TechRadar Verdict
Check Point Quantum Security Gateway is a high-level product which means it requires both a heavy financial and learning investment.
Pros
- +
Unified security management
- +
Threat detection capabilities
- +
Easy scaling
Cons
- -
Steep learning curve
Why you can trust TechRadar
Check Point’s new Quantum Security Gateway series is designed to deliver hardware-powered security to all client profiles, from a data center and an Internet of Things (IoT) operator to a small enterprise. It mostly plays its cards right, helping you keep various threat formats and actors at bay with the help of an end-to-end software-hardware platform and an array of both expected and custom technologies such as ThreatCloud and Maestro Hyper-scale.
Security features
Quantum Security Gateway is best approached as a security-themed package in which you get a firewall, antivirus and anti-bot tech, IPS, URL filtering, and application control. To deliver this, Quantum Security Gateway will rely on both hardware and software that make up the bulk of this neat package. Each gateway device will rely on robust hardware components that support both easy expansion and customization paired with modularity and flexibility.
The gateways will protect your organization against both cybersecurity threats while helping your filter network traffic and subject it to customized access policies. With them in place, you can block and restrict access to both applications and websites. In addition to these, you’ll get URL filtering, antivirus, and granular app and web controls, data loss prevention, and HTTPS control features.
This means that all network traffic will be subjected to TLS traffic inspection assisted with HTTPS classifications, interception of encrypted traffic, and subject-name-based verification. Every gateway utilizes Threat Prevention engines that handle both existing and incoming threats, with its anti-bot system relying on behavioral analysis of threats.
A TechRadar choice for top URL Filtering provider
Protect your employees and network from web-based threats with URL Filtering. Track web activity. Create custom filtering rules. Block malicious content. Secure your entire organization with just a few clicks with Perimeter 81. Radically simple. Get started today!
The gateways come with out-of-the-box support for the SandBlast Network sandbox that offers zero-day protection and a high level of resistance to attempts at evasion.
Recognizing that security should not come at the expense of productivity, Quantum Security Gateways will run all of your web and email downloads through their Threat Extraction engine and clean, rebuild and re-deliver the files in a seamless process.
ThreatCloud is Check Point’s response to the growing trend of using advanced analytics in building threat-resistant security models. In this case, the system will make use of a global network of sensors that feed the data on security risks to Check Point’s all-encompassing database.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Next, URL Filtering helps you modify access to websites down to the URL level. This means that you can restrict user access to avoid security breaches, just as you can erect barriers around any type of web content you deem unnecessary for the work process or unworthy of your precious bandwidth.
All web traffic segments can also be categorized in line with the URL category or the group of users and hardware it serves. For larger organizations, this feature will go a long way in having a clear overview of who is trying to access which website and when.
URL filtering goes hand in hand with the application control that allows your administrators to curb the usage of applications and widgets as well as sanitizes the sharing of data between the users in a larger system. At the same time, data loss prevention will keep the sensitive data safely within the confines of your network and prevent both unintentional and malicious data leakage.
To sweeten the deal, Check Point has made the Quantum Security Gateways Hyperscale-ready, meaning that they will chew whatever fast increase in traffic you throw at them. This will help you scale with the increased throughput of your network traffic while keeping the existing security levels intact.
Usability
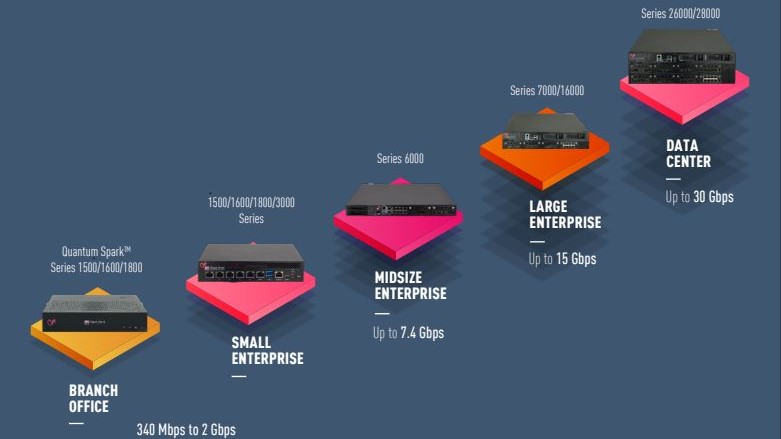
Based on their security properties, Quantum Security Gateways promise to meet the security needs of diverse user profiles. For starters, they will be a great addition to the organizations that manage distributed data centers, applications, and the workforce. Yes, the “distributed” is the name of the game here, as this attribute should no longer stand in the way of enjoying high-level security.
