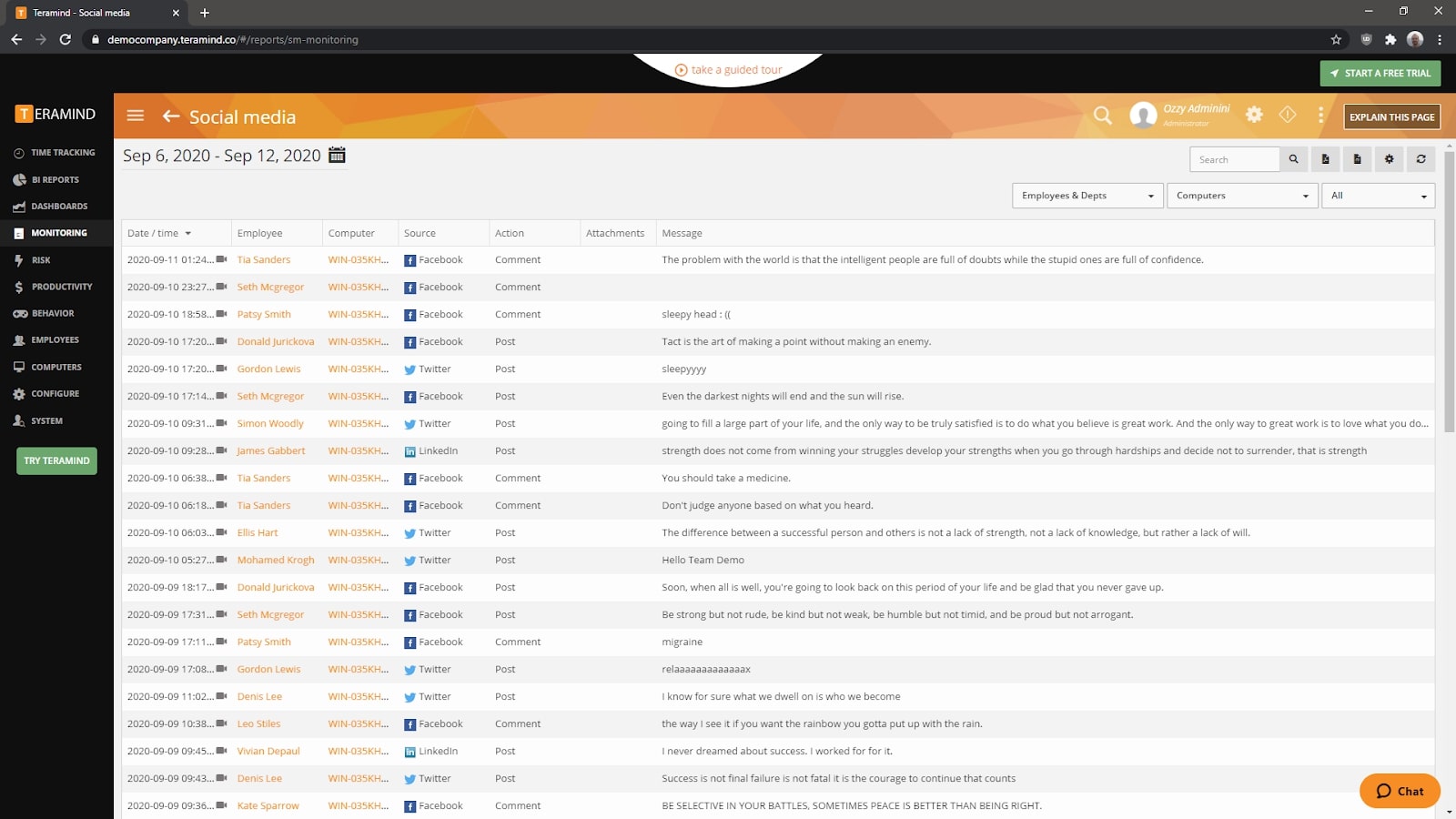
Features and services
Once you’ve logged into Teramind, you’ll be taken to the Focus Dashboard that summarizes your team’s activities. You can alter the Dashboard to suit your needs by adding or removing Widgets that show everything from keystroke logs to network usage.
Teramind has a full set of reports dedicated to time tracking. You can easily set up your own graphs and charts that show employee idle time. The Monitoring page has a long list of reports showing metrics such as web pages visited, emails sent, files transferred, instant messages sent, and even keystrokes made.