Apart from those that need to secure distributed assets, another ideal candidate for using the Quantum Security Gateways are enterprises that need to protect fast-paced workloads, robust data transfers, and mass backup systems. Also, if you can foresee an increase in your network capacities, Quantum’s Hyperscale feature will be a meaningful option to consider as part of your security projections.
Management features
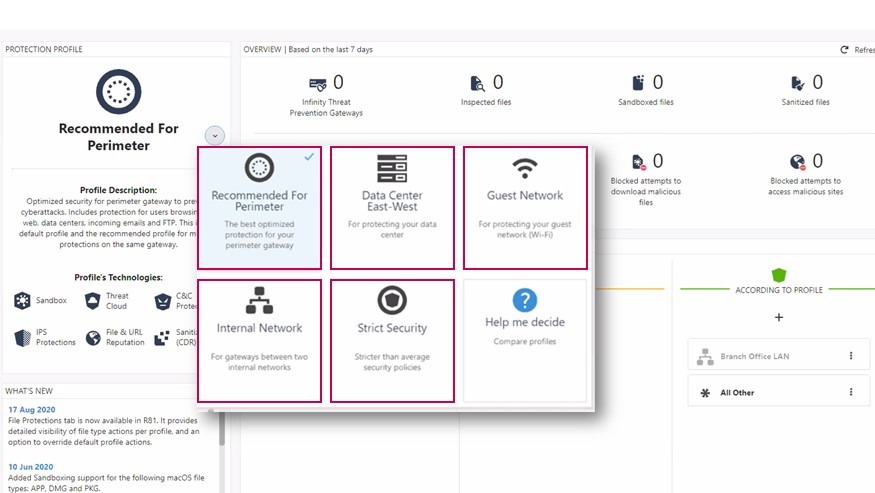
Check Point designed its Quantum Security Gateways in the recognition of the fact that the strength of one’s security system rests on the ability to effectively manage it. Event management is done via a SmartEvent feature that provides you with a single vantage point for observing and managing security risks, assisted by event investigation and real-time forensics and reporting.
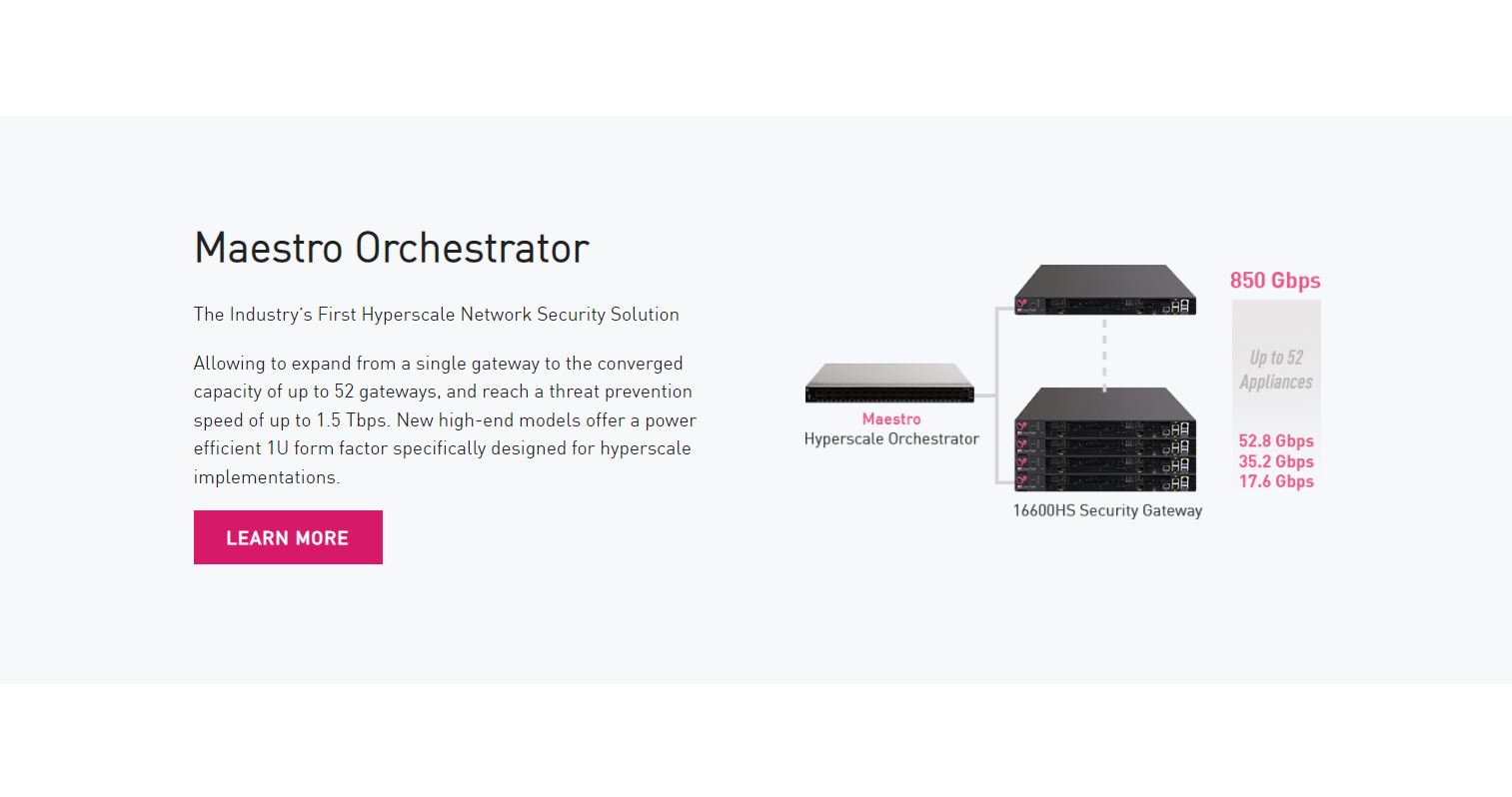
The unified security management approach gives you access to all networks, clouds, and the Internet of Things components while reducing the need for having dedicated security personnel for the related tasks. The umbrella security system at the top is the Maestro Orchestrator device which gives you control over all of your Quantum Security Gateways. What works for this approach apart from reduced overhead is the efficiency of its deployment support. By going for the automated and unified approach, you’ll have your Gateway-based perimeter up and running in no time.
The levels of access control and policy enforcement are managed with an easily scannable layer-based visual system which can be accessed via a central command window.
Still, this comes with a bit steeper learning curve compared to what is found with the competitors, so be prepared to deal with this in advance or bite the bullet once you acquire a gateway for you.
Pricing
Check Point is a bit more reticent when it comes to the pricing of its Gateways. It will simply direct you to schedule a demo to learn what it can do for you security-wise. Otherwise, you’ll be instructed to get in touch with the sales department to get a quote for a customized system in line with your specific needs.
Final verdict
Quantum Security Gateway offers a commendable unity of software and hardware in delivering robust protection against cyber-attacks of the latest generation. It will also scale seamlessly in any direction with your developing security needs, never losing sight of its unified-security philosophy capable of equally meeting the needs of smaller-scale organizations, data centers, or IoT systems. Despite its support for fast deployment, you should always bear in mind that this level of a professional approach to security takes both heavy financial and learning investment, so if security does not top your priority list, you can skip this one for a more accessible solution.
We've also highlighted the best URL filtering, best firewall and the best business VPN
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.