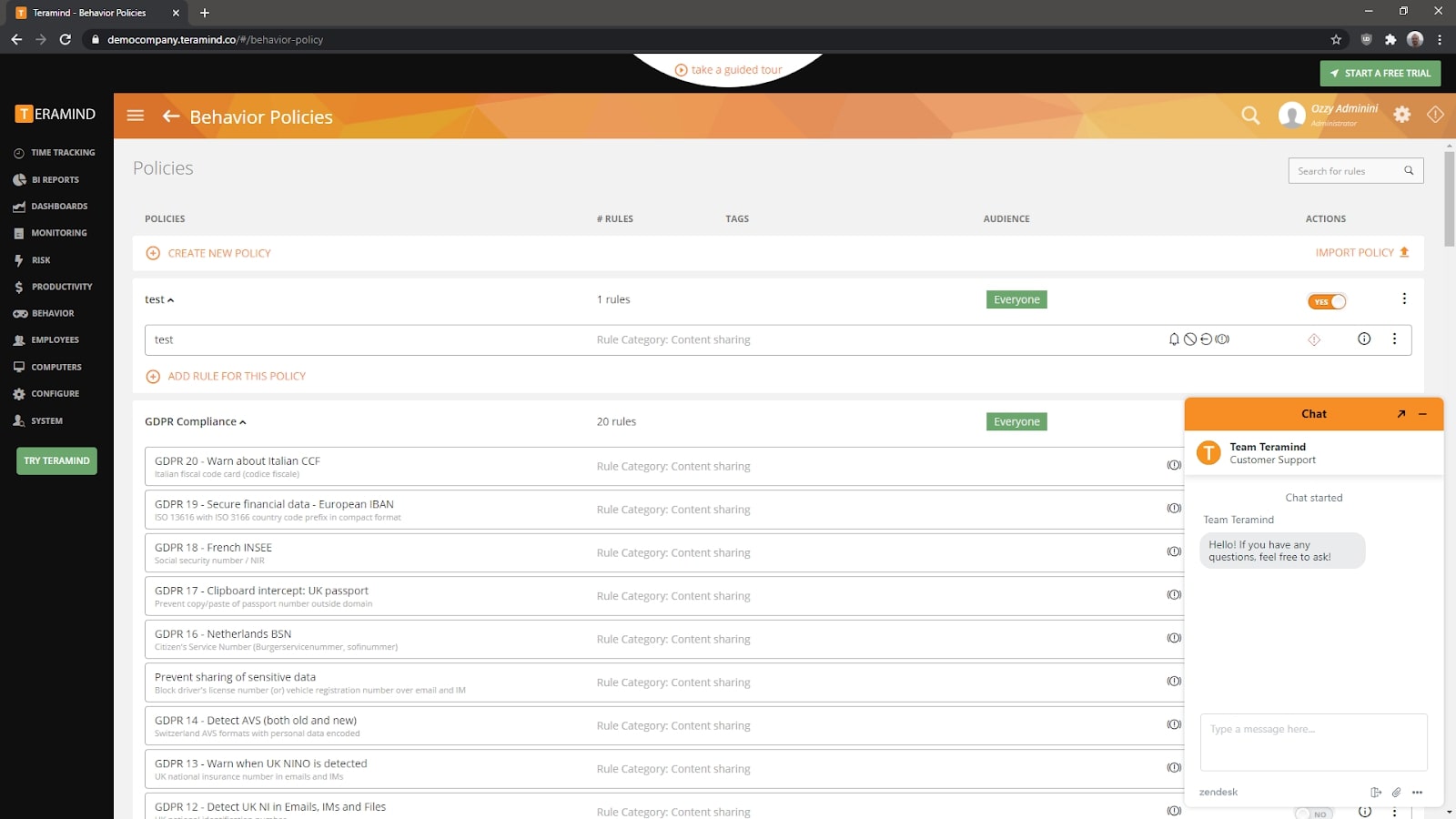
Usefully, Teramind also has automation and alerts. You can set up anomaly rules that trigger actions whenever an employee breaks them. There are hundreds of preset rules that you can build upon. Would you like to receive an email when an employee prints a document over 100 pages? Show a warning on the screen when an employee has been using social media for over 30 minutes? Block the sending of any email that contains certain inflammatory words? It’s all possible through the use of automation rules, one of Teramind’s most powerful features.
Support and customer care
Teramind has a comprehensive knowledge base, FAQ, and multiple user guides. Many of the guides are supported by helpful videos that take you step by step through the deployment and advanced configuration of the software.
You can email support directly or raise a support ticket from within the dashboard. There’s also 24/7 chat support and phone support, making for good all-around technical support. In our testing, the live chat support was instantaneous, and the agent we spoke to was courteous and knowledgeable.
The competition
If Teramind is too pricey, ActivTrak is a similar employee monitoring tool at a significantly lower price. You can run a basic plan for free, supporting up to three users. The Advanced plan, which is comparable to Teramind’s Starter plan, costs $7.20/user/month. However, ActivTrak cannot log keystrokes, the user interface is less polished, and there’s no OCR scanning of screenshots.
Another alternative to Teramind is Time Doctor. For starters, it’s cheaper, starting at $7/user/month. It lacks the in-depth reporting of Teramind and features such as remote control, email monitoring, and custom notifications, but if you’re mainly interested in employee time tracking, Time Doctor is a worthy choice.
Final verdict
It’s hard not to be impressed by Teramind as an employee monitoring tool. It enables you to access an almost overwhelming amount of information about what your team is doing. With the customizable dashboards, powerful automation, and excellent reporting tools, you can set up the software to give you the information you need and automatically correct malicious or harmful employee behavior.
Teramind’s responsive user interface and automated policy rules make it a top choice for employee monitoring, and once you’ve gotten over the learning curve, it excels as a remote monitoring tool.
Richard brings over 20 years of website development, SEO, and marketing to the table. A graduate in Computer Science, Richard has lectured in Java programming and has built software for companies including Samsung and ASDA. Now, he writes for TechRadar, Tom's Guide, PC Gamer, and Creative Bloq.
